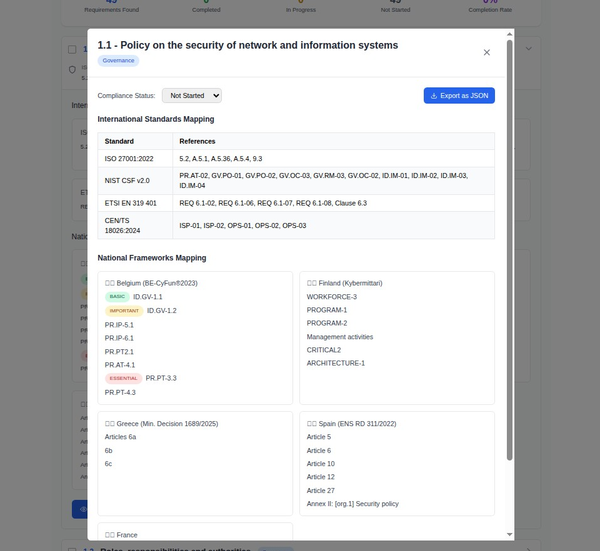
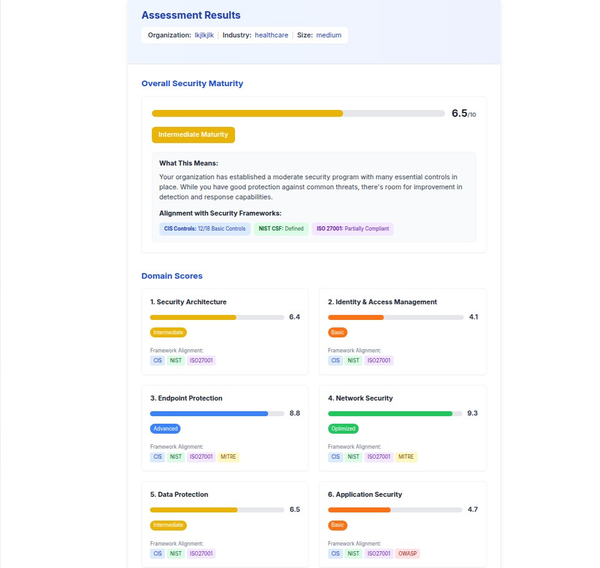
Navigating the AI Security Landscape: A Deep Dive into MITRE's SAFE-AI Framework for Compliance
The rapid integration of Artificial Intelligence (AI) into Information Technology (IT) systems is fundamentally changing how we approach cybersecurity. While AI offers transformative capabilities, it also introduces new vectors for adversarial actions that greatly expand the attack surface of IT systems. For cybersecurity and AI professionals tasked with securing information