Germany Completes NIS2 Implementation: A Watershed Moment for European Cybersecurity

The Waiting is Over: Germany's NIS2 Law Takes Effect December 6, 2025
After months of delays, political upheaval, and mounting pressure from Brussels, Germany has finally completed its national implementation of the EU's Network and Information Security Directive 2 (NIS2). With the Bundesrat's approval on November 21, 2025, and subsequent publication in the Federal Law Gazette, the law officially takes effect on December 6, 2025 – with no transition period.
For the approximately 29,850 German organizations now in scope, this isn't a soft landing. The clock started ticking immediately, and compliance is mandatory from day one. If you haven't assessed your NIS2 status yet, you're already behind.
Understanding NIS2: Europe's Cybersecurity Game Changer
The NIS2 Directive represents the most comprehensive overhaul of European cybersecurity regulation to date. Adopted by the European Parliament in December 2022, it replaced the original 2016 NIS Directive with significantly expanded scope, stricter requirements, and enforcement mechanisms with real teeth.
What Makes NIS2 Different?
Massive Expansion in Coverage While the original NIS Directive covered approximately 1,000 entities across Europe, NIS2 extends to over 100,000 organizations. In Germany alone, the number jumped from a few thousand to nearly 30,000 entities. The directive now covers 18 critical sectors, adding eight new areas beyond the original directive's focus on energy, transport, healthcare, finance, water, and digital infrastructure.
New sectors under NIS2 include:
- Digital services (cloud providers, data centers, social networks, online marketplaces)
- Manufacturing (including pharmaceuticals, chemicals, medical devices)
- Postal and courier services
- Waste and wastewater management
- Food production and distribution
- Public administration (central and regional)
- Space sector
- Research organizations
Size-Based Thresholds Under the German implementation, organizations must have either:
- 50 or more employees, OR
- Annual turnover and balance sheet total exceeding €10 million
Certain entities like trust service providers, domain name systems (DNS), and telecommunications operators fall under the directive regardless of size.
Severe Financial Penalties NIS2 introduces administrative fines that make GDPR look modest:
- Essential entities: Up to €10 million or 2% of global annual turnover, whichever is higher
- Important entities: Up to €7 million or 1.4% of global annual turnover
Management Accountability Perhaps the most significant shift: cybersecurity is now a boardroom issue. Management bodies are personally liable for compliance failures, with potential consequences including temporary bans from leadership roles. This elevates cybersecurity from a technical IT concern to a core governance and risk management responsibility.
Germany's Rocky Road to Implementation
Germany's journey to NIS2 compliance has been anything but smooth. The EU set an October 17, 2024 deadline for member states to transpose the directive into national law. Germany missed it – by over a year.
Timeline of Delays
- October 2024: Transposition deadline passes with Germany still debating draft legislation
- November 2024: European Commission launches infringement proceedings against 23 member states, including Germany
- May 2025: Commission sends "reasoned opinion" to 19 countries including Germany, escalating pressure
- July 30, 2025: German Cabinet approves draft after change in government
- November 13, 2025: Bundestag passes the NIS2 Implementation Act
- November 21, 2025: Bundesrat approves without amendments
- December 6, 2025: Law officially enters force
The delay stemmed from multiple factors: complex coordination between federal and state authorities, the collapse of the traffic light coalition government, early federal elections scheduled for February 2025, and extensive consultation with industry stakeholders who raised concerns about implementation practicality.
What German Organizations Must Do Now
The German NIS2 Implementation Act (NIS2UmsuCG) fundamentally revises the Federal Office for Information Security Act (BSI Act) and introduces comprehensive cybersecurity obligations across multiple dimensions.
1. Registration Requirements
Organizations falling within scope must register with the joint reporting office established by the BSI (Federal Office for Information Security) and BBK (Federal Office for Civil Protection and Disaster Assistance) within three months of determining they fall under NIS2.
This self-assessment carries weight: by registering, an organization formally declares it believes itself subject to NIS2 obligations. Get this wrong, and you could face enforcement action or penalties.
2. Governance and Management Responsibility
Under Section 38 of the new BSI Act, management bodies must:
- Approve all prescribed risk management measures
- Actively supervise their implementation (not merely delegate)
- Attend mandatory cybersecurity training at least every three years
- Maintain documentation of training participation, including participants, speakers, content, and duration
- Accept personal liability for damages resulting from duty breaches
A simple attendance certificate won't suffice. Organizations need comprehensive documentation proving executives understand their cybersecurity responsibilities and actively oversee implementation.
3. Risk Management Framework
Organizations must establish comprehensive risk management encompassing:
Technical Measures:
- Incident and emergency management capabilities
- Business continuity and disaster recovery planning
- Supply chain security assessments
- Vulnerability management and regular penetration testing
- Multi-factor authentication (MFA) implementation
- Encryption and cryptographic controls
- Network segmentation and access controls
- Security monitoring and SIEM capabilities
Organizational Measures:
- Clear roles and decision-making processes
- Security-by-design in development practices
- Regular effectiveness assessments
- Employee training and awareness programs
- Third-party risk management
- Systematic supplier registries
- Documentation of all security measures
The measures must be proportionate to the organization's risk profile, based on internationally recognized standards (like ISO 27001, IEC 62443, or NIST Cybersecurity Framework), and reflect the current state of the art.
4. Incident Reporting
Germany implements a three-stage incident reporting system for significant cybersecurity incidents:
Stage 1 - Early Warning (24 hours) Within 24 hours of becoming aware of a significant incident, organizations must submit an initial notification containing basic information about the incident.
Stage 2 - Incident Notification (72 hours) Within 72 hours, a detailed report must include the nature of the threat, technical details, potential impact, and mitigation measures taken.
Stage 3 - Final Report (30 days) Within one month, submit a comprehensive final report with root cause analysis, full impact assessment, and corrective actions implemented.
These tight timelines demand robust internal processes, clear escalation paths, and potentially 24/7 monitoring capabilities. The BSI has announced it will provide a digital reporting channel, though details remain forthcoming.
Importantly, NIS2 incident reporting must be coordinated with GDPR breach notifications when personal data is involved, requiring careful process integration.
5. Supply Chain Security
One of NIS2's most challenging requirements involves supply chain management. Organizations must:
- Assess cybersecurity risks from suppliers and service providers
- Implement contractual security requirements
- Establish audit rights over suppliers
- Maintain evidence of supplier compliance
- Manage subcontractor risks
- Create systematic supplier registers
For critical components in essential entities, the German implementation goes beyond NIS2's baseline: the Federal Ministry of the Interior can prohibit the use of specific high-risk components or manufacturers on a risk-based assessment, even for already deployed infrastructure.
6. Documentation and Audit Readiness
The BSI has broad supervisory powers, including:
- Regular audits and security inspections
- Binding instructions for remediation
- On-site examinations
- Requests for documentation at any time
Organizations need comprehensive documentation covering:
- Risk assessments and their methodology
- Security policies and procedures
- Management approvals and oversight activities
- Training records
- Incident response plans and tests
- Supply chain assessments
- Technical control implementations
- Evidence of measure effectiveness
European Context: Where Do Other Countries Stand?
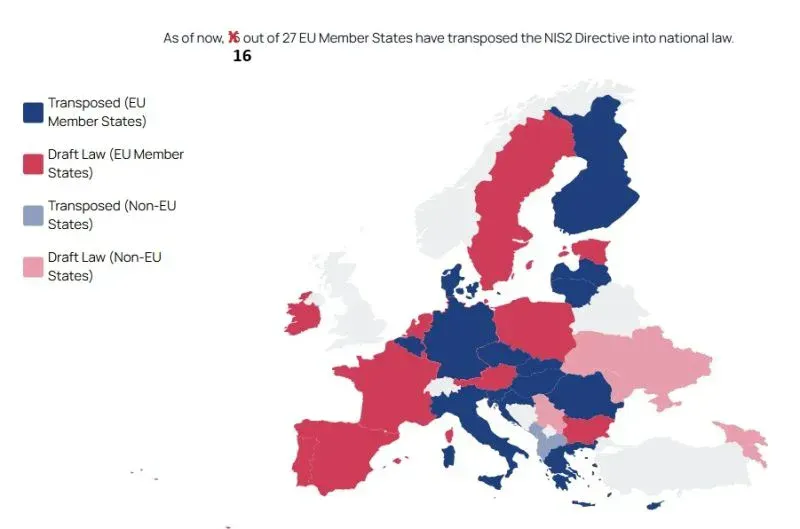
Germany's implementation, while delayed, puts it ahead of several major EU economies. As of December 2025, the transposition landscape looks like this:
Fully Transposed (16 countries): Belgium, Croatia, Cyprus, Czech Republic, Denmark, Finland, Germany, Greece, Hungary, Italy, Latvia, Liechtenstein, Lithuania, Romania, Slovakia, Slovenia
Expected Before Year-End: Malta, Portugal
Still Pending: Austria, Bulgaria, Estonia, France, Ireland, Luxembourg, Netherlands, Poland, Spain, Sweden, plus others
France, the Netherlands, and Spain – three major economies – are among those still working through implementation. This creates a patchwork compliance landscape where multinational organizations face varying requirements and timelines across different member states.
The "Negligible Activities" Debate
One of the most contentious aspects of Germany's implementation is the "negligible activities" clause in Section 28(3) of the new BSI Act. This provision allows companies to exclude business activities that are "negligible" compared to their overall operations when determining if they fall under NIS2.
The Promise and the Problem
On its face, this seems beneficial. A manufacturing company that provides cloud services only to internal users, or a logistics firm that operates a small e-commerce platform as a side business, shouldn't face full NIS2 compliance for activities representing a tiny fraction of their operations.
The problem? The law provides no clear definition of "negligible." The explanatory memorandum offers non-binding indicators like:
- Employee counts in specific activities
- Revenue percentages
- Whether the activity appears in company statutes
But it ultimately defers to an undefined "overall picture" assessment. This creates significant legal uncertainty. Companies must conduct their own carefully documented risk assessments to determine applicability – and their conclusions might differ from the BSI's interpretation during an audit.
Practical Steps: What To Do This Week
If you're potentially in scope for NIS2, here's your immediate action plan:
1. Conduct a Scope Assessment (This Week)
- Review your organization's size (employees, revenue, balance sheet)
- Identify which NIS2 sectors you operate in
- Assess if your activities in those sectors are "negligible"
- Document your methodology and conclusions
- Consider engaging legal counsel for borderline cases
2. Establish Executive Awareness (This Month)
- Brief your management board on NIS2 requirements
- Clarify personal liability implications
- Establish governance structures for cybersecurity oversight
- Schedule initial management training
3. Gap Analysis (Next 30 Days)
- Assess current cybersecurity posture against NIS2 requirements
- Identify technical and organizational gaps
- Prioritize remediation based on risk and compliance urgency
- Budget for necessary investments
4. Registration Planning (Within 90 Days)
- Prepare registration documentation
- Identify your designated contact persons
- Set up internal processes for maintaining registration information
- Submit registration to BSI/BBK joint office
5. Build Your Compliance Program (Months 2-6)
- Develop or update your information security management system
- Implement required technical controls
- Establish incident response and reporting procedures
- Create supply chain assessment processes
- Document everything comprehensively
The Broader Implications
Germany's implementation marks more than a regulatory milestone – it signals a fundamental shift in how cybersecurity is approached across Europe.
Cybersecurity as Business Strategy
With management liability and severe financial penalties, cybersecurity can no longer be treated as an IT problem solved by technical teams in isolation. It's now a strategic business risk requiring board-level attention, resource allocation, and ongoing governance.
Supply Chain Transparency
The supply chain security requirements will ripple through the economy. Suppliers to NIS2-covered entities will face indirect compliance pressures through contractual requirements, even if they don't directly fall under the directive. This creates a multiplier effect extending far beyond the 100,000+ directly covered entities.
Market Consolidation and Costs
The cybersecurity services market is already strained. With Germany's 29,850 entities now scrambling for compliance support simultaneously, expect:
- Surging demand for cybersecurity consultants and vCISOs
- Premium pricing for NIS2 gap assessments and implementation support
- Potential delays in accessing qualified service providers
- Competitive advantage for organizations that started preparation early
Regulatory Evolution
NIS2 isn't operating in isolation. It intersects with:
- GDPR: Data protection and breach notification coordination
- DORA: Digital Operational Resilience Act for financial services
- CER Directive: Critical Entities Resilience directive
- AI Act: Upcoming requirements for AI system security
- Cyber Resilience Act: Product security requirements
Organizations need integrated compliance approaches spanning this regulatory ecosystem.
International Competitiveness
While some industry voices warned that NIS2 would create compliance burdens harming competitiveness, supporters argue the opposite: in an era of escalating cyber threats, state-sponsored attacks, and ransomware epidemics, robust cybersecurity isn't optional – it's a competitive necessity.
The German government estimates NIS2 will prevent approximately €3.6 billion in annual economic losses – roughly €250,000 per affected company. This doesn't account for prevented reputational damage, business disruption, or the systemic stability benefits of a more resilient digital infrastructure.
Looking Ahead: 2026 and Beyond
With the law now in force, 2026 will be the year of implementation. Key milestones to watch:
Q1 2026:
- BSI releases detailed technical guidance
- Registration portal becomes fully operational
- First wave of compliance audits begins
Q2 2026:
- Essential entities complete initial registrations
- First enforcement actions likely for clear non-compliance
- Industry working groups emerge sharing best practices
Q3-Q4 2026:
- BSI begins systematic audit program
- Initial case law develops around "negligible activities" interpretation
- Clarification on critical component restrictions
2027 and Beyond:
- Highly critical entities must provide evidence of compliance (deadline set by BSI at registration, minimum 3 years after law effective)
- Ongoing three-year audit cycles begin
- Potential amendments based on implementation experience
The Bottom Line
Germany's NIS2 implementation isn't just another compliance exercise – it's a fundamental restructuring of how organizations approach cybersecurity. The immediate effective date with no transition period sends a clear message: cybersecurity is no longer a "nice to have" but a regulated, mandatory business function with severe consequences for failure.
For organizations in scope, the path forward requires:
- Immediate action on scope assessment and gap analysis
- Executive engagement treating this as a governance priority
- Substantial investment in technical controls and organizational capabilities
- Ongoing commitment to continuous monitoring and improvement
The organizations that thrive won't be those that grudgingly comply with minimum requirements, but those that recognize NIS2 as an opportunity to build genuine cyber resilience – a strategic asset in an increasingly dangerous digital landscape.
Related Resources from ComplianceHub.wiki
For deeper technical guidance and implementation strategies, explore these comprehensive articles from our compliance knowledge base:
Technical Implementation Guidance:
- Navigating NIS2 Compliance: A Deep Dive into ENISA's Technical Implementation Guidance - Comprehensive breakdown of the 13 technical requirements with practical implementation advice
Foundational Overview:
- NIS2 Directive Guide: EU Cybersecurity Compliance Requirements - Essential guide covering scope, entity classifications, and core requirements
Country-Specific Implementations:
- Ireland's NIS 2 Implementation: A Practical Roadmap - How Ireland's National Cybersecurity Centre translated EU requirements into actionable guidance
- Navigating Sweden's New Cyber Horizon: Cybersäkerhetslagen Deep Dive - Sweden's January 2026 implementation and NATO alignment considerations
- Spain Cybersecurity Guide: GDPR & LOPDGDD Compliance - Spain's NIS2 transposition and coordination with data protection laws
Threat Landscape Analysis:
- Understanding the Evolving Cybersecurity Threat Landscape in the EU - ENISA's first-ever State of Cybersecurity report analysis with sector-specific threat intelligence
Broader Compliance Context:
- EU's Cybersecurity Landscape in 2025 - How NIS2 fits with DORA, Cyber Resilience Act, and AI Act requirements
Dutch Translation:
- Navigeren door NIS2: Uw Praktische Gids voor Technische Cyberbeveiliging - Complete NIS2 technical implementation guide in Dutch
Additional Resources and Next Steps
Regulatory Authorities:
- BSI (Federal Office for Information Security): https://www.bsi.bund.de
- BSI NIS2 Information Portal: (forthcoming)
- EU NIS2 Directive Official Text: EUR-Lex 32022L2555
- ENISA NIS2 Resources: https://www.enisa.europa.eu/topics/cybersecurity-policy/nis-directive-new
Compliance Frameworks:
- NIST Cybersecurity Framework 2.0
- ISO/IEC 27001:2022
- IEC 62443 (for OT/industrial security)
- CyFun Framework 2025 (NIS2-specific self-assessment)
Professional Support:
- Engage qualified vCISO services for compliance oversight
- Conduct third-party gap assessments
- Consider joining industry peer groups for knowledge sharing
- Consult legal counsel for scope determination and liability issues
The era of mandatory, enforceable cybersecurity standards has arrived in Germany. The question isn't whether to comply – it's how quickly and effectively you can build the capabilities required to meet this new reality.
This article was prepared on December 5, 2025, immediately following Germany's official NIS2 implementation. Organizations should monitor the BSI website for ongoing guidance updates and regulatory clarifications as implementation proceeds.