NCA Leads International Operation to Degrade Illegal Versions of Cobalt Strike

Introduction
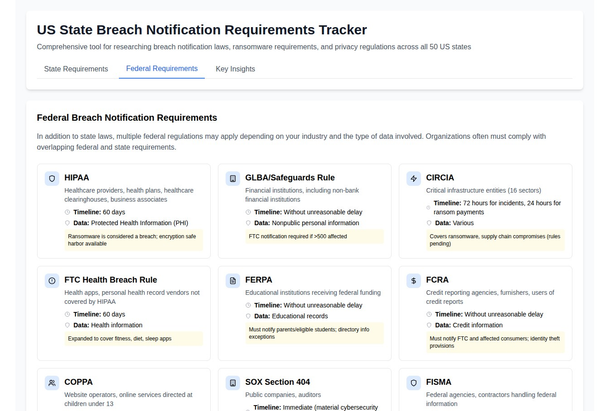
The National Crime Agency (NCA) has spearheaded an extensive international operation aimed at dismantling the illegal use of Cobalt Strike, a legitimate cybersecurity tool often misused by cybercriminals. This operation, involving cooperation with multiple law enforcement agencies worldwide, represents a significant step in the fight against cybercrime. This article explores the details and implications of this groundbreaking operation.
Background on Cobalt Strike
Cobalt Strike is a commercially available tool used by security professionals to simulate cyberattacks and test network defenses. Unfortunately, its powerful features have also made it a favorite among cybercriminals who exploit illegal versions to conduct ransomware attacks, data breaches, and other malicious activities.
The Operation
The NCA, in collaboration with international law enforcement agencies, targeted the infrastructure supporting the illegal distribution and use of Cobalt Strike. This operation involved:
- Intelligence Gathering: The NCA and its partners collected extensive intelligence on the networks and servers used to distribute pirated versions of Cobalt Strike.
- Coordinated Takedown: Multiple jurisdictions were involved in coordinated efforts to seize servers, disrupt communications, and apprehend individuals linked to the illegal activities.
- Legal Actions: Authorities executed search warrants, seized assets, and pursued legal actions against those involved in the distribution and misuse of the tool.
Key Achievements
- Server Seizures: Several key servers used for distributing illegal versions of Cobalt Strike were taken offline, significantly disrupting the cybercriminal operations.
- Arrests and Charges: Multiple individuals were arrested and charged with offenses related to the illegal distribution and use of Cobalt Strike.
- Enhanced Collaboration: This operation highlighted the importance of international cooperation in combating cybercrime, setting a precedent for future collaborative efforts.
Implications for Cybersecurity
The success of this operation has several important implications:
- Deterrence: The takedown of illegal Cobalt Strike infrastructure serves as a strong deterrent to cybercriminals, signaling that international law enforcement agencies are capable of sophisticated cyber operations.
- Improved Security: By disrupting the tools used by cybercriminals, the operation contributes to overall cybersecurity, making it more difficult for malicious actors to execute large-scale attacks.
- Legal Precedents: The legal actions taken during this operation establish important precedents for prosecuting those involved in the illegal distribution of cybersecurity tools.
There have been several instances where cybersecurity tools or "cyber weapons" have been targeted by international law enforcement and cybersecurity communities due to their misuse by cybercriminals. Here are a few notable examples:
1. Emotet
Background: Emotet started as a banking Trojan but evolved into a highly sophisticated and modular malware that was used to distribute other malware like ransomware.
Operation Ladybird: In January 2021, a global law enforcement operation led by Europol and involving agencies from multiple countries succeeded in taking down the Emotet infrastructure. Authorities seized control of the servers and used a coordinated takedown to disrupt the botnet's operations.
Impact: The takedown of Emotet was a significant blow to cybercriminal activities, as Emotet had been a major enabler of various types of cyber attacks.
Sources:
2. NetWalker Ransomware
Background: NetWalker ransomware was known for targeting healthcare organizations, educational institutions, and various businesses, demanding large ransoms for data decryption.
Operation Takedown: In January 2021, the FBI, in coordination with international partners, conducted a significant operation against NetWalker. This included seizing a server used to host NetWalker websites and arresting a Canadian national involved in its operations.
Impact: The operation disrupted NetWalker's infrastructure and showcased the ability of law enforcement to target and dismantle ransomware groups.
Sources:
3. Mirai Botnet
Background: The Mirai botnet, composed of IoT devices, was responsible for some of the largest DDoS attacks in history, including the massive attack on DNS provider Dyn in 2016.
Operation: The creators of Mirai were identified and arrested by the FBI in collaboration with various cybersecurity firms. The source code of Mirai was subsequently leaked, leading to the creation of multiple variants.
Impact: The arrest of the original creators significantly reduced the botnet's activities, although variants continue to pose a threat due to the leaked source code.
Sources:
4. Avalanche Network
Background: Avalanche was a major cybercrime network that hosted a variety of malware campaigns, including banking Trojans and ransomware.
Operation Avalanche: In December 2016, a coordinated effort by Europol, the FBI, and other international law enforcement agencies led to the takedown of the Avalanche network. The operation involved the arrest of suspects and the dismantling of the network's infrastructure.
Impact: The takedown of Avalanche disrupted numerous cybercriminal operations and highlighted the effectiveness of international cooperation in combating cybercrime.
Sources:
5. Hansa and AlphaBay Dark Web Markets
Background: Hansa and AlphaBay were major dark web marketplaces where illegal goods, including hacking tools and stolen data, were traded.
Operation Bayonet: In July 2017, an international law enforcement operation led by the FBI and Europol resulted in the simultaneous takedown of AlphaBay and the undercover operation of Hansa, which was used to gather intelligence on users.
Impact: The takedown of these marketplaces disrupted the distribution of illegal goods and services, including cyber weapons and tools used by cybercriminals.
Sources:
These examples illustrate the concerted efforts of international law enforcement and cybersecurity communities to disrupt the misuse of powerful cybersecurity tools and mitigate their impact on global cybercrime.
Conclusion
The NCA's leadership in this international operation marks a significant victory in the ongoing battle against cybercrime. By targeting the illegal use of Cobalt Strike, the NCA and its partners have not only disrupted a critical tool for cybercriminals but also demonstrated the effectiveness of global cooperation in enhancing cybersecurity. This operation sets a new standard for future efforts to combat the misuse of legitimate cybersecurity tools and protect digital infrastructure worldwide.
For more detailed information, visit the National Crime Agency's news page.