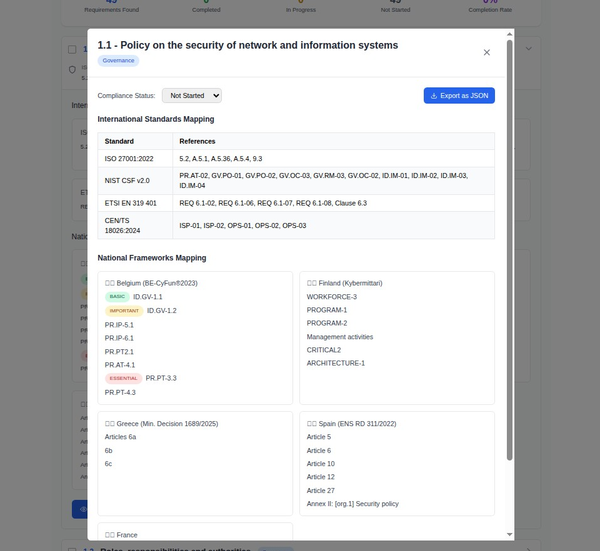
Service Organization Control (SOC)

Service Organization Control (SOC) reports are a suite of reports produced during an audit of a service organization. They are intended to help service organizations build trust and confidence in their service delivery processes and controls. Here's a matrix outlining SOC 1, SOC 2, and SOC 3 reports, along with their respective types:
| Report | Type | Description |
|---|---|---|
| SOC 1 | Type 1 | Evaluates and reports on the design of controls at a service organization at a specific point in time. This report is focused primarily on controls relevant to an audit of a user entity’s financial statements. |
| SOC 1 | Type 2 | Similar to Type 1, but it also includes the operational effectiveness of these controls over a minimum period of six months. Primarily relevant for financial reporting. |
| SOC 2 | Type 1 | Reports on the design of controls related to security, availability, processing integrity, confidentiality, or privacy at a specific point in time. SOC 2 is broader in scope than SOC 1, addressing controls that relate to operations and compliance. |
| SOC 2 | Type 2 | In addition to the Type 1 criteria, this report includes the operational effectiveness of these controls over a minimum period of six months. It covers the same trust principles as SOC 2 Type 1. |
| SOC 3 | - | Similar to SOC 2 reports but intended for a general audience. It provides a summary of the service organization’s system and the effectiveness of controls, but without the detailed description included in SOC 2 reports. |
Key Differences:
- SOC 1 focuses on controls at a service organization relevant to user entities’ internal control over financial reporting.
- SOC 2 focuses on controls at a service organization relevant to security, availability, processing integrity, confidentiality, or privacy.
- SOC 3 provides a general overview of controls related to trust principles but in a format suitable for public consumption.
Selection:
- Service organizations choose SOC 1 if their services impact user entities' financial reporting.
- SOC 2 is chosen for more comprehensive reporting on IT and data controls, particularly where confidentiality and privacy are of concern.
- SOC 3 is often used for marketing purposes as it is less detailed and can be freely distributed.
Type 1 reports in both SOC 1 and SOC 2 are about control design at a specific point in time, whereas Type 2 reports in both cover the operational effectiveness of these controls over a specified period.
Comparing and contrasting how each of these policies fits within the frameworks of SOC 1, SOC 2, and SOC 3 (Types I and II) involves understanding the focus and scope of each SOC report type and how the policies align with their respective objectives:
1. SOC 1 (Type I & II)
- Focus: Internal control over financial reporting.
- Relevant Policies: Access Control, Change Management, Incident Response and Business Continuity, Compliance and Audit, Network Security.
- Comparison: SOC 1 primarily concerns financial data integrity. Policies like Access Control and Change Management are critical for ensuring that financial data is accurate, reliable, and secure.
2. SOC 2 (Type I & II)
- Focus: Security, Availability, Processing Integrity, Confidentiality, and Privacy of information systems.
- Relevant Policies: Data Protection and Privacy, Information Security, Cloud Security, Network Security, Vulnerability Management, Encryption.
- Comparison: SOC 2 has a broader scope compared to SOC 1, focusing on overall IT and data security. Policies like Data Protection and Privacy, and Cloud Security are more aligned with SOC 2’s requirements, addressing confidentiality and privacy concerns.
3. SOC 3 (Type I & II)
- Focus: General information about data security based on SOC 2 principles but for a wider audience.
- Relevant Policies: Same as SOC 2 but less detailed.
- Comparison: SOC 3 reports are less technical and detailed compared to SOC 2. The same policies apply, but the emphasis is on providing a high-level understanding of controls without the technical depth of SOC 2.
Type I vs. Type II:
- Type I Reports: Focus on the design of controls at a specific point in time.
- All SOC Types: Assessment of whether the policies are appropriately designed to meet the specified criteria.
- Type II Reports: Focus on the operational effectiveness of these controls over a period of time.
- All SOC Types: Evaluation of how effectively these policies are implemented and maintained over time.
Summary:
- SOC 1 Policies: Narrower focus, primarily on controls affecting financial data integrity.
- SOC 2 Policies: Broader, encompassing overall IT and data security practices.
- SOC 3 Policies: Similar to SOC 2 but less detailed, for a general audience.
- Type I vs. Type II: Type I evaluates design, while Type II assesses operational effectiveness over time.
Each set of policies contributes differently to the SOC framework they are aligned with, reflecting the unique focus and scope of each SOC type.
Below is a master list that includes all the information security policies discussed, suitable for a comprehensive program aligned with SOC 1, SOC 2, and SOC 3 standards:
- Information Security Policy
- Access Control Policy
- Data Protection and Privacy Policy
- Network Security Policy
- Asset Management Policy
- Human Resources Security Policy
- Physical Security Policy
- Operational Security Policy
- Incident Response and Business Continuity Policy
- Vendor and Third-Party Security Policy
- Compliance and Audit Policy
- Encryption Policy
- Remote Access and Teleworking Policy
- Email and Communication Policy
- BYOD (Bring Your Own Device) Policy
- Password and Authentication Policy
- Change Management Policy
- Cloud Security Policy
- Mobile Device and Wireless Security Policy
- Backup and Data Recovery Policy
- Security Monitoring and Log Management Policy
- Vulnerability Management Policy
- Cryptography Policy
- Software Development and Lifecycle Security Policy
- Information Classification and Handling Policy
- Third-Party and Outsourcing Security Policy
- Social Media Security Policy
- Environmental and Safety Policy
- Intellectual Property Rights (IPR) Policy
- Incident Reporting and Whistleblower Policy
Implementation Guidance:
- Customization: Each policy should be tailored to the specific needs, size, and operational context of your organization.
- Integration: Ensure these policies are embedded in operational processes and company culture.
- Review and Update: Regularly review and update policies to ensure they remain effective, relevant, and compliant with current laws and standards.
- Training and Awareness: Provide ongoing training and awareness programs for all staff to ensure understanding and compliance with these policies.
- Enforcement: Establish clear consequences for non-compliance and ensure consistent enforcement of policies.
This comprehensive list covers a broad range of areas essential for a robust information security program, addressing various aspects of risk management, security controls, compliance, and best practices as required by SOC frameworks.
Interplay and Contrast Between Policies Across SOC Types:
To effectively compare and contrast the 30 policies in the master list and understand how they work together within the frameworks of SOC 1, SOC 2, and SOC 3 requirements, we'll need to consider the specific focus areas of each SOC type and how these policies align or differ in their application. Let's break it down:
1. Information Security Policy
- SOC 1: Ensures protection of financial data.
- SOC 2 & 3: Provides the overarching framework for data security across all five trust service principles.
2. Access Control Policy
- SOC 1: Critical for safeguarding financial data integrity.
- SOC 2 & 3: Broader scope; includes securing access to all types of data and systems.
3. Data Protection and Privacy Policy
- SOC 1: Less emphasis unless financial data includes personal data.
- SOC 2 & 3: Central to maintaining confidentiality and privacy of data.
4. Network Security Policy
- SOC 1: Ensures secure processing of financial transactions.
- SOC 2 & 3: Vital for protecting network infrastructure and data.
5. Asset Management Policy
- SOC 1: Focuses on financial assets and information systems.
- SOC 2 & 3: Involves broader asset management, including cloud-based assets.
6. Human Resources Security Policy
- SOC 1: Ensures staff handling financial data are secure and trustworthy.
- SOC 2 & 3: Broader application for staff training and security awareness.
7. Physical Security Policy
- SOC 1: Protects physical access to financial data and systems.
- SOC 2 & 3: Ensures security of physical infrastructure hosting any data.
8. Operational Security Policy
- SOC 1: Relates to operational controls affecting financial reporting.
- SOC 2 & 3: Encompasses a broader range of operational procedures.
9. Incident Response and Business Continuity Policy
- SOC 1: Focuses on continuity of financial operations.
- SOC 2 & 3: Covers a wider range of incidents and business operations.
10. Vendor and Third-Party Security Policy
- SOC 1: Pertains to vendors handling financial data.
- SOC 2 & 3: Includes broader vendor and third-party risk management.
11. Compliance and Audit Policy
- SOC 1: Compliance with financial reporting standards.
- SOC 2 & 3: Broader compliance with data security and privacy standards.
12. Encryption Policy
- SOC 1: Encrypts financial data for confidentiality.
- SOC 2 & 3: Applies to encryption of all sensitive data.
13. Remote Access and Teleworking Policy
- SOC 1: Secures remote access to financial systems.
- SOC 2 & 3: Includes broader considerations for secure remote work environments.
14. Email and Communication Policy
- SOC 1: Protects financial information shared via email.
- SOC 2 & 3: Secures all forms of communication and data transmission.
15. BYOD (Bring Your Own Device) Policy
- SOC 1: Manages risks of financial data on personal devices.
- SOC 2 & 3: More comprehensive, covering broader data categories.
16. Password and Authentication Policy
- SOC 1: Ensures secure authentication for financial systems.
- SOC 2 & 3: Applies to all systems to protect data integrity.
17. Change Management Policy
- SOC 1: Critical for changes affecting financial reporting.
- SOC 2 & 3: Broader scope, encompassing all IT system changes.
18. Cloud Security Policy
- SOC 1: Relevant if financial systems are cloud-based.
- SOC 2 & 3: Essential for managing cloud security comprehensively.
19. Mobile Device and Wireless Security Policy
- SOC 1: Secures financial data on mobile devices.
- SOC 2 & 3: Wider application for mobile and wireless security.
20. Backup and Data Recovery Policy
- SOC 1: Ensures financial data is recoverable.
- SOC 2 & 3: Applies to all critical data recovery.
21. Security Monitoring and Log Management Policy
- SOC 1: Monitors financial system activities.
- SOC 2 & 3: Involves comprehensive monitoring for security insights.
22. Vulnerability Management Policy
- SOC 1: Focuses on vulnerabilities affecting financial data.
- SOC 2 & 3: Involves broader vulnerability assessments.
23. Cryptography Policy
- SOC 1: Encrypts sensitive financial information.
- SOC 2 & 3: Applies to cryptographic controls across all data.
24. Software Development and Lifecycle Security Policy
- SOC 1: Relates to development of financial software.
- SOC 2 & 3: Includes secure software practices for all applications.
25. Information Classification and Handling Policy
- SOC 1: Classifies financial data.
- SOC 2 & 3: Broader classification and handling of all sensitive data.
26. Third-Party and Outsourcing Security Policy
- SOC 1: Controls third-party handling of financial information.
- SOC 2 & 3: Includes broader outsourcing and third-party engagements.
27. Social Media Security Policy
- SOC 1: Less relevant.
- SOC 2 & 3: Protects against data leaks and security breaches via social media.
28. Environmental and Safety Policy
- SOC 1: Relevant for physical safety of financial data centers.
- SOC 2 & 3: Includes broader environmental and safety considerations.
29. Intellectual Property Rights (IPR) Policy
- SOC 1: Protects financial methodologies and algorithms.
- SOC 2 & 3: Wider application for protecting all organizational IPR.
30. Incident Reporting and Whistleblower Policy
- SOC 1: Ensures financial irregularities are reported.
- SOC 2 & 3: Encourages reporting of any security incidents or unethical practices.
Summary:
- SOC 1 Policies: Center around financial data integrity and reporting.
- SOC 2 Policies: More expansive, covering IT and data security across various domains.
- SOC 3 Policies: Similar to SOC 2 but in a less detailed format suitable for public distribution.
- Interplay: Many policies have broader applications in SOC 2 and 3 compared to SOC 1, reflecting the wider scope of IT security and operational integrity beyond just financial reporting.