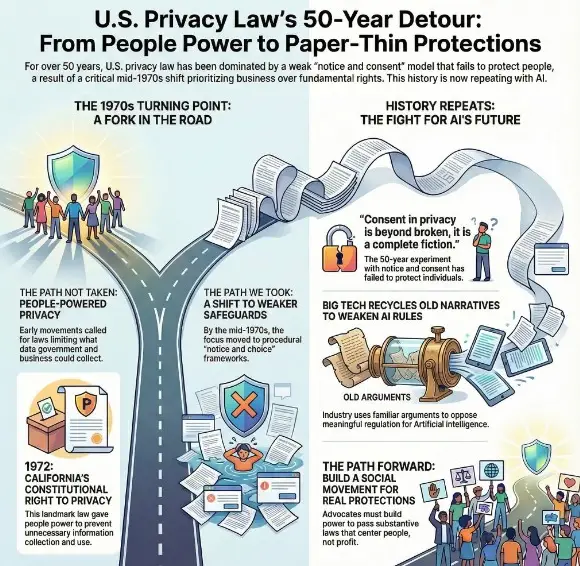
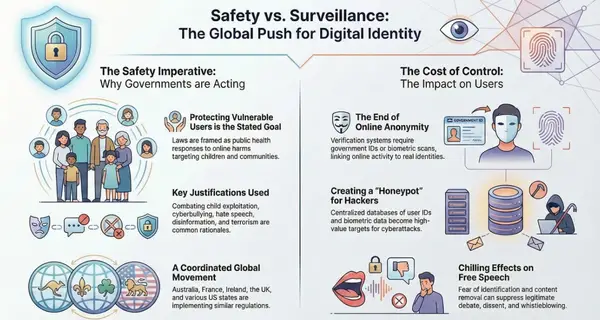
New Jersey Privacy Regulations in Limbo: What the Gubernatorial Transition Means for Your Compliance Program
Executive Summary The fate of New Jersey's proposed privacy regulations implementing the New Jersey Data Privacy Act (NJDPA) now rests with incoming Governor Mikie Sherrill's administration. With the Murphy administration failing to adopt the rules before the January 8 deadline, businesses face continued uncertainty about specific