What's The Fine For a Hospital Getting Ransomware?

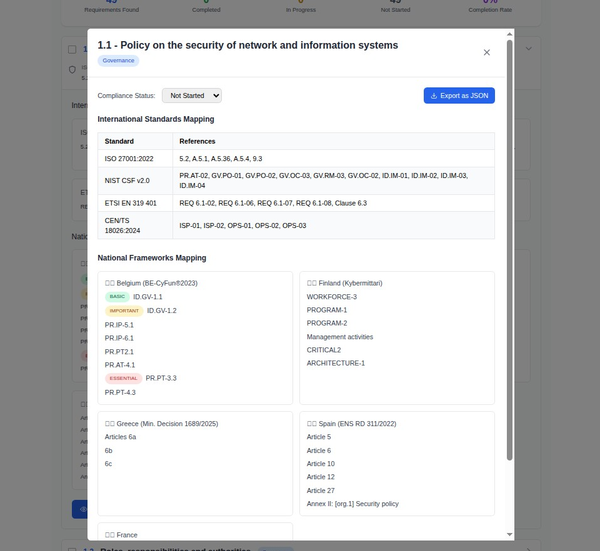
The fine a hospital may face after a ransomware attack depends on several factors, primarily related to the breach of legal obligations under healthcare privacy laws such as the Health Insurance Portability and Accountability Act (HIPAA), as well as potential state data breach laws and, in some cases, international regulations like the General Data Protection Regulation (GDPR) if the hospital handles EU patient data.
1. HIPAA Penalties for Healthcare Entities
Hospitals in the U.S. must comply with HIPAA, which regulates the protection of Protected Health Information (PHI). If a ransomware attack compromises patient data and the hospital is found to have inadequate safeguards, fines can be substantial. The U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR) enforces HIPAA, and penalties are typically divided into four tiers based on the level of negligence:
- Tier 1: The entity was unaware of the violation and would not have known with reasonable diligence. Penalties range from $127 to $63,973 per violation.
- Tier 2: The entity had reasonable cause to know but did not act with willful neglect. Penalties range from $1,280 to $63,973 per violation.
- Tier 3: The entity acted with willful neglect but corrected the issue within 30 days. Penalties range from $12,794 to $63,973 per violation.
- Tier 4: Willful neglect occurred, and no timely correction was made. Penalties are $63,973 per violation, up to an annual maximum of $1,919,173 for repeat violations.
In cases of severe or repeated non-compliance, these fines can accumulate quickly, especially if many patients are affected.
2. State Data Breach Laws
Many states have their own data breach notification laws, and hospitals could face additional fines if they fail to notify patients, the state attorney general, or regulators within a certain timeframe. For example:
- California Consumer Privacy Act (CCPA): While not focused specifically on health data, the CCPA imposes fines of up to $7,500 per violation if sensitive personal information is involved.
3. GDPR Fines
If the hospital handles EU patients' data, the GDPR applies. In the case of a ransomware attack where personal data is compromised and the hospital is found to have insufficient security measures, fines can be steep:
- Up to €10 million or 2% of global turnover, whichever is higher, for violations related to technical security measures.
- Up to €20 million or 4% of global turnover, whichever is higher, for more serious violations such as failing to obtain proper consent or not notifying authorities.
4. Other Potential Consequences
- Lawsuits: Patients affected by data breaches can file class action lawsuits, which can result in significant settlements or judgments.
- Regulatory Investigations: Post-attack, hospitals may face audits or investigations by regulatory bodies like the OCR or state attorneys general, leading to further sanctions.
Mitigation Factors
- Encryption: If patient data was encrypted at the time of the ransomware attack, it might not be considered a "breach" under HIPAA, reducing the hospital’s liability.
- Incident Response: Swift and appropriate incident response, including timely notifications and remediation efforts, can reduce fines and legal exposure.
Hospitals need to maintain strong cybersecurity measures, conduct regular risk assessments, and ensure compliance with both HIPAA and state regulations to minimize fines and mitigate legal risks in the event of a ransomware attack.
Several high-profile breaches in healthcare
Have led to substantial fines for hospitals and healthcare organizations due to violations of HIPAA and other data protection laws. Below are some significant examples of fines resulting from breaches in recent years:
1. Anthem Inc. (2015) – $16 Million (HIPAA Settlement)
- Incident: A cyberattack exposed the electronic protected health information (ePHI) of nearly 79 million individuals. Hackers infiltrated Anthem’s systems using stolen credentials, accessing names, Social Security numbers, addresses, and other sensitive data.
- Fine: The $16 million settlement in 2018 remains one of the largest HIPAA settlements to date. The investigation found that Anthem had insufficient access controls, delayed breach notifications, and inadequate safeguards to protect patient data.
- Key Lesson: The lack of proper security measures and delayed reporting led to the massive fine.
2. Premera Blue Cross (2014) – $6.85 Million (HIPAA Settlement)
- Incident: Premera experienced a data breach that affected 10.4 million individuals. Hackers gained access to its systems, exposing sensitive information such as Social Security numbers and health information.
- Fine: In 2020, Premera agreed to a $6.85 million settlement with the HHS. Investigations found Premera failed to conduct regular risk analyses and did not implement adequate security measures.
- Key Lesson: The settlement highlighted the importance of performing regular security risk assessments and ensuring proactive data protection strategies.
3. University of Texas MD Anderson Cancer Center (2018) – $4.3 Million (HIPAA Fine)
- Incident: MD Anderson faced a series of data breaches involving the loss of unencrypted devices, which contained the ePHI of approximately 35,000 patients.
- Fine: The OCR imposed a $4.3 million fine, citing MD Anderson’s failure to encrypt portable devices and implement adequate security controls despite knowing about the risk.
- Key Lesson: Failure to encrypt sensitive health information and implement adequate security practices can result in heavy fines, especially if vulnerabilities are known but not addressed.
4. Banner Health (2016) – $1.25 Million (HIPAA Settlement)
- Incident: Banner Health was hit by a cyberattack that compromised the ePHI of 2.9 million individuals. Hackers targeted point-of-sale systems at food and beverage outlets within its facilities, later gaining access to patient records.
- Fine: In 2020, Banner Health agreed to pay $1.25 million as part of a HIPAA settlement. Investigators found that Banner Health had failed to conduct an enterprise-wide risk analysis and lacked appropriate security measures.
- Key Lesson: Comprehensive risk assessments and securing third-party systems, such as those handling payment information, are critical in healthcare cybersecurity.
5. Touchstone Medical Imaging (2014) – $3 Million (HIPAA Settlement)
- Incident: Touchstone Medical Imaging had a breach where over 300,000 patients' records were exposed after sensitive health data was accessible online due to improper file server configurations.
- Fine: The OCR levied a $3 million fine in 2019. Touchstone was found to have failed to perform a thorough risk analysis and did not respond to the breach in a timely manner, leading to a significant fine.
- Key Lesson: Misconfigurations leading to exposure of sensitive data online, coupled with delayed breach notifications, can result in costly penalties.
6. CHSPSC LLC (2014) – $2.3 Million (HIPAA Settlement)
- Incident: CHSPSC, a business associate of Community Health Systems, faced a breach where 6 million individuals’ ePHI was exposed due to a cyberattack. Hackers exploited CHSPSC’s vulnerable systems, gaining access to sensitive information.
- Fine: In 2020, CHSPSC agreed to pay a $2.3 million settlement to resolve HIPAA violations. The OCR found that CHSPSC had failed to implement proper technical security measures and perform adequate risk assessments.
- Key Lesson: Business associates of healthcare entities are also liable under HIPAA for failing to protect sensitive data, underscoring the importance of securing third-party systems.
7. NY Presbyterian Hospital & Columbia University (2010) – $4.8 Million (HIPAA Settlement)
- Incident: A data breach occurred when an improperly configured server made the ePHI of 6,800 patients publicly accessible on the internet. The server was jointly managed by New York Presbyterian Hospital and Columbia University.
- Fine: The combined entities paid $4.8 million in 2014. The breach exposed deficiencies in managing electronic health records and ensuring proper security controls between healthcare providers and research institutions.
- Key Lesson: Coordinating security between entities (such as hospitals and universities) and ensuring proper server configurations are critical to avoiding significant fines.
Conclusion
These examples highlight the substantial fines imposed on healthcare entities following data breaches, especially when inadequate security measures, poor risk assessments, or delayed responses are involved. Hospitals and healthcare providers must prioritize proactive cybersecurity, encryption, and risk management to avoid similar penalties.