Policy Briefing: The Global Digital Identity Landscape—Models, Implementations, and Strategic Implications
1.0 Introduction: Defining Digital Identity and its Strategic Importance
A digital identity is the collection of data stored on computer systems that represents an individual, organization, or device. For individuals, this identity is composed of a wide range of personal data, including usernames, online search histories, purchase records, and official identifiers like social security numbers. When aggregated, these digital footprints can form a comprehensive profile often referred to as a "data double." In today's interconnected world, possessing a verifiable digital ID is paramount for participation in the digital economy. It is the key that unlocks access to critical e-government services, facilitates online purchases, and enables secure financial transactions.
This briefing analyzes the primary models of digital identity systems, examines key national implementations, and assesses the critical policy challenges that are shaping the future of digital identity. At the core of any digital ID system are three fundamental processes, as defined by the International Telecommunication Union (ITU):
- Identification (Proofing): The initial process of establishing and formally verifying an identity. This often involves the examination of foundational documents such as passports, birth certificates, or other official records to corroborate the identity being claimed.
- Authentication: The subsequent process of validating an identity assertion. This is typically accomplished by presenting a credential—such as a password, a smart card, or a biometric factor like a fingerprint—to prove that an individual is who they claim to be.
- Authorization: The final process of determining the specific actions, services, or resources that an authenticated identity is permitted to access.
The architectural design of systems that manage these three processes varies significantly around the world, each carrying distinct implications for governance, security, and individual rights.

2.0 Competing Models of Digital Identity: A Global Taxonomy
Governments and organizations have adopted several distinct architectural models for digital identity systems, each with different implications for governance, user control, and the role of the private sector. The choice of model reflects a country's unique legal traditions, technological infrastructure, and policy priorities. This section analyzes the dominant institutional models shaping the global landscape.
2.1 Government-Driven Centralized Systems
In this model, the government owns and operates one or more central databases that serve as the authoritative source of identity. State-issued electronic IDs (eIDs) are the primary credentials used for most digital transactions, both public and private. This approach provides a strong, state-backed foundation for identity but can create risks associated with centralized data storage. This model is evident in the national systems of Belgium, Germany, Pakistan, and Malaysia.
2.2 Semi-Centralized Federated Systems
Under a federated model, individuals can choose from multiple trusted identity providers, which can be public or private entities. These providers are accredited or coordinated through a central trust framework or identity hub, allowing users to leverage a single, trusted credential to access a wide range of services. This model promotes competition and user choice but requires robust interoperability standards and oversight, as seen in countries such as Sweden, the United Kingdom, and Australia.
2.3 Decentralized and Open-Market Systems
This model is characterized by the absence of a single, overarching national identity scheme. Instead, public and private entities create, own, and manage their own digital identity systems. Interoperability and recognition between systems rely on bilateral agreements rather than a central federation authority. This approach offers flexibility but can lead to a fragmented and inconsistent user experience, as exemplified by the United States.
2.4 Self-Asserted Digital Identity
In a self-asserted model, users choose their own digital attributes (such as a username or profile information) without any formal verification against official identity documents. This is the model used by major internet platforms like Facebook and Google. While common for social media and commercial services, no country currently uses this approach as the basis for a national digital identity system due to the lack of identity proofing.
These conceptual models provide a framework for understanding different approaches, but their true implications become clear when examining their application in specific national contexts.
3.0 National Implementations: Case Studies in Strategy and Execution
Examining specific national digital ID systems reveals the practical application of different models and highlights the unique legal, technical, and social challenges each country faces. The strategic choices made during design and implementation have profound consequences for privacy, security, and civic participation. This section provides an in-depth analysis of three distinct national approaches.
3.1 Estonia: The Integrated Digital State
Estonia has developed one of the world's most comprehensive digital societies, underpinned by a mandatory e-ID system for all residents. While built upon a state-issued e-ID, Estonia’s architecture represents a departure from a purely centralized database model, instead incorporating principles of a decentralized data model. This system provides access to an astounding 99% of public services online, from voting to accessing health records. Rather than storing all information in a single database, personal data is kept in separate, distributed databases across different public and private sector organizations.
These disparate systems are securely interconnected via the X-Road, a data exchange platform that encrypts, digitally signs, and logs all transactions. This design incorporates privacy-by-design principles by ensuring data is only shared on a need-to-know basis and in real-time. Crucially, citizens are empowered with a personal data usage log, available through a citizen portal, which allows them to monitor exactly which official or entity has accessed their data and when, fostering a high degree of transparency and accountability.

3.2 India: The Challenge of Scale with Aadhaar
India's Aadhaar program is the largest biometrics-based identification system in the world. As a prime example of the Government-Driven Centralized Systems model, it provides a unique 12-digit identification number (UIN) to residents based on biometric data (ten fingerprints, two iris scans, and facial photograph) and demographic information stored in its Central Identity Repository (CIDR). Aadhaar has been instrumental in expanding access to welfare schemes, financial services, and other essential benefits for a massive population, including many who previously lacked any form of official identification.
However, the scale and mandatory nature of the system raised significant privacy concerns. In a landmark 2017 ruling, the Indian Supreme Court declared privacy to be a fundamental right, leading to subsequent legal and technical adjustments to the Aadhaar framework. In response, the Unique Identification Authority of India (UIDAI) introduced several privacy-enhancing features. These include the Virtual ID, a temporary, 16-digit revocable number that can be used for authentication in place of the permanent Aadhaar number, and tokenization, which prevents different agencies from linking an individual's data across various databases using the Aadhaar number as a common identifier.
3.3 Australia: Public-Private Framework and Vendor Controversy
Australia's approach exemplifies the Semi-Centralized Federated System, with the Digital ID Act 2024 establishing the central trust framework for a national system. The system will be implemented via a phased rollout, with Phase 1 beginning in December 2024 for Commonwealth, state, and territory government entities, and Phase 2 extending to private sector entities by December 2026. The framework is overseen by the Australian Competition and Consumer Commission (ACCC) and the Office of the Australian Information Commissioner (OAIC).
A notable aspect of the Australian ecosystem is the significant role of private vendors, exemplified by the case of AU10TIX. This Israel-based company provides identity verification services for global platforms like X (formerly Twitter), PayPal, and LinkedIn using its "Digital Twins" technology. This reliance on a foreign vendor has sparked controversy over data sovereignty, with concerns that user data could be accessed by foreign intelligence services. These risks were starkly highlighted by a major data breach in which an unsecured AU10TIX admin account exposed the names, birthdates, ID numbers, and ID images of users for 18 months, raising critical questions about the security of centralized, third-party identity verification.
The evolution of these national systems informs and is informed by broader regional frameworks, particularly the ambitious and evolving regulatory landscape of the European Union.
4.0 The European Union's Regulatory Evolution: From Federation to Self-Sovereignty
The European Union has undertaken a significant, multi-stage effort to create a harmonized and interoperable digital identity framework for its 27 member states. This initiative aims to break down digital borders and foster a unified digital single market. This section traces the evolution of the EU's approach, from its initial federated model to a new decentralized, user-centric paradigm.
4.1 The eIDAS 1.0 Regulation (2014): A Federated Foundation
The original eIDAS regulation (EU 910/2014) established a foundational legal and technical framework to enable cross-border authentication for public services. It operated on a federated model, requiring member states to recognize each other's notified national electronic identification (eID) schemes. The technical backbone of this system was the eIDAS-Node infrastructure, a network of nodes that facilitated the secure exchange of authentication requests and identity data between countries.
Despite its ambitions, eIDAS 1.0 faced significant limitations. Its impact was largely confined to the public sector, as private sector adoption was optional. Adoption rates were low, with only 60% of EU citizens having access to a notified eID scheme by 2020. Most importantly, the federated structure meant that national authorities and identity providers retained control over user credentials, failing to provide individuals with direct control over their own personal data.
4.2 eIDAS 2.0 and the EUDI Wallet: The Shift to a Decentralized Model
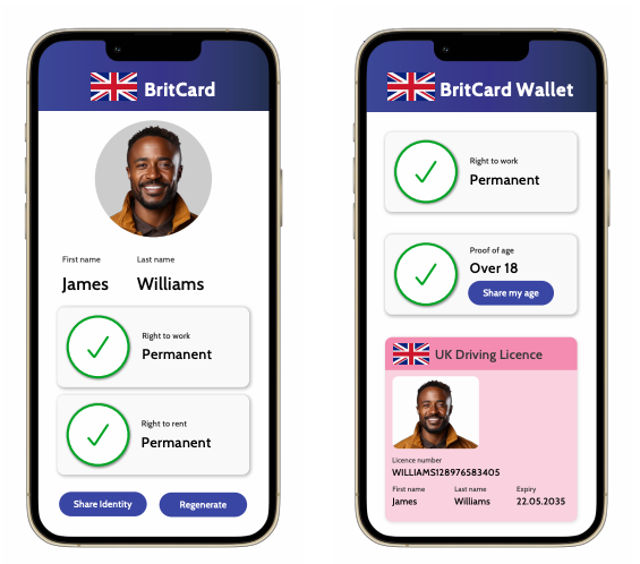
The revised eIDAS 2.0 regulation, which entered into force in May 2024, represents a fundamental paradigm shift towards a user-centric, cryptographically-secured Decentralized Identity model, also known as Self-Sovereign Identity (SSI). This differs from the 'open-market' model by focusing on individual data ownership via digital wallets rather than a multiplicity of uncoordinated identity systems. This SSI model is built on three core technological components: Decentralized Identifiers (DIDs), which are unique identifiers created and controlled by the user; Verifiable Credentials (VCs), which are tamper-evident digital attestations of attributes; and user-controlled Digital Wallets.
The centerpiece of this new framework is the European Digital Identity (EUDI) Wallet, a mobile application that each member state must offer to its citizens. The EUDI Wallet will allow users to securely store, manage, and share their identity attributes and verifiable credentials, giving them full control over their personal data.
Key innovations of eIDAS 2.0 include:
- The introduction of new trust services, such as Qualified Electronic Attestation of Attributes (QEAAs), which allow trusted providers to issue legally recognized VCs.
- The mandatory expansion of the framework to the private sector, requiring large online platforms and other designated services to accept the EUDI Wallet for identification.
- Support for selective disclosure, a critical privacy feature that allows users to share only the minimum data necessary for a transaction—for example, proving they are over 18 without revealing their exact birth date.
The development of these comprehensive identity frameworks is not occurring in a vacuum; they are increasingly being integrated into broader digital policy and content regulation.

5.0 Critical Policy Considerations and Regulatory Frontiers
As digital ID systems become more pervasive, they intersect with other complex regulatory domains and raise fundamental questions about privacy, surveillance, and societal equity. The design and deployment of these systems require navigating a series of difficult trade-offs between utility and individual rights. This section analyzes these critical policy dilemmas.
5.1 The Convergence of Identity and Content Regulation
Digital identity frameworks are increasingly being leveraged to enforce content and age verification mandates online. The UK's Online Safety Act is a primary example, requiring platforms that could host adult content to implement "highly effective" age assurance systems. This creates a de facto requirement for users to verify their identity to access a broad range of legal content on platforms like Reddit and Discord.
The European Union is pursuing a parallel path, with five member states (Italy, Greece, Denmark, France, and Spain) currently testing a "mini-wallet" age verification system. Critics argue that this trend represents a significant threat to online freedom, privacy, and anonymity. Forcing users to link their legal identity to their online activity is seen as creating a "chilling effect" on free expression and building a powerful infrastructure for digital control and mass surveillance.
5.2 Core Policy Dilemmas: Balancing Utility and Rights
The design of any digital ID system involves navigating central tensions between competing policy goals. Striking the right balance is essential to fostering public trust and ensuring these systems empower rather than control citizens.
- Privacy vs. Surveillance: The potential for government and corporate surveillance is a primary concern. The data sovereignty questions raised by vendors like AU10TIX in Australia and T-Systems in the EU highlight the risk of personal data being accessed by third parties. However, these risks can be mitigated through Privacy by Design (PbD) principles and privacy-enhancing technologies. Austria's use of sector-specific PINs (ssPINs), which creates different identifiers for each administrative sector, and India's introduction of Virtual ID and tokenization are practical examples of technologies that prevent the cross-linking of user data and enhance privacy.
- Security and Centralization Risks: Centralized databases of identity information create high-value targets for malicious actors, often referred to as "honeypots." The AU10TIX data breach, where a single unsecured account exposed the sensitive information of users across multiple major platforms, serves as a stark warning of the dangers of this model. In contrast, distributed data architectures, such as Estonia's X-Road system, reduce this risk by avoiding the creation of a single point of failure and keeping data securely stored in separate, purpose-specific databases.
- Inclusion and the Digital Divide: A fundamental challenge is ensuring that digital ID systems are universally accessible and do not create new barriers for marginalized communities. Approximately 1 billion people globally lack any form of official identification, making them "invisible" to both state and commercial services. Systems must be designed inclusively to avoid further marginalizing vulnerable populations such as refugees, the elderly, and those with limited digital literacy or access to technology.
Navigating these dilemmas is crucial as nations build the foundational identity systems for the 21st century.
6.0 Conclusion: Navigating the Future of Digital Identity
This briefing has outlined the key trends shaping the global digital identity landscape. The movement towards comprehensive digital ID is undeniable, driven by the demands of the digital economy and the need for more efficient governance. However, this global trend is marked by significant architectural divergence, with countries adopting centralized, federated, and increasingly decentralized models. The European Union's eIDAS 2.0 regulation and its EUDI Wallet represent the most significant regulatory momentum, pushing the frontier towards a user-centric, self-sovereign identity paradigm.
The central strategic challenge for policymakers is therefore not whether to adopt digital ID, but how to architect it. The choice is between systems that are fundamentally tools of public administration and control, versus those designed as public utilities that empower individual economic and social agency. On one hand is the vision of empowering individuals with greater control, privacy, and agency over their personal data, as exemplified by the SSI model of the EUDI Wallet. On the other is the risk of these same systems being used to enable widespread surveillance, a concern raised by the convergence of digital ID with mandatory age verification for content access.
To ensure that digital identity systems enhance, rather than diminish, individual rights and societal trust, a path forward must be charted with care. This will require robust regulatory oversight, transparent public-private collaboration, and an unwavering commitment to user-centric design principles. The ultimate measure of success will be the creation of identity systems that are inclusive, secure, and fundamentally aligned with the values of a free and open society.