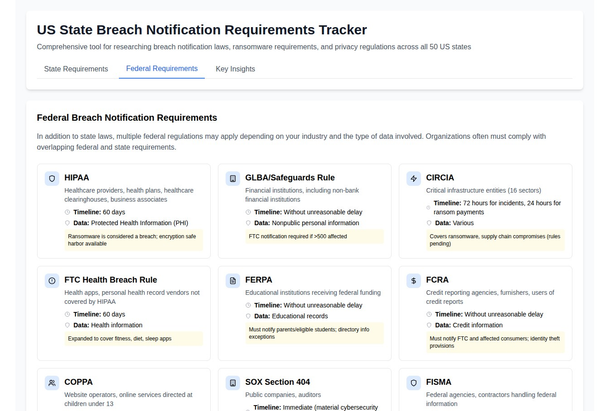
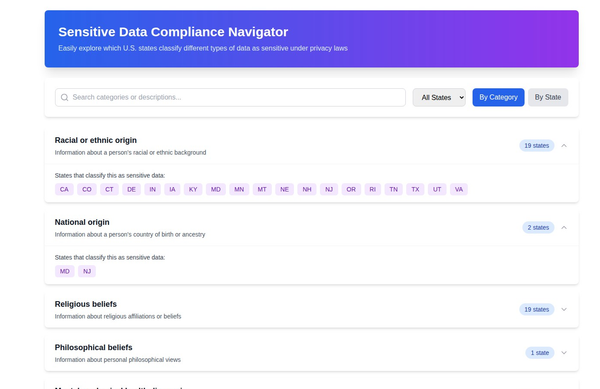
Understanding the Protecting Americans’ Data From Foreign Adversaries Act

In an era where data breaches and digital espionage are front-page news, the need to safeguard Americans’ personal data from foreign adversaries has reached a critical juncture. Policymakers from both major parties have explored legislative solutions to strengthen protections for U.S. citizens against potential foreign surveillance and data exploitation. One such proposal is the Protecting Americans’ Data From Foreign Adversaries Act, aimed at curbing the transfer or misuse of sensitive data by entities controlled or influenced by foreign adversaries.
Below is an in-depth look at the key provisions, objectives, and potential implications of this proposed legislation.
1. Background and Motivations
1.1 Rise of Data-Driven Threats
Advancements in technology have turned data into one of the most valuable resources in the modern world. Mobile devices, IoT (Internet of Things) sensors, social media platforms, and enterprise software generate vast amounts of personal and commercial information. In recent years, reports of foreign-linked entities harvesting Americans’ data—from financial records to location information—have raised concerns in Washington, D.C., that adversarial governments might exploit these datasets for economic or strategic gain.
1.2 High-Profile Incidents
Several high-profile incidents underscored the vulnerability of American data:
- Data Harvesting by Foreign-Owned Apps: Popular mobile applications owned by foreign entities have come under intense scrutiny for allegedly sharing user data with parent companies based in or influenced by adversarial governments.
- Cyberattacks Targeting U.S. Infrastructure: From large-scale ransomware attacks on critical infrastructure to allegations of state-sponsored hacking campaigns, the U.S. has witnessed a surge in cyber threats targeting sensitive systems.
These incidents reinforced the perception that a cohesive, robust legal framework is necessary to defend U.S. data privacy from potential foreign exploitation.
2. Overview of the Legislation
2.1 Legislative Intent
The Protecting Americans’ Data From Foreign Adversaries Act is designed to:
- Define “Foreign Adversaries”: Establish a clear legal definition of which foreign governments, corporations, or individuals constitute adversaries in the eyes of U.S. national security policy.
- Regulate Data Transactions: Impose stricter requirements on the sale, transfer, or processing of Americans’ personal data by any business or platform with ties to foreign adversaries.
- Enhance Government Oversight: Grant federal agencies greater authority to investigate, review, and, if necessary, block transactions or data-sharing arrangements involving companies under foreign influence.
2.2 Scope of Data Covered
The Act broadens the definition of “sensitive personal data” beyond what is traditionally covered by privacy statutes, considering the possibility that any personal identifiable information (PII) could be leveraged for intelligence or espionage. This may include:
- Location data
- Health records
- Biometric identifiers
- Financial information
- Genetic data
By categorizing these and other data types as particularly sensitive, the legislation seeks to provide an elevated degree of protection against unauthorized foreign access.
2.3 Enforcement Mechanisms
Under the bill:
- Federal Authorities: Agencies such as the Department of Commerce and the Department of Homeland Security may gain the power to conduct thorough investigations into companies suspected of improper data transfers to foreign entities.
- National Security Reviews: The Committee on Foreign Investment in the United States (CFIUS) or similar review bodies could be assigned the role of assessing risks and recommending remedies or restrictions on data transfers that could threaten national security.
- Civil and Criminal Penalties: Companies and individuals found in violation of the law could face fines, injunctions, or in severe cases, criminal charges, depending on the degree and nature of the offense.
3. Key Provisions and Mechanisms
- Mandatory Disclosure
Companies that handle significant volumes of U.S. user data or data critical to national security must disclose any foreign ownership, control, or significant investment. This transparency mechanism helps U.S. authorities determine potential vulnerabilities or conflicts of interest. - Risk-Based Assessment
Not every foreign data transaction is inherently malicious. The legislation calls for a risk-based approach, requiring executive agencies to evaluate factors such as:- The track record of the foreign entity or government
- The potential for misuse of the data
- The sensitivity of the data in question
- Data Localization or Restrictions
Where deemed appropriate, U.S. regulators could require data localization (keeping data on domestic servers) or limit how certain categories of data can be stored and transferred internationally. The goal is to minimize exposure of sensitive data beyond U.S. legal jurisdiction. - Collaboration With Allies
Recognizing that data travels across borders seamlessly, the legislation encourages cooperation with allied nations who share similar privacy and security concerns. Joint efforts on cybersecurity standards, best practices, and data transfer protocols can bolster collective defenses against adversarial threats.
4. Potential Impacts
4.1 For Businesses and Tech Companies
- Compliance Costs: Companies handling large quantities of personal data may need to implement new protocols and reporting mechanisms to align with the Act’s provisions, increasing operational costs.
- Increased Scrutiny of Foreign Investment: Tech firms and startups seeking foreign capital may face additional review processes or limitations, potentially affecting funding options and expansion strategies.
4.2 For Consumers
- Enhanced Data Security: If effectively enforced, consumers will benefit from stronger safeguards against unauthorized foreign access to their personal information.
- Privacy Confidence: The Act may foster greater public trust in digital platforms, given new layers of legal and regulatory oversight on cross-border data transfers.
4.3 For International Relations
- Trade and Diplomatic Tensions: Countries considered “adversarial” may retaliate with countermeasures, potentially complicating broader diplomatic engagements and trade agreements.
- Collaborative Frameworks: The Act could also serve as a blueprint for like-minded nations to enact similar protections, encouraging the development of multinational data protection frameworks and shared cybersecurity protocols.
5. Criticisms and Challenges
Despite its lofty intentions, the Protecting Americans’ Data From Foreign Adversaries Act has encountered criticisms and logistical challenges:
- Overreach Concerns
Critics worry that the Act’s broad definition of “foreign adversaries” or “sensitive data” might lead to overregulation and stifle innovation. There is apprehension that some businesses—especially smaller tech startups—may find compliance overly burdensome or costly. - Free Trade Implications
Some industry groups argue that stringent data localization requirements and expanded government oversight could undermine U.S. commitments to free trade. The tension between national security and economic liberalization is a recurring theme in discussions about foreign technology investment. - Legal Complexities
Balancing national security priorities with individual rights and global commerce laws could prove challenging. Vague or expansive provisions could create legal ambiguity about the extent of government power to monitor or restrict data transfers. - Rapid Technological Change
The pace of tech innovation often outstrips the speed of legislative updates. Critics question whether the Act, once passed, would be flexible enough to adapt to emerging technologies such as quantum computing, AI-driven data analytics, and decentralized data systems.
6. Outlook and Future Developments
The exact fate of the Protecting Americans’ Data From Foreign Adversaries Act will depend on negotiations in Congress, input from federal agencies, and the evolving geopolitical landscape. Several lawmakers have emphasized the urgency of creating a robust legal framework to protect Americans’ data, while others caution against measures that might overly restrict the flow of information and commerce.
Regardless of the final legislative text, the ongoing debate underscores how critical data security and privacy have become in U.S. national security policy. As threats multiply in a hyper-connected global environment, lawmakers, regulators, and businesses alike will need to collaborate on policy solutions that strike a balance between protecting citizens’ data and fostering technological innovation.
7. Conclusion
The Protecting Americans’ Data From Foreign Adversaries Act seeks to address mounting concerns over foreign entities’ access to U.S. citizens’ personal information. By establishing stronger oversight, clearer definitions, and potential penalties for misuse, this legislative effort aims to insulate American data from exploitation. However, like any significant legislative proposal, it faces challenges related to legal interpretation, economic impact, and the lightning pace of technological change.
As the digital landscape continues to evolve, so will the conversation around national data protection. This Act represents one of several legislative attempts to navigate the complexities of global data flows, highlighting a growing consensus in Washington that data privacy and national security are inextricably linked. How effectively these proposals are implemented—and how they adapt to new threats—will determine the future of digital security and innovation in the United States.
Further Reading
- Cybersecurity and Infrastructure Security Agency (CISA) – Official Website
- Committee on Foreign Investment in the United States (CFIUS) – U.S. Department of Treasury
- Federal Trade Commission (FTC) – Privacy and Data Security Resources
Disclaimer: This article is for informational purposes only and does not constitute legal advice. For specific inquiries or compliance guidance, consult an attorney or qualified legal professional.