France's Encryption War Escalates: GrapheneOS Exodus Signals Dangerous Precedent for Open Source Privacy Tech

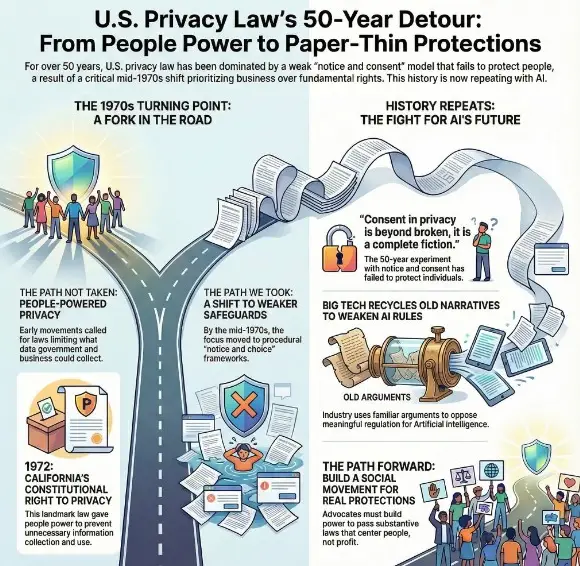
Executive Summary: The GrapheneOS project's dramatic withdrawal from France in November 2025 represents a watershed moment in the escalating global conflict between privacy technology and state surveillance powers. This case follows an established pattern of French law enforcement targeting encrypted communications platforms, but marks the first time authorities have directly threatened an open-source privacy project with prosecution for refusing to implement backdoors—a move that could fundamentally reshape how security software is developed and distributed worldwide.
The GrapheneOS Crisis: What Happened
In late November 2025, GrapheneOS—a nonprofit open-source Android-based operating system focused on security and privacy—announced it was ceasing all operations in France, migrating infrastructure away from French hosting provider OVH to servers in Canada and Germany. The project declared that France is no longer a safe place for open source privacy projects.
The crisis began when French media outlet Le Parisien published articles characterizing GrapheneOS as a tool enabling criminal activity. French cybercrime prosecutor Johanna Brousse stated in an interview that authorities would pursue legal action against platforms with criminal organization ties if they refuse cooperation.
According to GrapheneOS developers, French authorities threatened arrests and server seizures similar to actions taken against SkyECC and EncroChat—previous encrypted communication networks that were dismantled through aggressive law enforcement operations.
The Technical Impossibility Defense
GrapheneOS developers emphasized a critical technical reality: they cannot simply unlock specific devices because GrapheneOS security relies on hardware-backed features in Google Pixel phones' Titan M2 security chips, making backdoor implementation require breaking security for all users.
The project's security features include:
- Hardware-backed encryption using Google Pixel's Titan M2 security chip
- Automatic partition reset to encrypted state after device lock
- Destructive PIN functionality that erases all data upon entry
- No cloud infrastructure for signing or builds that could be compromised
Media Conflation and Misinformation
GrapheneOS representatives argue that French media conflated their legitimate open-source project with government-sponsored forks and commercial products built on GrapheneOS code. The articles referenced features like fake Snapchat apps, dark web advertising, and unlisted YouTube videos—none of which are part of the official GrapheneOS project.
French security authorities have issued investigation reports suggesting GrapheneOS use is inherently suspicious because it demonstrates an "intention to conceal", a characterization that privacy advocates view as criminalizing legitimate security practices.
France's Pattern: A History of Aggressive Encryption Takedowns
The threats against GrapheneOS must be understood within France's established pattern of aggressive action against encrypted communications platforms. This isn't the first time French authorities have targeted encryption technology—it's part of a systematic campaign.
EncroChat: The Blueprint for Crypto-Network Takedowns
In 2020, French and Dutch authorities infiltrated EncroChat's encrypted messaging service, intercepting over 115 million conversations among more than 60,000 users. The operation resulted in 6,558 arrests worldwide and seizure of $985 million in illicit proceeds.
French National Gendarmerie discovered EncroChat in 2017 during organized crime operations and, after obtaining judicial authorization in January 2020, placed a "technical tool" on EncroChat's servers in France. The malware allowed them to read messages before encryption and record lock screen passwords.
EncroChat was a commercial service selling modified phones with encryption specifically to criminal networks, charging approximately $1,000 per device plus $1,500 for six-month subscriptions with 24/7 support.

SkyECC: The Follow-Up Operation
When EncroChat collapsed, many users migrated to Sky ECC. Belgian and Dutch police, in cooperation with French authorities, infiltrated Sky ECC in early 2021, monitoring communications of 170,000 global users and intercepting 3 million messages daily.
The operation demonstrated law enforcement's ability to pivot quickly to new platforms, with French police gathering data from Sky ECC phones worldwide and providing it to law enforcement agencies in other countries.
The Telegram Precedent: Targeting Tech Leaders
France's arrest of Telegram founder Pavel Durov in August 2024 created another flashpoint in this conflict. As detailed in our previous coverage on Telegram security, Durov was arrested as part of an investigation into alleged criminal activities on Telegram and lack of cooperation with law enforcement, though he was not charged with any crime.
This arrest mirrored the logic used against GrapheneOS, signaling a strategic shift in how French authorities approach dual-use technologies. The message was clear: platform operators who enable encrypted communications could face personal liability.

The Critical Distinction: Commercial vs. Open Source
The GrapheneOS case represents a dangerous evolution in enforcement tactics. Unlike EncroChat and Sky ECC—commercial enterprises that sold expensive, modified hardware specifically marketed to criminal networks—GrapheneOS is a free, open-source project available to anyone concerned about privacy.
As community members argued, EncroChat was a commercial enterprise selling products specifically marketed to criminals with promises of impunity, while GrapheneOS is a nonprofit foundation maintaining free and open-source software.
This distinction is fundamental. GrapheneOS developers compared accusations of aiding criminals to "considering knife manufacturers accomplices to crimes"—the absurdity of holding tool creators responsible for all user actions.
The False Equivalence Problem
French authorities sent internal messages to police forces labeling all Google Pixel phones with GrapheneOS as inherently suspicious, leading to a wave of uncritical media coverage that repeated these claims as fact.
The project emphasizes it:
- Does not engage in commercial activities
- Does not sell or distribute systems on darknet forums
- Does not market to criminal organizations
- Allows anyone to freely download firmware
- Has no relationship with commercial forks using their code
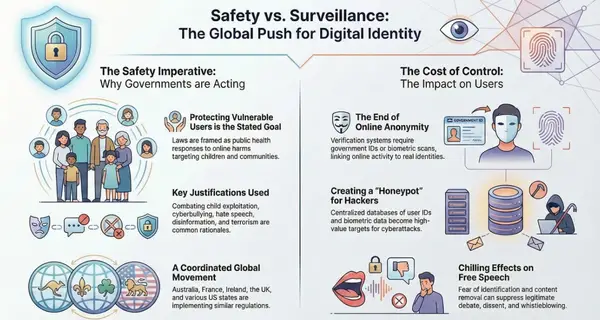
The EU Chat Control Context: A Broader Surveillance Push
France's actions against GrapheneOS must be understood within the broader context of European surveillance expansion, particularly the controversial "Chat Control" proposal.
Chat Control: The Encryption Backdoor Legislation
As we've extensively covered on Compliance Hub Wiki, the EU's Child Sexual Abuse Material (CSAM) regulation—known as "Chat Control"—has failed three times to pass after facing blocking minorities led by Germany and other member states.
The proposal would mandate message scanning and encryption backdoors, with major platforms including Signal, Telegram, WhatsApp/Meta, and Apple threatening to exit the EU market rather than implement such measures.
Over 500 cryptography experts and security researchers signed an open letter warning that Chat Control is "technically infeasible" and would create catastrophic security vulnerabilities.
France's Role in Surveillance Expansion
GrapheneOS specifically cited France's support for Chat Control as reinforcing their decision to leave, stating their "simple heuristic for the EU is avoiding countries supporting Chat Control".
France has consistently pushed for stronger surveillance capabilities and weaker encryption protections, positioning itself at the forefront of EU member states seeking to mandate law enforcement access to encrypted communications.
Global Regulatory Fragmentation: Implications for Compliance
This situation highlights the growing complexity of the global privacy and encryption regulatory landscape, as detailed in our 2025 Global Digital Privacy briefing.
Jurisdictional Conflicts
Organizations developing privacy technology now face contradictory requirements:
- France and some EU members: Demanding encryption backdoors or lawful access capabilities
- United States: Generally protecting strong encryption (with some exceptions)
- Canada, Germany, Netherlands: Supporting robust encryption standards
- Other jurisdictions: Varying positions creating compliance uncertainty
The "Brussels Effect" in Reverse
Typically, EU regulations set global standards through the "Brussels Effect." However, Chat Control's repeated failures reduce pressure for similar legislation in other jurisdictions, potentially limiting the expansion of mandatory encryption weakening globally.
Compliance Challenges for Organizations
For compliance professionals, this creates unprecedented challenges:
Risk Assessment Considerations:
- Geographic distribution of infrastructure
- Jurisdictional exposure to conflicting encryption requirements
- Third-party vendor locations and legal obligations
- Cross-border data transfer implications
Strategic Questions:
- Can you maintain strong encryption while operating in France?
- What triggers "cooperation" obligations with law enforcement?
- How do you document inability to decrypt user data?
- What legal protections exist for refusing technically impossible demands?
Technical Implications: Can You Build Truly Secure Systems?
The GrapheneOS situation raises fundamental questions about whether it's possible to build secure systems that satisfy both privacy requirements and law enforcement demands.
The Backdoor Paradox
Security experts universally recognize that encryption backdoors create vulnerabilities exploitable by both legitimate authorities and malicious actors. Independent analyses, including the European Parliament's own assessment, raised concerns about technical reliability of detection technologies, noting high false-positive rates and misidentification risks.
Once a backdoor exists:
- It can be discovered by sophisticated attackers
- It creates a single point of failure
- It undermines the fundamental security model
- It makes all users less secure, not just targets of investigation
Hardware-Backed Security as Protection
GrapheneOS security relies on hardware-backed features in Google Pixel phones' Titan M2 security chips, and bypassing brute-force protections would require breaking the security model for every user.
This hardware-level implementation provides a defense against demands for selective backdoors—the technology simply doesn't support such capabilities without comprehensive redesign that would eliminate security for all users.
Legal and Ethical Frameworks: Where Do We Draw Lines?
The Criminal Enterprise vs. Tool Provider Distinction
The legal theory underlying prosecution of GrapheneOS would be unprecedented. Historically, tool providers have not been held liable for criminal misuse of their products unless:
- They actively marketed to criminals
- They knowingly facilitated specific criminal acts
- They refused legitimate lawful access requests within technical capabilities
- They operated as criminal enterprises themselves
GrapheneOS meets none of these criteria. It's an open-source project that:
- Makes its code freely available for audit
- Operates transparently as a nonprofit
- Does not market to any specific audience
- Cannot technically provide the access being demanded
Comparison to Other Dual-Use Technologies
Consider the precedents:
- Tor: Enables anonymous communication, used by both activists and criminals—developers not prosecuted
- Signal: Provides end-to-end encryption, used globally—operates legally despite criminal use cases
- VPN Services: Enable privacy and circumvention—generally legal despite misuse
- Encryption Libraries: OpenSSL, GnuPG, etc.—foundational security tools used universally
Prosecuting GrapheneOS would establish a precedent requiring all security tool developers to implement backdoors or face legal jeopardy.
Industry Response and Exodus Risk
The Chilling Effect on Innovation
GrapheneOS announced developers are now prohibited from traveling to or working in France due to security concerns. This creates a chilling effect on:
- Open-source security research
- Privacy technology development
- Academic collaboration on encryption
- Conference attendance and knowledge sharing
Infrastructure Migration Trends
GrapheneOS's migration follows a pattern:
- Mastodon, Discourse, Matrix servers: Moved to Toronto, Canada
- Website infrastructure: Transferred to Netcup in Germany
- DNS services: Migrated to Vultr and BuyVM
- Cryptographic credentials: Rotated as security precaution
The developers confirmed no confidential user data or critical security infrastructure was stored in France, so core security features remain unaffected.
Other Platforms Taking Notice
Major platforms including Signal, Telegram, WhatsApp/Meta, and Apple have maintained firm positions against implementing backdoors, with some threatening EU market exit.
The GrapheneOS case provides a concrete example of the risks privacy-focused technology companies face in certain jurisdictions.
Compliance Recommendations: Navigating the New Reality
For Organizations Developing Privacy Technology
Immediate Actions:
- Geographic Risk Assessment: Evaluate infrastructure locations against jurisdictional threats
- Legal Entity Structure: Consider separation of development, operations, and infrastructure across favorable jurisdictions
- Technical Architecture: Design systems that genuinely cannot provide backdoor access (hardware-backed security, zero-knowledge designs)
- Documentation: Maintain clear records of technical impossibility for certain requests
- Incident Response: Develop plans for jurisdictional threats including rapid migration capabilities
Strategic Considerations:
- Avoid France for critical infrastructure if you develop strong encryption or privacy tools
- Monitor Chat Control developments as they signal broader EU direction
- Establish presence in supportive jurisdictions (Canada, Germany, Netherlands, U.S.)
- Build migration capabilities allowing rapid infrastructure relocation
- Document technical limitations clearly for legal proceedings
For Organizations Using Privacy Technology
Due Diligence Questions:
- Where is the provider's infrastructure located?
- What jurisdictions govern their operations?
- Can they technically access your encrypted data?
- What happens if they receive government demands?
- Do they have infrastructure migration plans?
Risk Mitigation:
- Prefer providers in jurisdictions with strong encryption protection
- Understand technical architecture ensuring true end-to-end encryption
- Monitor regulatory developments in provider jurisdictions
- Have backup communication channels using different providers/jurisdictions
The Broader Implications: Digital Rights in Democratic Societies
The Privacy vs. Security False Dichotomy
French authorities frame this as necessary for combating serious crime. However, security experts argue this presents a false choice. Strong encryption:
- Protects critical infrastructure from adversaries
- Secures financial transactions and commerce
- Enables whistleblowers and journalists
- Protects activists in authoritarian regimes
- Safeguards personal privacy and dignity
Weakening encryption for law enforcement access weakens it for everyone, creating vulnerabilities that hostile nations, cybercriminals, and malicious actors will exploit.
The Slippery Slope Concern
Law enforcement's rhetoric equates sophisticated encryption with suspicious behavior and "intention to conceal," treating privacy tools as inherently suspect.
This logic pathway leads to:
- Criminalizing privacy-preserving technologies
- Treating security-conscious behavior as evidence of wrongdoing
- Eroding presumption of innocence
- Establishing surveillance as default rather than exception
Democratic Oversight Questions
The GrapheneOS case raises critical democratic governance questions:
- Should law enforcement determine what security technologies are permitted?
- Can demands for technically impossible access be legally enforced?
- What oversight exists for state surveillance capabilities?
- How do we balance legitimate security needs with fundamental rights?
Connections to Broader Tech Regulation Battles
The Encryption Wars Historical Context
This represents the latest chapter in decades-long "Crypto Wars":
- 1990s: U.S. export restrictions on strong encryption
- 2015: FBI vs. Apple iPhone backdoor dispute
- 2016: WhatsApp end-to-end encryption controversy
- 2020s: EU Chat Control and similar proposals globally
Each iteration sees law enforcement argue technology enables crime, while security experts warn that weakening encryption creates greater risks.
Related Regulatory Pressures
As covered in our Cybersecurity Frontlines analysis, organizations face mounting regulatory complexity:
- EU AI Act: Comprehensive AI governance with significant penalties
- DORA: Digital operational resilience for financial sector
- NIS2: Expanded cybersecurity requirements across critical sectors
- Data Act: New data access and portability requirements
The GrapheneOS situation adds another dimension to this already complex compliance landscape.
What Happens Next: Predictions and Preparations
Likely Short-Term Developments
Within 6 Months:
- France may attempt enforcement actions against GrapheneOS despite infrastructure migration
- Other EU member states may clarify positions on similar demands
- Chat Control likely returns in modified form under different presidency
- Additional privacy technology providers may relocate from France
Within 1-2 Years:
- Legal challenges in European courts regarding encryption backdoor demands
- Potential EU-wide framework attempting to resolve conflicting national approaches
- Increased jurisdictional fragmentation for privacy technology providers
- Possible transatlantic tensions over encryption policy divergence
Long-Term Trajectory
The fundamental tension between strong encryption and law enforcement access remains unresolved. Possible outcomes include:
Scenario 1: Encryption Prevails
- Technical impossibility arguments succeed in courts
- Democratic oversight prevents backdoor mandates
- Privacy technology continues developing freely
- Law enforcement adapts investigation techniques
Scenario 2: Jurisdictional Fragmentation
- Some jurisdictions mandate backdoors, others protect encryption
- Technology providers cluster in supportive jurisdictions
- Users in restrictive jurisdictions lose access to strong security
- Global internet fragments along regulatory lines
Scenario 3: Compromise Framework
- New legal frameworks distinguish legitimate privacy from criminal enablement
- Technical standards emerge allowing targeted lawful access without universal backdoors
- Enhanced oversight mechanisms balance security needs with rights protection
- International cooperation produces workable standards
Conclusions and Compliance Takeaways
The GrapheneOS exodus from France represents far more than one organization relocating servers. It signals a critical inflection point in the global debate over encryption, privacy, and state surveillance powers.
Key Lessons for Compliance Professionals
- Geographic jurisdiction matters profoundly for privacy technology operations
- Technical architecture decisions have legal implications (hardware-backed security as defense)
- Open-source projects face unique risks despite lack of commercial relationships
- Regulatory fragmentation is accelerating across privacy and encryption domains
- Documentation of technical impossibility provides critical legal protection
Strategic Imperatives
Organizations must:
- Assess jurisdictional exposure for all infrastructure and operations
- Monitor regulatory developments in France and broader EU regarding encryption
- Develop contingency plans for rapid infrastructure migration if needed
- Document technical architecture clearly regarding encryption capabilities
- Engage in policy advocacy to shape reasonable regulatory approaches
The Broader Stakes
This isn't just about GrapheneOS or even just encryption—it's about whether democratic societies will preserve space for privacy-enhancing technologies in an era of expanding surveillance powers.
By pulling infrastructure from France, GrapheneOS makes a larger statement about the shrinking space for privacy technology within Europe. The question is whether other jurisdictions will follow France's aggressive approach or establish themselves as havens for privacy innovation.
For compliance professionals navigating this landscape, the message is clear: geographic strategy, technical architecture, and legal preparedness are now essential components of privacy technology compliance. The days of assuming consistent global standards for encryption and privacy tools have ended—if they ever truly existed.
Additional Resources
Related Coverage from Our Network:
- EU Chat Control Fails Again - Detailed analysis of encryption backdoor proposal defeats
- 2025 Global Digital Privacy Landscape - Comprehensive regulatory overview
- Telegram Security Guide - Context on Durov arrest and platform security
- Cybersecurity Legal Battles - Broader enforcement landscape
External Resources:
- GrapheneOS Official Statement: grapheneos.social
- Privacy Guides Analysis: privacyguides.org
- EU Chat Control Opposition: chatkontrolle-stoppen.eu
This analysis is current as of November 26, 2025. For compliance guidance specific to your organization's situation, consult with legal counsel familiar with encryption law and cross-border technology regulation.