Senate Passes Intelligence Authorization Act in Response to Salt Typhoon: A Turning Point for U.S. Cybersecurity

The Senate Intelligence Committee's recent approval of the Intelligence Authorization Act represents a watershed moment in America's cybersecurity posture, directly addressing the devastating breach known as Salt Typhoon—what officials are calling "the worst telecom hack in our nation's history." This legislative response underscores the profound impact that Chinese state-sponsored cyber operations have had on U.S. national security infrastructure and marks a significant shift toward proactive cybersecurity governance.
The Salt Typhoon Breach: A National Security Crisis
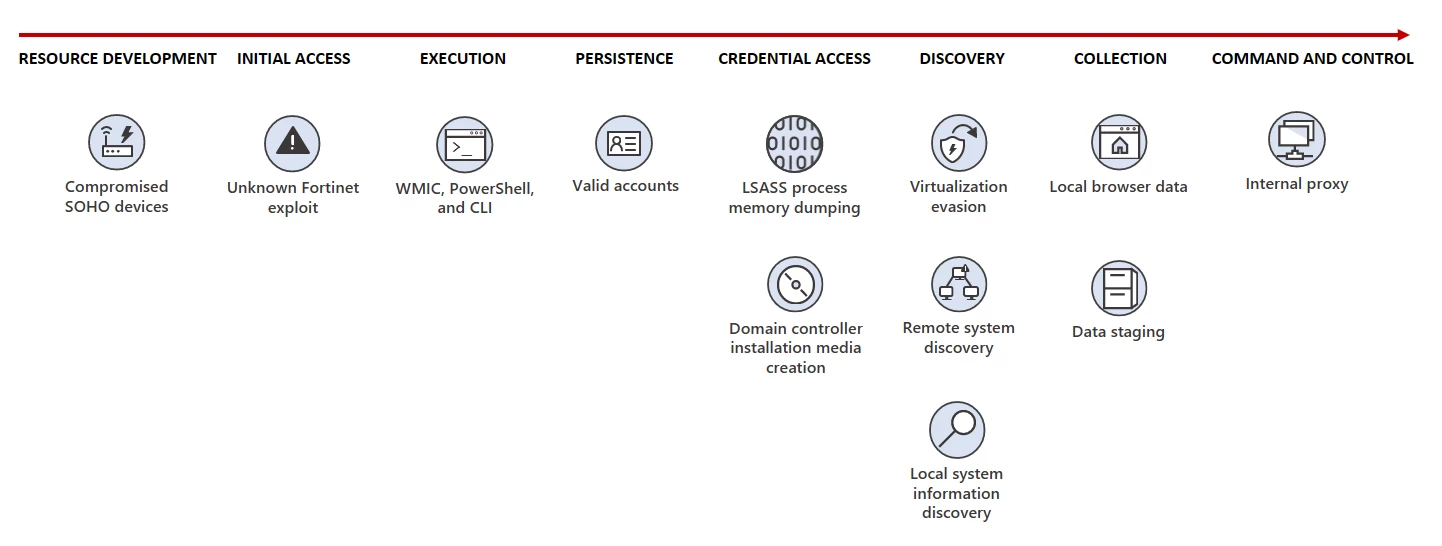
The Chinese hacking group known as Salt Typhoon penetrated multiple U.S. telecommunications networks, creating what cybersecurity experts and government officials view as an unprecedented espionage operation. The hackers acquired access to the system that logs U.S. law enforcement requests for criminal wiretaps, allowing the Chinese to know who is of interest to American investigators. This breach fundamentally compromised the integrity of America's most sensitive surveillance infrastructure.
The scope of the attack was extensive. Salt Typhoon deeply penetrated major U.S. telecommunications networks, including AT&T and Verizon, and also breached Lumen Technologies, specifically targeting their wiretapping systems. The implications of this breach extend far beyond corporate cybersecurity failures—it represents a direct assault on America's ability to conduct lawful intelligence and law enforcement operations.
What makes Salt Typhoon particularly alarming is its nature as an espionage operation rather than pre-positioning for critical infrastructure sabotage. The hackers accessed call records on numerous Americans, including officials and staff affiliated with President-elect Trump's administration. This suggests a sophisticated, long-term intelligence gathering operation designed to provide the Chinese government with unprecedented insight into American political, legal, and security apparatus.
Legislative Response: The Intelligence Authorization Act
The Senate Intelligence Committee on Tuesday approved an annual intelligence authorization bill that aims to augment defenses against digital espionage campaigns like the recent China-linked attack. This legislation represents Congress's most comprehensive response to the Salt Typhoon breach and broader Chinese cyber threats.
The act introduces several critical provisions specifically designed to address telecommunications vulnerabilities. The measure aims to prevent compromise of U.S. telecommunications through strengthening network security by establishing "baseline cybersecurity requirements for vendors of telecommunications services" to the country's 18 intelligence agencies. This requirement represents a fundamental shift from voluntary cybersecurity standards to mandatory compliance frameworks.
Additionally, the Intelligence committee's bill "shores up counter-intelligence risks posed" by compromises of U.S. telecommunications infrastructure created via Salt Typhoon through "leveraging" the clandestine community's "procurement power." This language suggests that intelligence agencies will use their significant purchasing power to enforce cybersecurity standards across the telecommunications sector.
The broader context of this legislation is significant. This bill takes unprecedented steps to address counterintelligence risks to our National Laboratories by prohibiting visitors from foreign adversary nations thereby protecting America's research and competitive advantage. The bill ensures resources are focused on the most pressing threats, specifically from China, Russia, Iran, and their partners, including Cuba, Venezuela, and North Korea, as well as terrorist organizations.

Congressional Oversight and Accountability
The Salt Typhoon incident has triggered intense congressional scrutiny of telecommunications companies and their cybersecurity practices. U.S. Senator Maria Cantwell demanded answers from AT&T Chairman and CEO John Stankey and from Verizon Chairman and CEO Hans Vestberg about ongoing vulnerabilities related to the successful Chinese state-sponsored "Salt Typhoon" hack. This oversight reflects growing frustration with what lawmakers view as inadequate corporate cybersecurity measures.
Senator Ron Wyden wrote to US Attorney General Merrick Garland and Federal Communications Commission Chair demanding that agencies "finally act to secure US telephone and broadband companies' wiretapping systems from hackers." This bipartisan pressure demonstrates the urgency with which Congress views the need for telecommunications security reform.
The oversight efforts have revealed concerning gaps in corporate cybersecurity practices. In December 2024, both AT&T and Verizon claimed that their networks were secure, yet questions remain about the completeness of remediation efforts and the potential for future breaches.
Federal Response and Sanctions
The Biden administration has responded to Salt Typhoon with both legislative and executive actions. Treasury sanctions actions aimed at combatting increasingly reckless cyber activity by the PRC and PRC-based actors, including the January 3, 2025 designation of Integrity Technology Group, Inc. for its role in Flax Typhoon malicious cyber activity, demonstrate a coordinated approach to addressing Chinese cyber threats.
Lawmakers have touted the addition of a $3 billion investment that closes a financial shortfall in a Federal Communications Commission program to help rural broadband providers rip out and replace Chinese-made internet equipment. This funding addresses a critical vulnerability in America's telecommunications infrastructure by removing potentially compromised hardware from the network.

The Broader Cybersecurity Landscape
Experts told lawmakers that without urgent federal action to strengthen cyber defenses and additional efforts to improve the cybersecurity practices of telecommunications companies, another Salt Typhoon-style attack is virtually inevitable. This warning underscores the systemic nature of the vulnerabilities that Chinese hackers exploited.
Congressional hearings titled "Salt Typhoon: Securing America's Telecommunications from State-Sponsored Cyber Attacks" have brought together government officials, cybersecurity experts, and industry representatives to examine the breach's implications and develop comprehensive response strategies.
The telecommunications sector's vulnerability to state-sponsored attacks reflects broader challenges in securing critical infrastructure. Unlike traditional cybersecurity threats that focus on financial gain or disruption, state-sponsored operations like Salt Typhoon are designed for long-term intelligence gathering and strategic advantage.

Policy Implications and Future Directions
The Intelligence Authorization Act's passage represents more than a reactive measure to Salt Typhoon—it signals a fundamental shift in how the U.S. approaches cybersecurity governance. By establishing baseline cybersecurity requirements for telecommunications vendors serving intelligence agencies, Congress is creating a model that could expand to other critical infrastructure sectors.
House lawmakers earlier this week approved by voice vote a measure that would designate the National Telecommunications and Information Administration as the lead agency for protecting the country's communications networks. This organizational change reflects recognition that cybersecurity requires centralized coordination rather than fragmented agency approaches.
The legislation's emphasis on leveraging procurement power represents an innovative approach to cybersecurity enforcement. By requiring vendors to meet specific security standards to maintain government contracts, the intelligence community can drive industry-wide improvements in cybersecurity practices.

Challenges and Limitations
Despite the comprehensive nature of the legislative response, significant challenges remain. The mostly classified measure authorizes billions of dollars in spending by the U.S. intelligence agencies, as well as sets funding levels for intelligence-related efforts. However, due to the sensitivities involved with the annual intelligence bill, public portions often aren't released until weeks after passage. This classification limits public understanding of specific measures and their implementation.
The effectiveness of new cybersecurity requirements will depend heavily on implementation and enforcement. Previous efforts to establish voluntary cybersecurity standards have had mixed results, raising questions about whether mandatory requirements will achieve better outcomes.
Additionally, the global nature of telecommunications infrastructure means that securing American networks requires international cooperation and coordination. Chinese state-sponsored groups operate across multiple jurisdictions, making attribution and response particularly challenging.

Conclusion
The Senate Intelligence Committee's approval of the Intelligence Authorization Act in response to Salt Typhoon represents a critical inflection point in American cybersecurity policy. By establishing mandatory cybersecurity standards for telecommunications vendors and leveraging government procurement power to drive industry improvements, Congress is taking decisive action to address the vulnerabilities that Chinese hackers exploited.
However, the Salt Typhoon breach has revealed fundamental weaknesses in America's telecommunications infrastructure that extend beyond any single legislative fix. The incident demonstrates that state-sponsored cyber operations pose existential threats to national security infrastructure and require sustained, coordinated responses across government and industry.
The success of this legislative response will ultimately be measured not by the passage of new laws, but by the effective implementation of cybersecurity standards that can prevent future breaches. As experts warn that another Salt Typhoon-style attack is likely, the urgency of this implementation cannot be overstated. The American people deserve telecommunications infrastructure that is secure from foreign adversaries, and this legislation represents an important step toward that goal.
The broader implications of Salt Typhoon extend beyond cybersecurity to questions of national sovereignty, economic security, and the protection of democratic institutions. As the U.S. continues to confront an increasingly assertive and technologically sophisticated China, the lessons learned from Salt Typhoon will inform cybersecurity policy for years to come.











