HIPAA and HITECH: A Deep Dive into Protecting Health Information in the Digital Age

This in-depth article will explore the key takeaways from your podcast episode on HIPAA and HITECH, drawing upon the insights and analysis presented.
Introduction
The podcast episode, provides a comprehensive overview of HIPAA and HITECH, starting with the historical context of HIPAA's enactment in 1996. The episode emphasizes that these regulations impact everyone, not just healthcare professionals, as they govern the protection of sensitive health data in an increasingly digital world.

HIPAA: Setting the Stage for Healthcare Data Privacy
Enacted in 1996, HIPAA primarily aimed to combat fraud and waste in healthcare, focusing on paper records prevalent at the time. However, the rapid evolution of technology, particularly the internet and smartphones, necessitated a more comprehensive approach to data security.
HITECH: Ushering Healthcare Data into the Digital Age
The HITECH Act of 2009 emerged as a response to the technological advancements transforming healthcare. This act incentivized the adoption of electronic health records (EHRs) while strengthening HIPAA's provisions for the digital age.
Expanding the Scope of Protection
One of HITECH's significant contributions was broadening the definition of protected health information (PHI). Previously limited to medical charts, PHI now encompasses any identifiable health-related information, including mental health, payment details, and even genetic data. This expansion underscores the extensive reach of these regulations in safeguarding sensitive personal information.

Business Associates: A New Frontier in HIPAA Compliance
HITECH significantly impacted businesses handling PHI, extending its reach beyond traditional healthcare providers. Now, any entity interacting with PHI, such as appointment scheduling tech companies or cloud service providers, is considered a "business associate" and must comply with HIPAA and HITECH.
Key Compliance Requirements for Business Associates
- Business Associate Agreements (BAAs): These legally binding contracts between covered entities (e.g., doctor's offices) and business associates outline each party's responsibilities in protecting PHI. These agreements go beyond informal arrangements, establishing a formal commitment to data security.
- Encryption: HITECH mandates stricter encryption standards for business associates, requiring them to "scramble" data into an unreadable format without the proper decryption key. This safeguards data both at rest (stored on servers) and in transit (during electronic transmission).
- Documentation and Proof of Compliance: Business associates must demonstrate their adherence to HIPAA and HITECH through documented policies, procedures, and security measures. This shift emphasizes accountability and transparency in data protection practices.

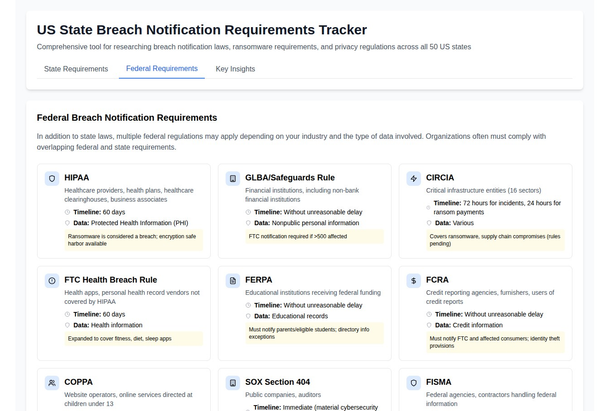
Breach Notification: A Critical Aspect of HIPAA and HITECH
A breach, defined as unauthorized access or disclosure of PHI, can occur through various means, including hacking, device theft, or even human error like sending an email to the wrong recipient. The HITECH Breach Notification Rule mandates notifying affected individuals and the Department of Health and Human Services (HHS) within 60 days of discovering a breach. These notifications must include specific details about the breach, potential risks, and steps individuals can take to protect themselves.

Penalties for Non-Compliance
The podcast episode emphasizes that non-compliance with HIPAA and HITECH carries serious consequences, including hefty fines and potential criminal charges. These penalties underscore the importance of taking these regulations seriously.
The Bigger Picture: Enabling a Patient-Centered Healthcare System
Beyond avoiding penalties, the ultimate goal of HITECH is to leverage technology for a more connected and patient-centric healthcare system. Envisioning a future where medical records are securely accessible with consent, HITECH paves the way for improved care coordination and patient empowerment.

Conclusion
HIPAA and HITECH play a crucial role in navigating the complex landscape of health information privacy and security in our digital age. The podcast episode effectively breaks down these regulations, providing listeners with the knowledge and tools to become responsible stewards of sensitive health data. By understanding and implementing the guidelines outlined in HIPAA and HITECH, we can collectively work towards a healthcare system that prioritizes both innovation and patient privacy.