International Cybersecurity Standards

Overview
In an increasingly interconnected world, cybersecurity has become a critical concern for organizations of all sizes and sectors. To address these challenges, various international standards and frameworks have been developed to guide organizations in establishing robust cybersecurity practices. This article explores three prominent cybersecurity standards: ISO/IEC 27001, the NIST Cybersecurity Framework, and CIS Controls. We will delve into their key elements, similarities, and differences, providing a comprehensive understanding of how these frameworks contribute to global cybersecurity resilience.
Key Points
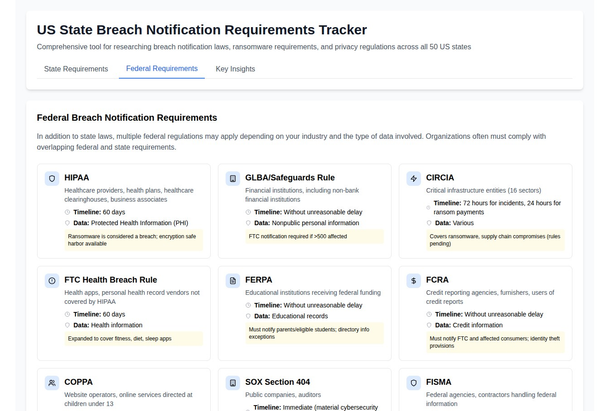
ISO/IEC 27001
ISO/IEC 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability.
- Purpose: To help organizations manage and protect their information assets.
- Scope: Applicable to organizations of all types and sizes.
- Key Elements:
- Risk Management: Identifying, analyzing, and addressing information security risks.
- ISMS: Establishing, implementing, maintaining, and continually improving an ISMS.
- Annex A Controls: 93 controls organized into four sections (A.5 to A.8) covering organizational, physical, technological, and human-related aspects[1][3][4].
NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) is a voluntary framework developed by the National Institute of Standards and Technology (NIST) to help organizations manage and reduce cybersecurity risks.
- Purpose: To provide a policy framework of computer security guidance for how private sector organizations in the U.S. can assess and improve their ability to prevent, detect, and respond to cyber attacks.
- Scope: Primarily used by U.S. federal agencies but applicable to any organization.
- Key Elements:
- Five Functions: Identify, Protect, Detect, Respond, Recover[2][6].
- Core Components: Framework Core, Implementation Tiers, and Profiles.
- Risk-Based Approach: Emphasizes understanding and managing cybersecurity risks in alignment with business needs.
CIS Controls
The CIS Controls (formerly known as the SANS Top 20) are a set of best practices for cybersecurity developed by the Center for Internet Security (CIS).
- Purpose: To provide specific and actionable ways to stop today's most pervasive and dangerous cyber attacks.
- Scope: Applicable to organizations of all sizes and sectors.
- Key Elements:
- 18 Top-Level Controls: Covering areas such as inventory and control of hardware/software, continuous vulnerability management, and incident response[7].
- Implementation Groups (IGs): Help organizations prioritize their implementation efforts based on their size and risk profile.
- Community Consensus: Developed through a collaborative process involving cybersecurity experts worldwide.

Differences and Similarities
Similarities
- Risk Management Focus: All three frameworks emphasize a risk-based approach to cybersecurity, helping organizations identify, assess, and mitigate risks.
- Comprehensive Coverage: Each framework covers a wide range of cybersecurity aspects, from technical controls to organizational policies.
- Global Applicability: While NIST CSF is U.S.-centric, its principles are universally applicable, similar to ISO/IEC 27001 and CIS Controls, which are recognized globally.
Differences
| Feature | ISO/IEC 27001 | NIST CSF | CIS Controls |
|---|---|---|---|
| Scope | International | Primarily U.S. | International |
| Certification | Requires formal certification | Voluntary, no formal certification | Voluntary, no formal certification |
| Structure | Detailed ISMS requirements | High-level framework with five functions | Specific, prioritized controls |
| Technical vs. Operational | More operational, less technical | Balanced between technical and operational | Highly technical and prescriptive |
| Cost | Higher due to certification audits | Lower, flexible implementation | Lower, flexible implementation |
Conclusion
ISO/IEC 27001, NIST Cybersecurity Framework, and CIS Controls each offer valuable guidance for enhancing cybersecurity. Organizations can choose the framework that best fits their needs or even integrate elements from multiple frameworks to build a robust cybersecurity posture. By understanding and implementing these standards, organizations can better protect their information assets and contribute to global cybersecurity resilience.
Diagrams
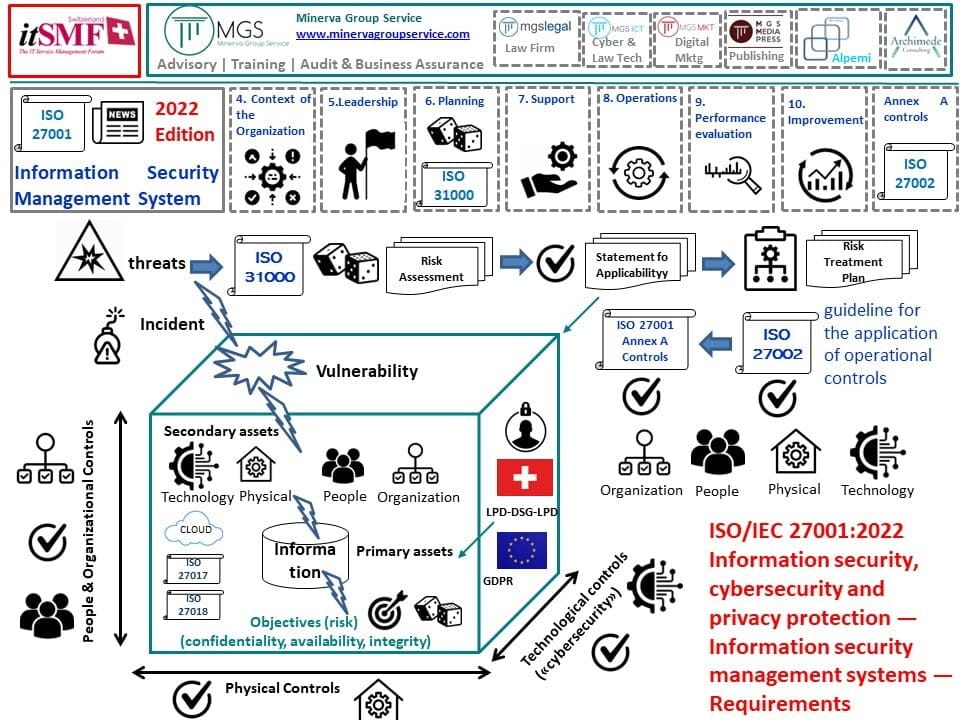
ISO/IEC 27001 Framework
+-----------------------------+
| ISO/IEC 27001 |
+-----------------------------+
| 1. Context of the Organization|
| 2. Leadership |
| 3. Planning |
| 4. Support |
| 5. Operation |
| 6. Performance Evaluation |
| 7. Improvement |
+-----------------------------+
NIST Cybersecurity Framework Functions
+-----------------------------+
| NIST Cybersecurity |
| Framework |
+-----------------------------+
| 1. Identify |
| 2. Protect |
| 3. Detect |
| 4. Respond |
| 5. Recover |
+-----------------------------+
CIS Controls Overview
+-----------------------------+
| CIS Controls |
+-----------------------------+
| 1. Inventory and Control |
| of Hardware Assets |
| 2. Inventory and Control |
| of Software Assets |
| 3. Continuous Vulnerability |
| Management |
| 4. Controlled Use of |
| Administrative Privileges|
| ... |
| 18. Penetration Testing |
| and Red Team Exercises |
+-----------------------------+
By leveraging these frameworks, organizations can systematically improve their cybersecurity measures, ensuring a more secure and resilient digital environment.
Documents and information on various international cybersecurity standards:
ISO/IEC 27001:2022 - Information Security Management Systems
- ISO/IEC 27001:2022 Handbook: This handbook provides comprehensive guidance on establishing and maintaining an Information Security Management System (ISMS) as per ISO/IEC 27001:2022.
The CSF 1.1 Five Functions | NIST
- NIST Cybersecurity Framework: This framework includes five core functions: Identify, Protect, Detect, Respond, and Recover, which provide a high-level, strategic view of an organization's management of cybersecurity risk.
ISO 27001 Requirements - Free Overview - ISMS.online
- ISMS.online: This resource provides a detailed overview of ISO 27001 requirements, including preloaded policies and controls to help organizations achieve compliance.
What is ISO 27001? A detailed and straightforward guide - Advisera
- Advisera Guide: This guide offers a detailed explanation of ISO 27001, its importance, purpose, and requirements, along with practical advice on implementation.
CIS Critical Security Controls
- CIS Controls: A set of best practices for cybersecurity, developed through a community consensus process, aimed at helping organizations protect against cyber threats.
These resources provide comprehensive information and practical guidance on implementing and maintaining robust cybersecurity practices in line with international standards.
Citations:
[1] https://www.iso.org/standard/27001
[2] https://www.nist.gov/cyberframework/getting-started/online-learning/five-functions
[3] https://www.isms.online/iso-27001/requirements/
[4] https://advisera.com/27001academy/what-is-iso-27001/
[5] https://secureframe.com/hub/iso-27001/what-is-iso-27001
[6] https://www.nist.gov/cyberframework
[7] https://www.cisecurity.org/controls
[8] https://hitachi-systems-security.com/nist-cis-sans-20-iso-27001-simplifying-security-control-assessments/
[9] https://www.onetrust.com/blog/iso-27001-vs-nist-cybersecurity-framework/