Virginia's Social Media Age Verification Law: Protection or Precedent for Digital ID Checkpoints?
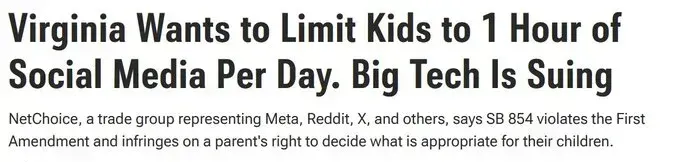
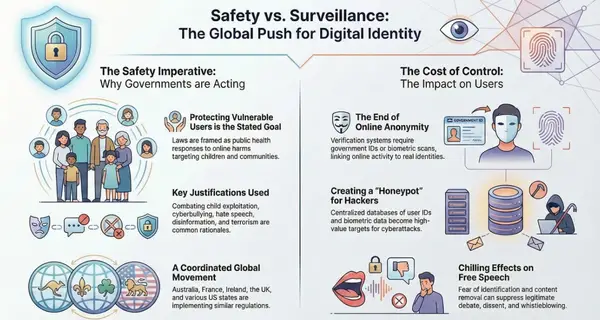
On January 1, 2026, Virginia will become one of the first states to enforce comprehensive age verification requirements across social media platforms, mandating that every user prove their age before accessing sites and limiting minors under sixteen to just one hour of daily use per platform. While lawmakers frame Senate Bill 854 as essential protection for children's mental health, this bizarre law is yet another attempt to collect our biometric data and violate our privacy—transforming the internet from an open forum into a permission-based system where the state determines who can speak and for how long.
The Mechanics of Control
Senate Bill 854, embedded within Virginia's Consumer Data Protection Act, requires social media companies to verify ages through "commercially reasonable methods"—a deliberately vague standard that in practice means collecting government IDs, biometric data, or other identifying information from all users, not just minors. The law imposes a strict one-hour daily limit on users under sixteen, though parents can override these restrictions through "verifiable parental consent," another mechanism requiring identity verification and documentation.
The Virginia Attorney General's office holds enforcement authority, with civil penalties reaching $7,500 per violation—a structure designed to ensure compliance through financial pressure rather than criminal prosecution. Companies that fail to implement age verification systems face mounting fines that could quickly escalate into existential threats for platforms that serve Virginia residents.
The Addiction Narrative
Legislative supporters repeatedly invoked addiction metaphors to justify the intervention. Delegate Wendell Walker compared social media to "a drug addiction," while Delegate Sam Rasoul accused technology companies of deliberately engineering "algorithms that keep us more and more addicted." This framing casts government intervention as a public health response rather than speech regulation—a rhetorical strategy that obscures the constitutional implications of requiring identification to access platforms that host constitutionally protected expression.
The addiction framework also assumes a level of harm that remains contested in academic research. While studies show correlations between heavy social media use and negative mental health outcomes, establishing causation has proven difficult, and research on moderate use shows mixed or neutral effects. By treating all teen social media access as inherently harmful, Virginia's law ignores the substantial evidence that online platforms provide critical support networks, educational resources, and social connection for young people—particularly those from marginalized communities or isolated geographic areas.
The Free Speech Challenge
NetChoice, a technology trade association representing Meta, Reddit, X, and other major platforms, filed a federal lawsuit (NetChoice v. Miyares) against Virginia Attorney General Jason Miyares in November 2025, arguing that SB 854 violates the First Amendment by conditioning access to protected speech on government-approved identification. The complaint draws historical parallels to moral panics over comic books, rock music, and video games—previous episodes where authorities sought to control youth access to media deemed dangerous, only to see those restrictions later recognized as unconstitutional overreach.
The lawsuit's core argument challenges the premise that government age gates are necessary when families already possess extensive tools for managing children's online activity. Modern devices and platforms offer sophisticated parental controls, content filters, screen time limits, and activity monitoring—all available without requiring every user to submit identification to the state. NetChoice contends that Virginia's law "does not enforce parental authority; it imposes governmental authority, subject only to a parental veto," inverting the constitutional relationship between families and government by making state control the default and parental autonomy the exception.
The Infrastructure of Surveillance
Beyond the immediate restrictions on minors, SB 854 establishes infrastructure that affects every user. Age verification systems cannot distinguish between adults and minors without checking everyone, meaning all Virginians—and potentially all Americans accessing platforms that serve Virginia residents—must prove their identity to participate in online discourse. This creates a comprehensive identity verification regime that would have been unthinkable a decade ago but is rapidly becoming normalized through incremental state legislation framed as child protection.
The law prohibits companies from using verification data for other purposes, but this statutory protection offers limited reassurance. Once infrastructure exists to collect and verify identity documents at scale, the technical and legal barriers to expanding its use diminish significantly. Future legislatures could expand permissible uses, data breaches could expose sensitive information, and government agencies could compel access to verification databases—all scenarios that become possible only after the collection systems exist.
This dynamic parallels other surveillance infrastructure that began with narrow, sympathetic justifications before expanding into broader monitoring systems. Automatic license plate readers were initially deployed to find stolen vehicles; they now enable mass tracking of lawful movement. Cell site simulators were reserved for terrorism investigations; they're now used for routine criminal cases. Age verification systems pitched as protecting children establish the technical foundation for comprehensive identity verification of all online speech.
The Biometric Data Collection Concern
The "commercially reasonable methods" language in SB 854 opens the door to biometric data collection on an unprecedented scale. Facial recognition systems, voice analysis, behavioral biometrics—all qualify as verification methods that companies might deploy to comply with Virginia's mandate. Once collected, this biometric data creates permanent digital fingerprints that cannot be changed if compromised, unlike passwords or even government ID numbers.
The privacy implications extend far beyond age verification. Biometric data linked to online activity creates comprehensive profiles of digital behavior tied to immutable physical characteristics. Even if Virginia's statute prohibits certain uses, the data itself becomes a target for hackers, a resource for law enforcement, and a commodity for data brokers willing to skirt regulations. The state has effectively mandated the creation of a biometric database of social media users under the guise of protecting children—a Trojan horse for surveillance infrastructure that civil liberties advocates have opposed for decades.
The Parental Rights Paradox
Virginia lawmakers claim SB 854 empowers parents, yet the law's structure reveals the opposite. Parents who wish to allow their teenagers unrestricted social media access must actively navigate verification systems, provide documentation, and potentially expose their own identities to prove their authority over their children—a bureaucratic burden that transforms parental permission from the default state into an exception requiring justification.
This inversion matters because it reframes the constitutional question. Traditional First Amendment doctrine holds that parents, not government, possess primary authority over children's access to information and ideas. Virginia's law flips this presumption: the state now controls access by default, and parents must petition for exceptions through verification systems that themselves raise privacy concerns. The legal question becomes whether government can condition the exercise of parental authority on participation in state-mandated identification programs.
The practical effect may discourage many parents from seeking overrides. Families concerned about privacy, those uncomfortable with digital identity systems, or those simply unwilling to navigate bureaucratic processes may accept the default one-hour limit rather than submit to verification requirements—allowing the state's judgment to supplant parental decision-making not through direct prohibition but through friction and surveillance costs.
The International Context
Virginia's approach echoes age verification mandates emerging globally, from the United Kingdom's Online Safety Act to the European Union's Digital Services Act to various Australian proposals. These parallel movements suggest coordinated pressure toward identity-bound internet access rather than independent local initiatives. International precedents often preview domestic policy shifts, particularly in areas where lawmakers can leverage child safety concerns to overcome civil liberties objections.
Several countries have already implemented or proposed more aggressive verification requirements, including facial recognition systems, credit card validation, and government-issued digital identity credentials. Virginia's "commercially reasonable methods" standard leaves room for any of these approaches, potentially making the state an early adopter of biometric verification systems that most Americans would reject if proposed overtly rather than embedded in child protection legislation.
The global dimension also highlights the practical impossibility of geographic restrictions on internet platforms. A Virginia resident can easily access platforms through VPNs, international servers, or services that don't verify age due to foreign jurisdiction—making the law's actual impact on teen social media use questionable while its impact on normalizing verification systems remains guaranteed.
The Enforcement Question
Virginia's enforcement mechanism through the Attorney General's office creates political dynamics worth examining. Attorneys general face electoral pressures and often use high-profile enforcement actions to build political profiles, making age verification violations potentially attractive targets for officials seeking to demonstrate toughness on tech companies. The $7,500-per-violation structure means that platforms with millions of users face essentially unlimited exposure—an enforcement club powerful enough to compel compliance regardless of constitutional challenges.
Yet enforcement raises practical questions about which platforms fall under the law's scope. SB 854 targets "social media companies," but this category's boundaries remain contested. Does it include messaging apps? Gaming platforms with chat features? Comment sections on news sites? Educational forums? The ambiguity creates compliance uncertainty while giving enforcement authorities broad discretion over which platforms to target—a discretion that could easily become selective or politically motivated.
The law also creates compliance requirements that may prove technically infeasible or economically unviable for smaller platforms, potentially consolidating social media into a few major companies capable of bearing verification costs and legal risks. This concentration effect runs counter to digital competition and innovation, entrenching dominant platforms while making new entrants nearly impossible—an outcome that serves established corporate interests while being framed as protecting children.
The Slippery Slope Actualized
Civil liberties advocates often invoke slippery slope arguments that critics dismiss as hypothetical scaremongering. Virginia's law demonstrates that the slope isn't hypothetical—it's actively materializing. Once age verification infrastructure exists, expanding its application becomes merely a matter of legislative amendment rather than fundamental systemic change.
Consider the trajectory: Virginia requires age verification to limit teen social media use. Next session, lawmakers could extend time limits to adults "at risk of addiction." Future legislation could mandate identity verification for accessing news sites hosting "misinformation," adult content, gambling platforms, or any category of speech that attracts regulatory attention. Each expansion would leverage existing verification systems, making incremental control easier than the initial infrastructure deployment.
This progression isn't speculative. Other jurisdictions have already moved beyond age verification for minors to broader identity requirements. Louisiana requires age verification for accessing any site with substantial sexual content—a category that could encompass everything from medical information to artistic works to LGBTQ resources. Utah has proposed mandatory social media verification for all users regardless of age. The pattern suggests that child protection serves as the opening argument for comprehensive identity-bound internet access, not the final destination.
The Privacy Contradiction
Virginia's statute includes privacy protections prohibiting companies from using age verification data for other purposes, yet this provision highlights the law's fundamental contradiction: lawmakers recognize that identity verification creates privacy risks serious enough to require specific statutory protection, then mandate that very verification anyway.
The privacy language offers largely illusory protection. Data breaches remain possible regardless of use restrictions. Companies could be compelled to share verification databases with law enforcement through subpoenas or national security letters. Future legislative amendments could expand permissible uses. Third-party verification services—the likely implementation mechanism—create additional breach and misuse vectors beyond the platforms themselves.
Most critically, the verification process itself violates privacy by requiring users to disclose identity information to access anonymous or pseudonymous speech. The First Amendment has long recognized anonymity as essential to free expression, protecting speakers from retaliation, social stigma, or government tracking. Age verification systems eliminate this protection by design, making anonymous political speech, whistleblowing, or controversial advocacy impossible without first identifying oneself to commercial or government verification authorities.
What This Means for Digital Rights
Virginia's age verification law represents a critical moment in internet governance—not because it's uniquely restrictive, but because it normalizes identity verification as a prerequisite for online participation. The law establishes infrastructure and precedents that make future expansions technically trivial and politically feasible, transforming debates about speech regulation from whether verification should exist to merely what restrictions should accompany it.
The broader implication extends beyond social media to the internet's fundamental architecture. The early internet's design philosophy emphasized open access and decentralized control, with technical protocols enabling communication without centralized identity verification. Age verification mandates push toward the opposite model: centralized control, mandatory identification, and state oversight of who can speak and under what conditions.
This transition matters regardless of one's views on social media's impact on youth mental health. Even accepting every claim about algorithmic harm and addictive design, the solution of government-mandated identity verification trades potential psychological risks for certain structural threats to free expression, privacy, and the open internet model. Once verification infrastructure exists, the choice about how to use it passes from users and families to governments and corporations—a power transfer that Virginia's law accelerates under the cover of protecting children.
As January 1, 2026 approaches, Virginians face a new reality: accessing social media will require proving identity through systems that transform the internet from a forum for free expression into a permission-based platform where the state determines who can participate and for how long. Whether courts strike down these requirements or allow them to stand will determine not just Virginia's digital future, but whether American internet access follows the path of open discourse or controlled identification that's emerging globally.
The stakes extend beyond one state's social media policy to fundamental questions about the relationship between government, technology, and constitutional rights in the digital age. Virginia's law provides an early answer—one that prioritizes state control over individual liberty and treats identity verification as a reasonable price for online participation. The alternative vision, where families manage children's internet use without government-mandated identification systems, awaits vindication through either legislative repeal or judicial intervention. Until then, Virginia's approach stands as a warning about how quickly child protection rhetoric can normalize surveillance infrastructure that once seemed dystopian but increasingly appears inevitable.