The Dutch NIS2 Law (Cbw) is Delayed to 2026. Acting Now is Not Optional—It's a Fiduciary Duty.
Introduction: The Upcoming Cyber Shift
Businesses today operate under constant pressure from two fronts: the escalating sophistication of cyber threats and a new wave of regulations designed to counter them. At the forefront of this regulatory shift is the European Union’s new cybersecurity rule, NIS2, which establishes a high common standard of digital resilience across all member states.
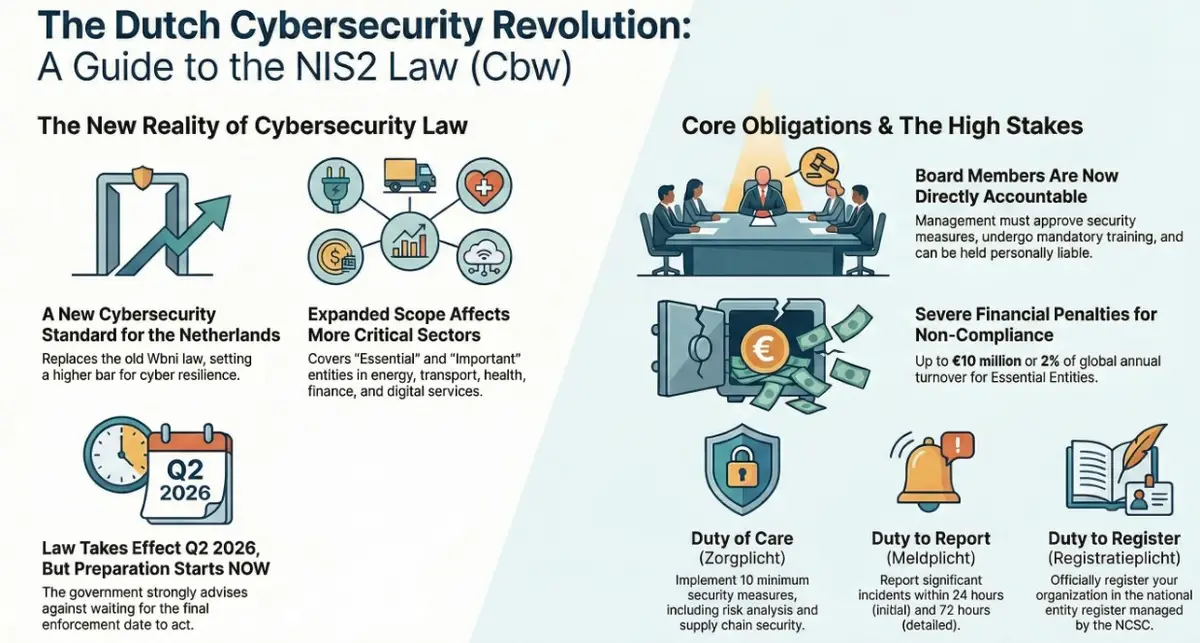
In the Netherlands, this directive is being implemented as the Cyberbeveiligingswet (Cbw). However, recent news has confirmed that its official enforcement has been delayed, with the new target set for the second quarter of 2026. For many, this delay might seem like a welcome reprieve—a chance to push a complex compliance project further down the road.
This is a dangerously misleading assumption. Ignoring the Cbw until its formal enforcement date is a major strategic mistake. The law's impact is already taking shape, and the risks of inaction are immediate and substantial. Here are the five most surprising and impactful reasons why your organization must act now.
--------------------------------------------------------------------------------
1. It’s Not Just for Power Grids Anymore: The Law's Massive Scope
While the previous cybersecurity law (the Wbni) primarily focused on traditional critical infrastructure, the new Cbw dramatically expands its scope. This expansion reflects the government's recognition that societal functions are now critically dependent on the digital operations of sectors like food production and waste management, which have become prime targets for disruptive cyberattacks.
The law now applies to a wide array of new sectors. This includes organizations involved in Waste Management, Food production and distribution, Chemical manufacturing, and other Critical Manufacturing sectors, such as the production of electronics, machinery, and motor vehicles.
Inclusion is determined by a straightforward "size-cap rule." All medium and large organizations within these sectors are now covered. A "medium" organization has at least 50 employees or an annual turnover or balance sheet total of over €10 million. A "large" organization has over 250 employees, or an annual turnover exceeding €50 million and a balance sheet total exceeding €43 million.
The impact is profound: countless businesses that never considered themselves part of the national critical infrastructure now face significant new legal obligations. Crucially, the inclusion of manufacturing sectors acknowledges the convergence of information technology (IT) and operational technology (OT), demanding a unified security strategy that protects both corporate networks and industrial control systems.
2. The Board of Directors Is Now Personally on the Hook
The Cbw elevates cybersecurity from an IT problem to a non-delegable, board-level responsibility. The law codifies this by imposing three core governance mandates directly on the management body:
- The management body must approve the organization's cybersecurity risk-management measures.
- They must oversee the implementation of these measures.
- They are required to follow a recognized training program to gain sufficient knowledge to identify and assess cybersecurity risks and be able to demonstrate this with a certificate.
This creates an explicit and enforceable fiduciary duty. The gravity of this change is captured in the directive's text, which states that management bodies "can be held liable for infringements."
This fundamentally changes the nature of executive liability. The mandatory, certified training requirement is designed to eliminate "plausible deniability" for board members regarding cybersecurity oversight. Failure to attend this training is, in itself, an auditable violation, making it clear that while operational tasks can be delegated, the ultimate responsibility for cybersecurity resilience now rests squarely in the boardroom.
3. The Official 2026 Deadline Is a Mirage
The facts are clear: the Netherlands will miss the original EU deadline of October 17, 2024, to implement the directive. The new target for the Cbw to formally enter into force is the second quarter of 2026. However, treating this date as the starting line for compliance efforts is a critical error.
The Dutch government (Rijksoverheid) has explicitly and strongly advised organizations not to wait for the law to become active. Its official guidance is unambiguous:
De Rijksoverheid adviseert organisaties om niet af te wachten totdat de Cyberbeveiligingswet inwerking treedt. De risico’s die organisaties en systemen lopen, zijn er immers nu ook al.
"The national government advises organizations not to wait until the Cybersecurity Act enters into force. After all, the risks that organizations and systems run already exist."
This creates a "2025 preparation window." While the law may not be formally enforceable until 2026, its requirements are already known. If a major cyber incident were to occur before the enforcement date, a demonstrable lack of preparation based on the Cbw's published standards could be viewed as managerial negligence, regardless of the law's official status.
4. It Creates a "Regulatory Domino Effect" in Your Supply Chain
One of the most significant but least obvious impacts of the Cbw is the "regulatory domino effect" it will trigger throughout the Dutch economy. The law doesn't just apply to individual companies in isolation; it addresses the systemic risk present in modern, interconnected supply chains.
The Cbw mandates that regulated entities, particularly large "Essential Entities," must actively manage the cybersecurity risks within their own supply chains. In practice, this means these larger companies will be legally required to audit and manage the security of their external service providers and acquisitions, ensuring suppliers meet security thresholds equivalent to their own.
This requirement functionally compels smaller suppliers—even those who may not fall directly under the Cbw's size rules—to adopt NIS2-level security standards through mandatory contractual clauses. For suppliers, this means that demonstrating Cbw-aligned security is no longer just a defensive measure, but a commercial differentiator essential for retaining and winning contracts with larger clients.
5. The Fines Are Big Enough to Get the CFO’s Attention
To ensure compliance is taken seriously, the Cbw introduces severe, GDPR-scale financial penalties for violations. These sanctions are designed to be a substantial deterrent and are structured in two tiers based on an entity's classification:
- Essential Entities: Subject to fines of up to €10 million or 2% of the entity’s total worldwide annual turnover, whichever is higher.
- Important Entities: Subject to fines of up to €7 million or 1.4% of the entity’s total worldwide annual turnover, whichever is higher.
The comparison to GDPR is intentional and gives a familiar frame of reference for the financial magnitude of these penalties.
These sanctions elevate cybersecurity failures to a material financial risk. This means non-compliance is no longer just an operational issue; it's a financial threat that requires board-level attention, explicit consideration in financial reporting, and integration into enterprise-wide risk management frameworks.
--------------------------------------------------------------------------------
Conclusion: A New Baseline for Business Resilience
The Cyberbeveiligingswet is not just another IT compliance checklist. It represents a fundamental shift that embeds cybersecurity directly into corporate governance, supply chain management, and financial risk assessment, establishing a new, non-negotiable aspect of enterprise risk management on par with financial or operational risk.
Waiting for the formal enforcement date in 2026 is an unsustainable strategy. The board's new personal liability is the driving force that necessitates a robust, defensible budget for managing the "regulatory domino effect" in the supply chain. A failure in a supplier could now directly lead to an auditable breach of fiduciary duty, exposing the organization to material financial risk. The law establishes a new, higher baseline for business resilience in an increasingly hostile digital world.
With cybersecurity now a core fiduciary duty, is your leadership team truly prepared to answer for it?