The Silent Revolution: How Wireless Body Area Networks Are Transforming Human Surveillance Under the Guise of Healthcare
An investigation into the deployment of in-body monitoring systems, the COVID-19 catalyst, and the World Economic Forum's vision of "hackable humans"
Introduction: Beyond the Skin's Boundary
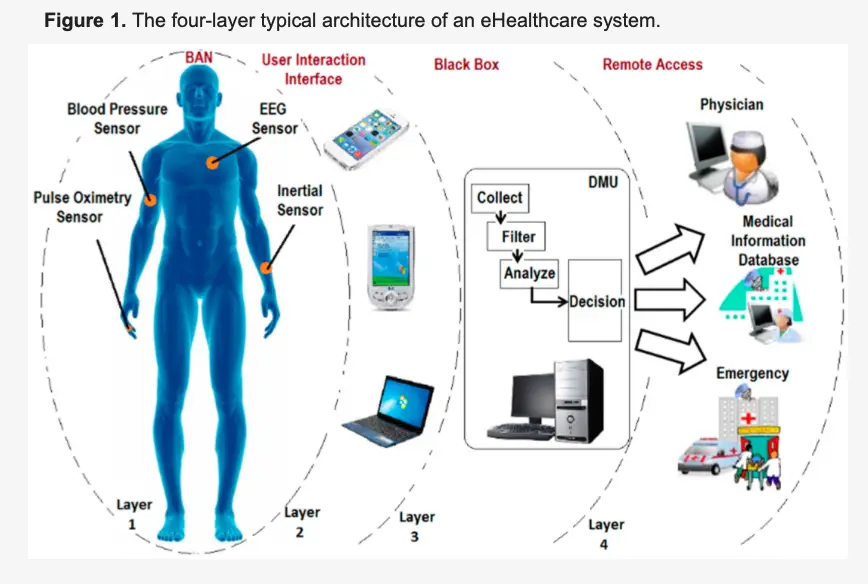
We stand at an unprecedented crossroads in human history, where the boundary between our physical bodies and digital surveillance systems is dissolving. While most people focus on external privacy concerns—smartphones tracking location, social media monitoring behavior—a far more invasive infrastructure is being quietly deployed: Wireless Body Area Networks (WBANs) that monitor, collect, and transmit data from inside the human body itself.

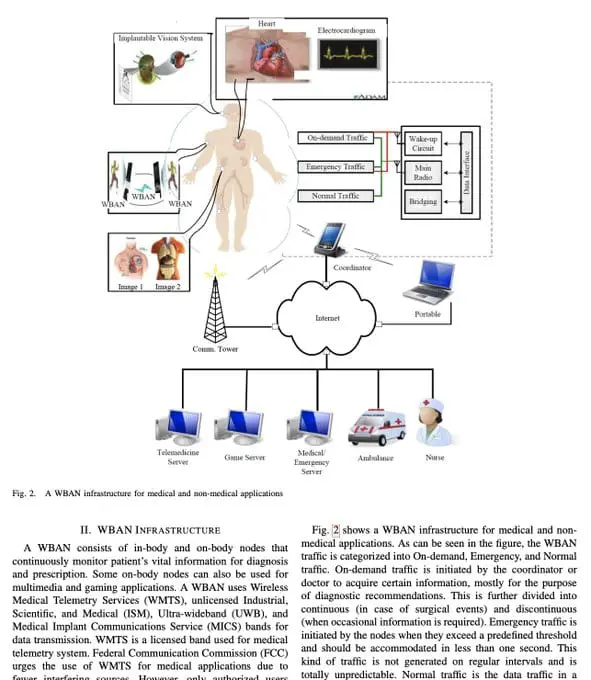
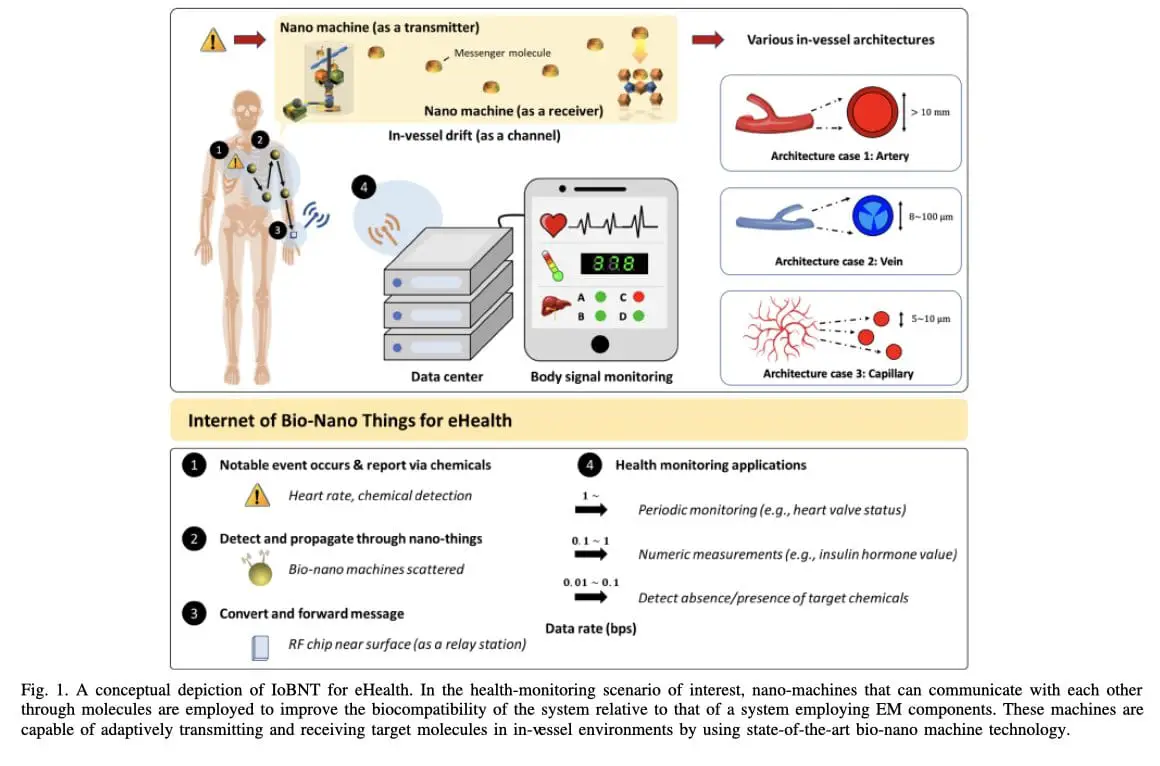
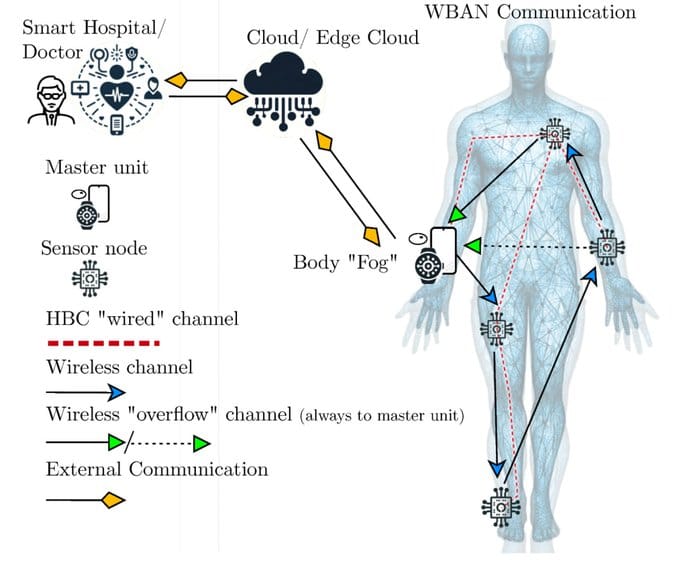
This isn't science fiction. It's current reality, accelerated by COVID-19 and championed by influential figures like World Economic Forum advisor Yuval Noah Harari, who openly states that "humans are now hackable animals" and "surveillance is going under the skin".
The implications extend far beyond healthcare. We're witnessing the construction of a surveillance apparatus that operates at the cellular level, with profound consequences for human autonomy, privacy, and the very nature of what it means to be human in the 21st century.

The Technology Framework: Understanding WBANs
What Are Wireless Body Area Networks?
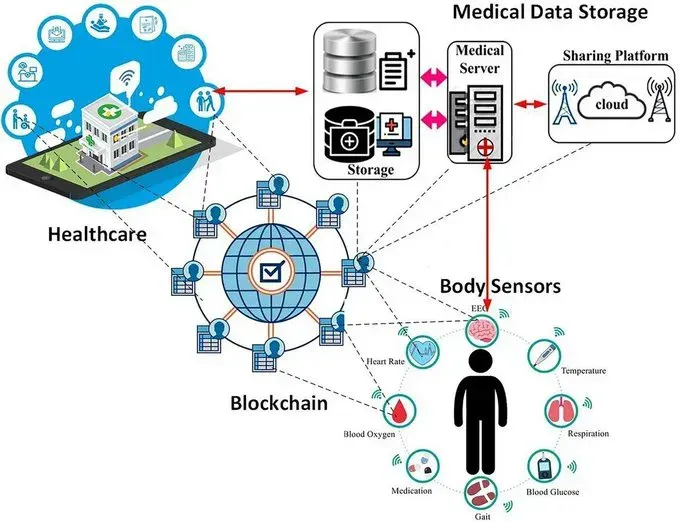
Wireless Body Area Networks represent "a wireless network of wearable computing devices" that can be "embedded inside the body as implants or pills, surface-mounted on the body in a fixed position, or carried in different positions". These systems create what researchers call a "body sensor network" capable of continuous physiological monitoring.
The technology encompasses three primary categories:
1. Implantable Devices: Surgically placed sensors that "monitor heart function, detect abnormal heart rhythms," and perform various sensing functions from inside the body
2. Ingestible Devices: Sensors that "resemble regular capsules and can be swallowed similarly to normal pills"
3. Injectable Devices: Microdevices "placed inside the human body via needles" for "sensing and neuro-stimulation"
The Communication Infrastructure
The sophistication of these networks extends far beyond simple monitoring. WBANs feature "a standard ZigBee compliant radio and a common set of physiological, kinetic, and environmental sensors" that can "perform real-time analysis of sensors' data, provide guidance and feedback to the user, and generate warnings".
More concerning is their connectivity: "Through gateway devices, it is possible to connect the wearable devices on the human body to the internet. This way, medical professionals can access patient data online using the internet independent of the patient location".
This creates a pathway not just for medical monitoring, but for unprecedented surveillance capabilities that operate beyond traditional privacy protections.

COVID-19: The Perfect Storm for Implementation
The Coronavirus-Body Area Network (CoV-BAN) Model
The COVID-19 pandemic served as more than a health crisis—it became the justification for rapid deployment of invasive monitoring technologies. Researchers developed what they explicitly called the "coronavirus-body area network (CoV-BAN) model based on IoT technology as a real-time health monitoring system for the detection of the early stages of coronavirus infection".
This system was designed to:
- Use "machine learning and the Internet of Things (IoT) to identify and monitor the human body for health-related information"
- Employ "wearable biosensors to examine the health status of the patient"
- Enable "continuous monitoring of COVID-19 infected persons"
Technical Implementation During the Pandemic
The CoV-BAN model incorporated sophisticated surveillance capabilities:
Multi-Sensor Integration: "Wearable or implanted biosensors (ECG, EEG, temperature, blood pressure) capture data through ZigBee and Bluetooth wireless technologies and transmit it to the body coordinator"
Cloud-Based Monitoring: The system uses "long-range (LoRa)-based IoT program to receive biosensor signals from the patient and transmit them to the cloud directly for monitoring"
Remote Healthcare Access: "Using the Internet, the sink nodes transfer the gathered data to a distant medical facility or doctor"
The Normalization Strategy
COVID-19 provided the perfect cover for normalizing invasive monitoring. As researchers noted, "To prevent coronavirus disease 2019 (COVID-19) from spreading, the regular identification and monitoring of infected patients are needed". This created public acceptance for technologies that would have faced significant resistance under normal circumstances.
The pandemic established the precedent that public health emergencies justify extraordinary surveillance measures, setting the stage for permanent implementation of these systems.
The World Economic Forum's Vision: "Hacking Humans"
Yuval Noah Harari's Explicit Agenda
World Economic Forum advisor Yuval Noah Harari has been remarkably candid about the surveillance agenda. His statements reveal a comprehensive vision for human monitoring and control:
On Human "Hackability": "Humans are now hackable animals"
On Under-the-Skin Surveillance: "Previously, surveillance was mainly above the skin; now we want it under the skin"
On COVID as Justification: "COVID is critical because this is what convinces people to accept, to legitimize, total biometric surveillance. If we want to stop this epidemic, we need not just to monitor people, we need to monitor what's happening under their skin"
The Economic Transformation
Harari's vision extends beyond surveillance to economic control. He explains that future generations will "learn how to engineer bodies and brains and minds," which will become "the main products of the 21st Century economy: not textiles and vehicles and weapons, but bodies and brains and minds".
This represents a fundamental shift where human biology becomes a commodity, controlled and manipulated by those who own the technology infrastructure.
Data as the New Currency
According to Harari, "data is the most important asset in the world," and "the few masters of the economy" will be "the people who own and control data". When this data includes real-time biological information from inside human bodies, the implications for power and control become staggering.

The Technical Reality: How In-Body Surveillance Works
Intrabody Communication Systems
The technology for "under the skin" surveillance is already operational. Research demonstrates that "the conductive properties of the body can be used to enable wireless communication with implanted devices".
Galvanic Communication: "Galvanic intrabody communication has been studied for a range of medical applications including communicating with implanted and surface-mounted devices"
Signal Transmission: These systems can "send signals from an implanted device to electrodes on the skin," enabling "easy placement and repositioning of skin electrodes to improve signal quality"
Biomedical Telemetry Infrastructure
The monitoring infrastructure extends far beyond individual devices. "Biotelemetry involves the application of telemetry in biology, medicine, and other health care to remotely monitor various vital signs of ambulatory patients".
Dedicated Frequency Allocations: "The Federal Communications Commission (FCC) has recently begun to allocate dedicated frequency bands for exclusive biotelemetry usage, for example, the Wireless Medical Telemetry Service (WMTS)"
This represents a systematic infrastructure development that goes far beyond emergency pandemic response.
The Device Ecosystem
Current implantable and injectable devices include:
Miniaturized Sensors: "Miniaturized wireless biomedical devices have gained increasing popularity" and can "sense certain physiological parameters, collect sensitive information, transmit it to a detector"
Multi-Functional Capabilities: These devices can perform "sensing and neuro-stimulation" and even "affect the human body through stimulation and drug delivery"
The technology already exists for devices that not only monitor but can influence human physiology remotely.
Healthcare Privacy Risks: A Critical Gap in Protection
For more information about healthcare data vulnerabilities, visit HIPAA Security Health
The HIPAA Illusion
While patients assume their medical data is protected under HIPAA regulations, the reality of WBAN technology creates unprecedented vulnerabilities:
Third-Party Access: "Considerable effort would be required to make WBAN transmission secure and accurate" and "little study has been done in this area for WBANs"
Data Sharing Limitations: "As WBANs are resource-constrained in terms of power, memory, communication rate and computational capability, security solutions proposed for other networks may not be applicable to WBANs"
Insurance and Employer Access: The continuous stream of biological data creates new categories of information that may not be covered by existing privacy protections, potentially accessible to insurance companies, employers, and government agencies.
Digital Twin Technology Risks
Learn more about emerging digital identity threats at Digital Twin Risk Health
WBAN technology enables the creation of comprehensive "digital twins"—virtual replicas of individuals based on continuous biological monitoring. These digital models can:
- Predict health outcomes and behaviors
- Enable manipulation through targeted interventions
- Create permanent surveillance profiles that persist beyond individual control
- Facilitate social credit systems based on biological compliance
Device Security Vulnerabilities
Explore medical device cybersecurity concerns at Device Risk Health
The Cybersecurity Crisis
Medical devices, including WBAN components, face severe security challenges:
Insufficient Security Design: "Security is a high priority in most networks, little study has been done in this area for WBANs"
Remote Access Vulnerabilities: The ability for external systems to access real-time biological data creates unprecedented attack surfaces for malicious actors
Update and Maintenance Challenges: Implanted devices may operate for years without security updates, creating persistent vulnerabilities
The Hacking Reality
When Harari describes humans as "hackable animals," this isn't metaphorical. The technical infrastructure makes it possible for external parties to:
- Monitor real-time physiological responses
- Influence behavior through targeted stimulation
- Collect continuous biological data for analysis and prediction
- Potentially manipulate device functions remotely
The Surveillance Infrastructure: Who Has Access?
Healthcare System Integration
WBAN systems use "licensed wireless medical telemetry services (WMTS)" and connect to "telemedicine systems through faster network connectivity for processing and analysis". This creates multiple access points for data collection and monitoring.

Government and Corporate Access
The integration with internet infrastructure means that data flows through systems potentially accessible to:
- Government Agencies: National security and public health authorities
- Insurance Companies: For risk assessment and premium determination
- Employers: Particularly in healthcare and high-risk industries
- Technology Companies: Providing the infrastructure and analytics platforms
- Research Institutions: Collecting population-level health data
The Consent Problem
Most individuals receiving medical care are not informed about the extent of data collection and sharing enabled by these systems. The complexity of the technology infrastructure makes meaningful consent nearly impossible.
Why Healthcare Providers Stay Silent
Limited Technical Understanding
Research shows "there is an enormous disparity between the number of published articles in English dealing with these devices and their actual use in clinical settings". Many healthcare providers lack comprehensive understanding of the surveillance capabilities they're implementing.
Economic Incentives
Healthcare systems face financial pressures that make technology adoption attractive:
- Remote monitoring reduces staffing costs
- Continuous data collection supports value-based care models
- Technology companies provide financial incentives for adoption
Professional Liability Concerns
Healthcare providers may avoid discussing surveillance implications to prevent:
- Patient anxiety and treatment refusal
- Legal liability for privacy violations
- Professional sanctions for discouraging "beneficial" technologies
The Broader Implications: A New Form of Human Control
Beyond Healthcare
While marketed as healthcare technology, WBAN systems create infrastructure for comprehensive human monitoring and control that extends far beyond medical applications:
Behavioral Monitoring: Real-time physiological data reveals emotional states, stress responses, and behavioral patterns
Social Control: Continuous monitoring enables social credit systems based on biological compliance
Economic Manipulation: Access to physiological data enables targeted marketing and economic pressure based on biological vulnerabilities
The Transformation of Human Agency
The implementation of WBAN technology represents a fundamental shift in the relationship between individuals and systems of power. When external entities can monitor and potentially influence human biology in real-time, traditional concepts of privacy, autonomy, and consent become obsolete.
Resistance and Protection Strategies
Individual Actions
Medical Consent Awareness: Demand detailed explanations of all monitoring technologies and data sharing practices
Device Disclosure: Require complete information about any implantable or wearable devices, including communication capabilities
Privacy Rights: Assert rights to data control and deletion where legally possible
Systemic Changes Needed
Regulatory Reform: Expand privacy protections to cover continuous biological monitoring
Transparency Requirements: Mandate clear disclosure of all surveillance capabilities
Consent Standards: Establish meaningful consent standards for biological data collection
Security Standards: Implement robust cybersecurity requirements for medical devices
Conclusion: The Choice Before Us
The deployment of Wireless Body Area Networks represents more than a technological advancement—it's a fundamental transformation of human existence. Under the guise of healthcare improvement, we're witnessing the construction of a surveillance infrastructure that operates at the most intimate level of human biology.
Yuval Noah Harari's candid statements about "hacking humans" and surveillance "under the skin" should be understood as fair warning of the agenda being implemented. COVID-19 provided the crisis necessary to accelerate deployment and normalize acceptance of invasive monitoring technologies.
The choice before us is stark: accept the transformation of human beings into monitored, controlled biological assets, or demand transparency, consent, and protection of fundamental human autonomy.
This isn't a distant future scenario—it's happening now. The infrastructure is being deployed, the data is being collected, and the control systems are being established. The question is not whether this technology exists, but whether we'll allow it to be implemented without our knowledge or meaningful consent.
The battle for human autonomy in the digital age is being fought not in the abstract realm of data privacy, but in the most intimate space of all—inside our own bodies. Understanding this reality is the first step toward protecting what remains of human freedom in an increasingly monitored world.
For more information about protecting yourself from healthcare surveillance and privacy risks, visit:
- HIPAA Security Health - Understanding healthcare data protection
- Digital Twin Risk Health - Digital identity and surveillance concerns
- Device Risk Health - Medical device cybersecurity threats
Sources: This analysis is based on peer-reviewed research from major medical and technology journals, including publications from the National Center for Biotechnology Information, IEEE, Nature, and official statements from World Economic Forum advisors. All claims are supported by documented evidence from published scientific literature and public statements by key proponents of these technologies.








