Cybersecurity in Construction and the Role of IoT in Equipment

Introduction
As construction sites grow increasingly connected—hosting drones, sensors, autonomous vehicles, and other smart devices—cybersecurity has emerged as a critical priority. Today’s construction projects demand not only the efficient coordination of labor and resources but also the secure management of a complex, digital ecosystem. From blueprints to heavy machinery, cyber threats can affect every layer of a construction project, potentially leading to project delays, financial losses, or even safety hazards.

In this article, we’ll delve into why cybersecurity matters in construction, explore how IoT-enabled equipment is reshaping worksites, identify key cyber challenges, and outline strategies to keep operations secure in an era of connected machinery.

1. Why Cybersecurity Matters in Construction
1.1 Increasing Digitalization
Modern construction sites are no longer simple arrays of bricks and mortar. They feature:
- Drones used for aerial site surveys and progress monitoring.
- Sensors that track temperature, humidity, vibration, and other environmental factors in real time.
- Autonomous vehicles and robotics that handle repetitive or hazardous tasks.
- On-site management platforms integrating multiple data streams to provide actionable insights.
All these systems communicate wirelessly, often sending critical data to cloud-based platforms. While this connectivity streamlines operations and offers real-time insights, it expands the attack surface for cyber criminals who could exploit unprotected devices or networks.
1.2 Critical Infrastructure
Many construction projects directly support vital infrastructure such as roads, bridges, tunnels, and public buildings. A successful cyberattack against these projects can have far-reaching consequences:
- Service disruptions (e.g., blocked roadways, compromised utilities).
- Project delays that can escalate costs and stall public benefits.
- Safety hazards if systems that control cranes or heavy vehicles are tampered with.
In some cases, cyberattacks on construction sites for critical infrastructure could even be considered a matter of national security, prompting heavier scrutiny from governments and regulators.
1.3 Financial & Safety Risks
Breaches can lead to:
- Project Delays & Cost Overruns: Ransomware or data theft can halt work and disrupt supply chains.
- Loss of Sensitive Data: Proprietary information such as design blueprints, bidding documents, or intellectual property can be stolen and sold or leaked.
- Compromised Safety Systems: Unsecured machinery with connected features may be commandeered or sabotaged, endangering workers and the public.
A robust cybersecurity posture is therefore essential to protect both productivity and safety on construction sites.

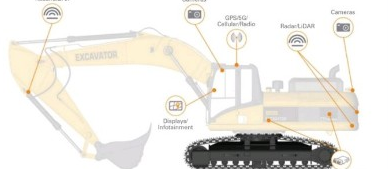
2. IoT in Construction Equipment
2.1 Connected Machinery
Today’s heavy equipment—excavators, bulldozers, cranes, loaders—often comes sensor-equipped to monitor:
- Performance metrics (engine load, hydraulic pressure, temperature).
- Usage data (operator hours, fuel consumption).
- Maintenance status (predictive analytics based on part wear and tear).
Connectivity enables proactive maintenance (e.g., scheduling repairs before failures occur) and more efficient job planning. However, every sensor and network interface introduces a potential entry point for cyber adversaries.
2.2 Remote Monitoring & Control
Over-the-air (OTA) updates and remote diagnostics have revolutionized equipment maintenance:
- Quick Fixes & Firmware Updates: Technicians can resolve software bugs or performance issues without physically visiting the site.
- Fleet Management: Centralized dashboards allow site managers to track multiple machines across locations, monitoring fuel usage, idle times, and productivity.
While remote connectivity can save time and money, it also raises concerns about unauthorized access or malicious firmware tampering. A cyber criminal who gains control of heavy machinery could cause accidents or extort a company by halting operations.
2.3 Data-Driven Insights
Construction firms are increasingly leveraging data analytics to optimize operations:
- Fuel Consumption & Efficiency: Identifying patterns to reduce costs and carbon footprint.
- Predictive Maintenance: Scheduling repairs before catastrophic failure to minimize downtime.
- Real-Time Decision-Making: Adjusting workflows on the fly based on sensor data.
However, if data streams are intercepted or manipulated, the resulting misinformation can lead to poor decision-making, unnecessary expenses, or safety incidents.

3. Key Cybersecurity Challenges
3.1 Legacy Equipment & Software
- Older Machinery: Many companies still rely on older or proprietary control systems. These may not have been designed with cybersecurity in mind and can be difficult (or impossible) to patch.
- Integration Complexities: Mixing legacy systems with new IoT-driven solutions can create unexpected vulnerabilities, as older components might not support modern encryption or secure protocols.
3.2 Supply Chain Risks
- Multiple Vendors: Construction equipment often sources components from a variety of suppliers. A vulnerability in one small component can compromise an entire machine.
- Third-Party Software: Some systems rely on external software libraries or subcontractor code, which could have hidden backdoors or unpatched vulnerabilities.
A single weak link in the supply chain can open the door to larger cybersecurity breaches across the network.
3.3 Physical Security Overlaps
- Unattended Devices: Construction sites are expansive, and workers may leave devices or vehicles unattended, making them physically accessible to unauthorized personnel.
- Temporary Networks: Many on-site networks are ad hoc or temporary, lacking the robust security controls typical of permanent corporate networks.
- Converged Threats: A compromised on-site device could provide attackers with a foothold to escalate into larger corporate or cloud systems.
4. Strategies for Mitigating Cyber Threats
4.1 Risk Assessment & Standardization
- Adopt Industry Standards: While ISO 21434 is geared toward automotive cybersecurity and ISO 24882 is emerging for agricultural machinery, these types of standards offer frameworks that can be adapted for construction equipment.
- Formal Security Assessments: Conduct threat modeling to identify your most critical systems and data. Develop a systematic risk management plan that informs all stages of equipment design, deployment, and maintenance.
4.2 Secure Network Architectures
- Network Segmentation: Separate critical operational systems (e.g., crane controls) from less secure networks (e.g., on-site Wi-Fi for employees or visitors).
- Encryption & VPNs: Secure remote connections and data in transit with strong encryption protocols (e.g., TLS, VPN tunnels).
- Zero-Trust Approach: Establish strict access policies so that even devices within the same network must authenticate and be authorized to communicate.
4.3 Firmware & Software Updates
- Regular Patching: Keep firmware, operating systems, and control software up to date.
- Verified Updates Only: Implement cryptographic signing for updates to ensure they are authentic and untampered.
- Automated Patch Management: Deploy tools that regularly check for new patches and systematically install them to minimize vulnerabilities.
4.4 Training & Awareness
- Operator Training: Ensure equipment operators understand basic cyber hygiene (e.g., using strong, unique passwords, recognizing phishing attempts).
- Site Managers & IT/OT Staff: Provide more in-depth training on network security, incident response, and secure device management.
- Ongoing Education: Cyber threats evolve. Continuous refreshers and updated protocols are essential to keep pace with new attack methods.
4.5 Collaboration with Suppliers
- Vendor Security Requirements: Communicate clear cybersecurity standards to equipment manufacturers and software suppliers.
- Joint Patch Management: Have a formal process for reporting, patching, and validating vulnerabilities discovered in third-party components.
- Transparency & Accountability: Push for greater visibility into vendor security practices, from design to lifecycle management.
5. Emerging Trends
5.1 Autonomous Equipment & Robotics
As more tasks become automated:
- Machine Decision-Making: Algorithms guide heavy machinery, and hacking these decision systems could lead to catastrophic accidents.
- Sensor Integrity: Attackers might feed false data to sensors (GPS spoofing, for instance), causing equipment to operate erratically.
5.2 Edge Computing & 5G
- Lower Latency, Higher Bandwidth: 5G networks and edge computing bring powerful real-time capabilities to job sites, but also new threat vectors due to increased connectivity points.
- Secure Edge Infrastructure: Protecting computing nodes placed in the field is more challenging than securing a centralized data center.
5.3 Regulatory Landscape
- Automotive-Inspired Cyber Rules: Regulations such as UNECE WP.29 for vehicles might set a precedent for construction equipment cybersecurity requirements.
- Global Harmonization: Different regions may introduce their own rules, potentially leading to standardization or, conversely, patchwork regulations that firms must navigate.
6. Conclusion
Cybersecurity has become an essential consideration for construction projects of all sizes. With IoT-enabled equipment on-site—be it drones, sensors, or connected heavy machinery—robust cyber defenses are vital to protect operations, intellectual property, and the well-being of workers. A strategic combination of industry-standard frameworks, network protections, regular updates, employee training, and vendor collaboration can help construction firms stay ahead of the ever-evolving cyber threat landscape.
By embracing cybersecurity best practices, construction companies can fully realize the benefits of digital transformation—such as greater efficiency, lower costs, and improved safety—without compromising the security and integrity of their projects.
Key Takeaways
- Cybersecurity Risks Are Real: Connected construction sites face threats ranging from data theft to potential sabotage of critical machinery.
- IoT in Equipment Brings New Vulnerabilities: Remote monitoring, predictive maintenance, and data-driven insights deliver efficiency gains but require proactive defense strategies.
- Legacy Systems Compound Risks: Older equipment and fragmented supply chains often lack modern security features, creating exploitable gaps.
- Defense in Depth: Focus on strong network architectures, secure firmware practices, staff training, and robust supplier relationships to build layered security.
- Future Trends Demand Action: Autonomous machinery, 5G connectivity, and evolving regulations will drive even greater need for cybersecurity measures.
With the right mix of technology, policy, and training, the construction industry can securely harness IoT and connected equipment, delivering safer, faster, and more efficient projects for the modern world.