Cybersecurity Baseline Self-Assessment: A Comprehensive Framework Approach
Overview
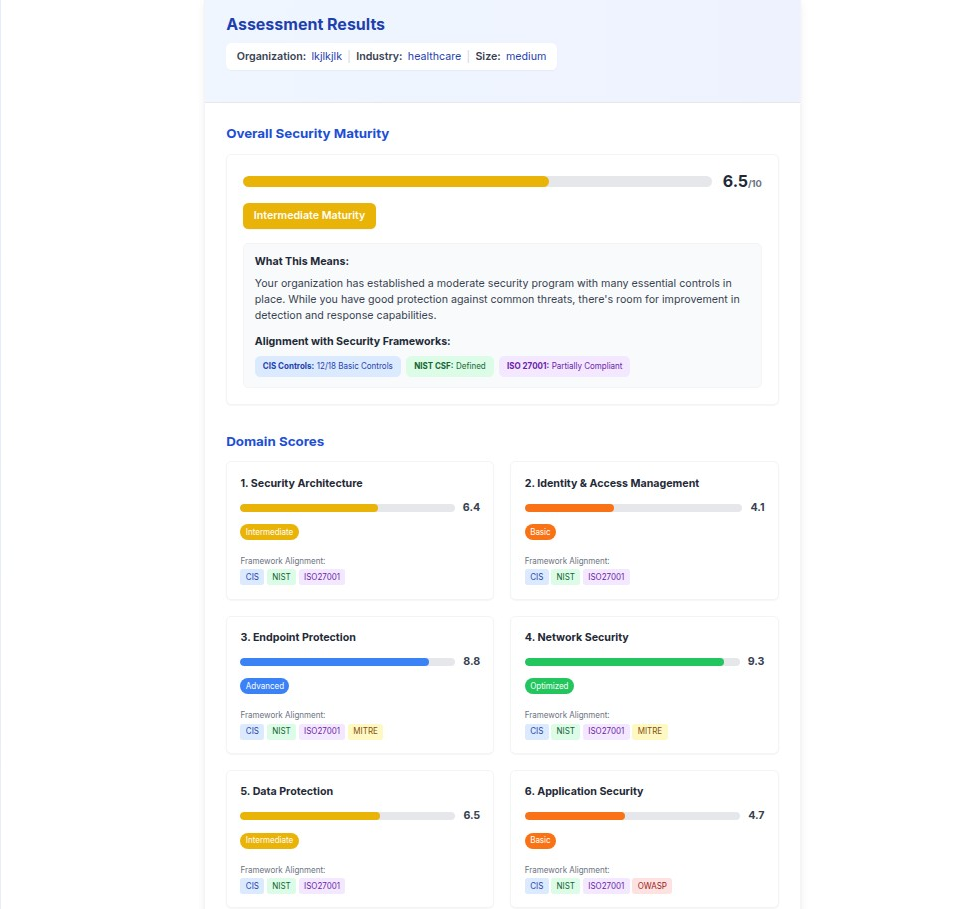
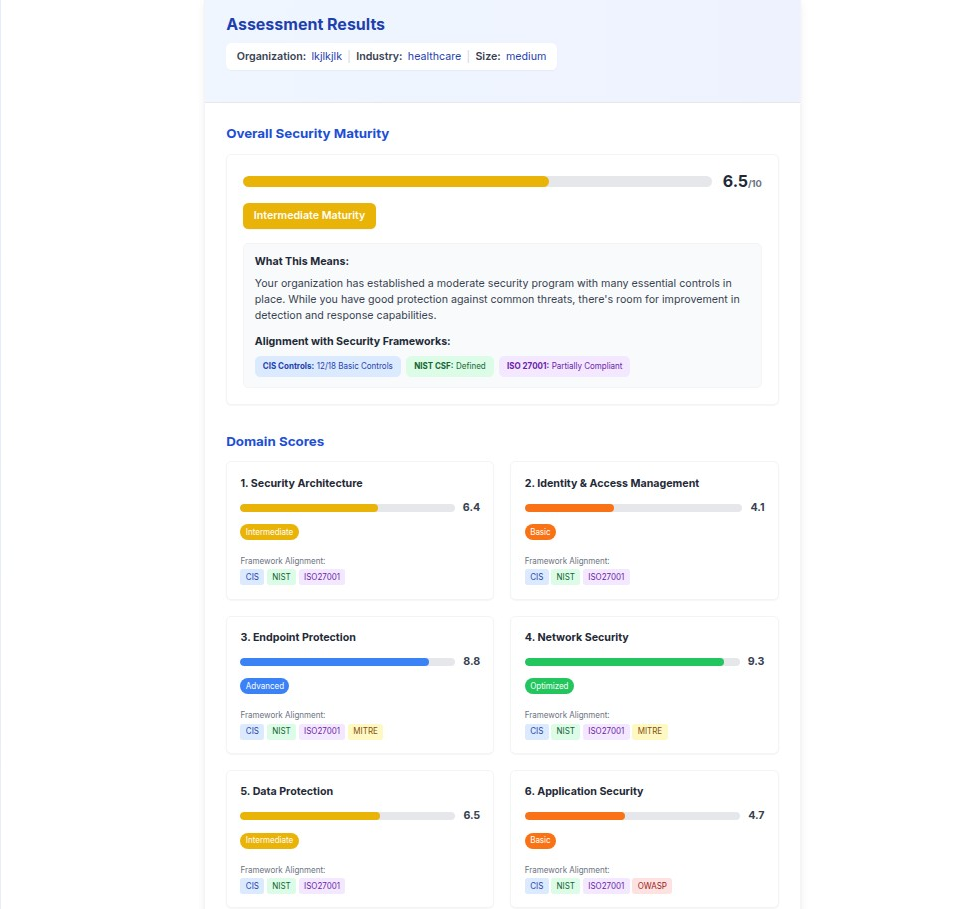
A cybersecurity baseline self-assessment is a structured evaluation tool that helps organizations understand their current security posture and identify areas for improvement. This assessment methodology provides actionable recommendations aligned with industry-standard frameworks to enhance an organization's cybersecurity maturity.

Assessment Structure
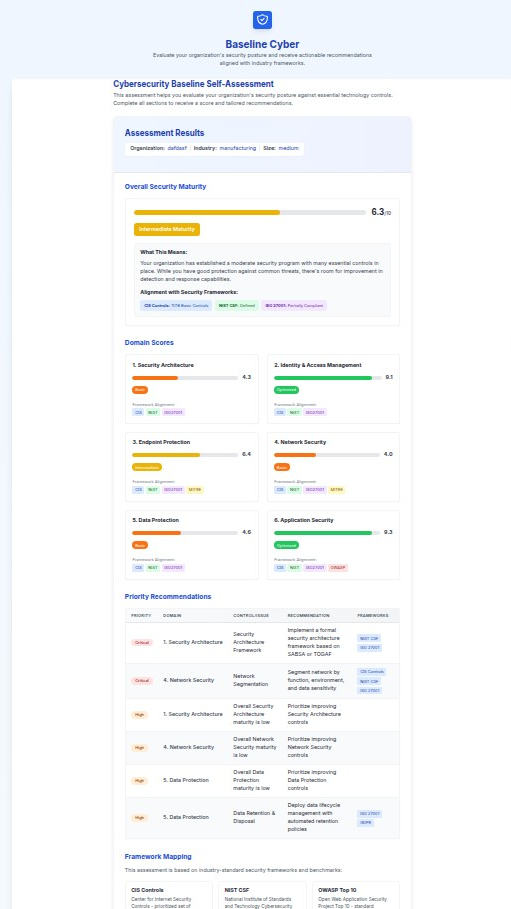
The baseline assessment typically covers seven core security domains:
1. Organization Information
Establishes the foundational context including organization size, industry vertical, and basic security program characteristics.
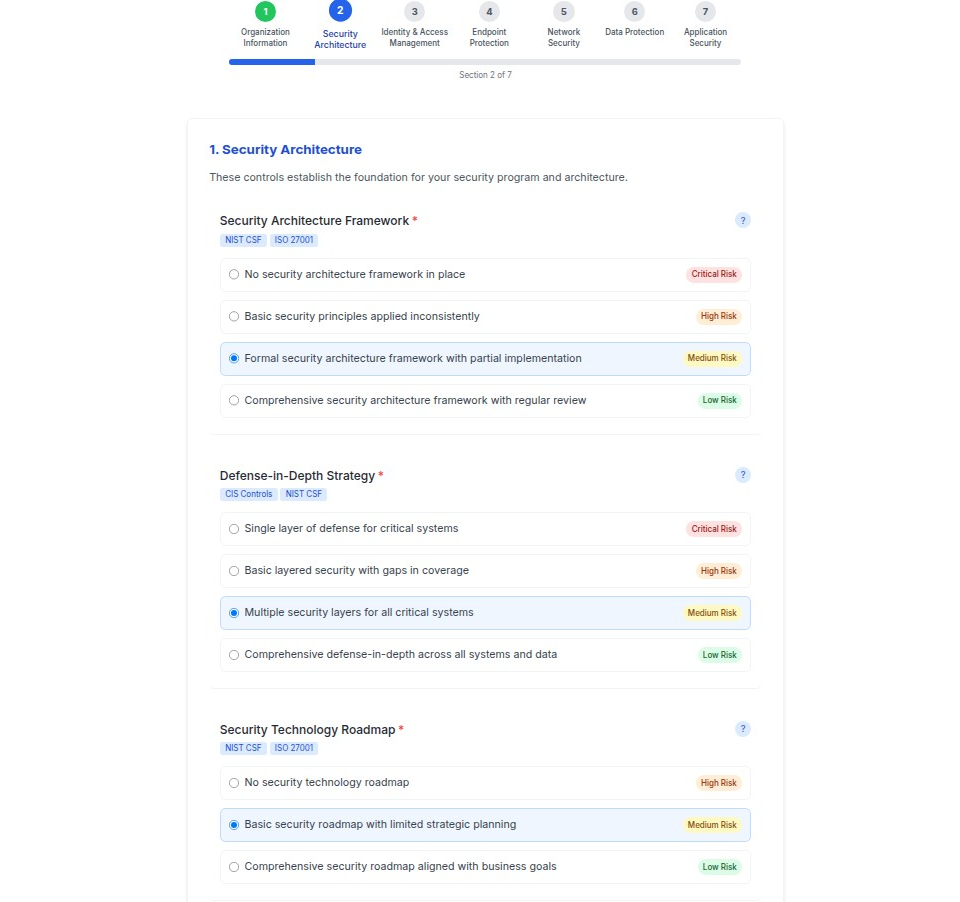
2. Security Architecture
Evaluates the fundamental security program structure and architecture, including:
- Security Architecture Framework: Ranges from no framework (Critical Risk) to comprehensive frameworks with regular review (Low Risk)
- Defense-in-Depth Strategy: Assesses layered security approaches from single-layer defense to comprehensive multi-system coverage
- Security Technology Roadmap: Reviews strategic planning from basic roadmaps to comprehensive business-aligned strategies
3. Identity & Access Management
Focuses on user authentication, authorization, and access controls across the organization.
4. Endpoint Protection
Examines security measures for computers, mobile devices, and other endpoints that connect to the network.
5. Network Security
Assesses network-level protections, monitoring, and segmentation strategies.
6. Data Protection
Reviews data classification, encryption, backup, and privacy protection measures.
7. Application Security
Evaluates security practices in software development and application deployment.
Maturity Scoring System
The assessment uses a 10-point maturity scale with the following classifications:
- Advanced (8.0-10.0): Comprehensive security program with regular optimization
- Intermediate (6.0-7.9): Moderate security program with essential controls in place
- Basic (4.0-5.9): Foundational security measures with significant gaps
- Critical (0.0-3.9): Minimal security controls requiring immediate attention
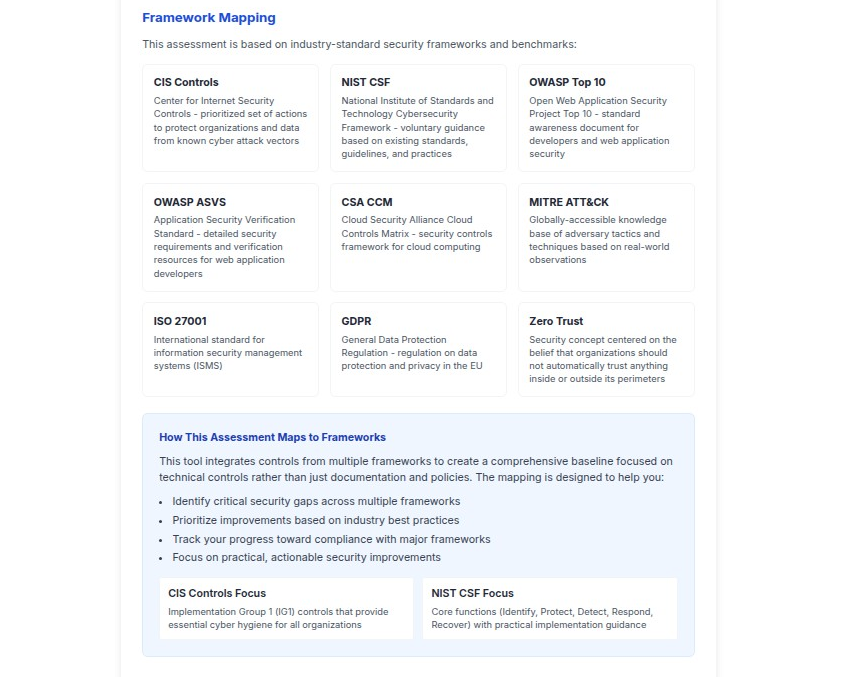
Framework Integration
The assessment integrates multiple industry-standard frameworks to provide comprehensive coverage:
Primary Frameworks
- CIS Controls: Center for Internet Security Controls for prioritized cyber defense actions
- NIST CSF: National Institute of Standards and Technology Cybersecurity Framework
- ISO 27001: International standard for information security management systems

Specialized Frameworks
- OWASP Top 10: Web application security awareness document
- OWASP ASVS: Application Security Verification Standard
- CSA CCM: Cloud Security Alliance Cloud Controls Matrix
- MITRE ATT&CK: Knowledge base of adversary tactics and techniques
- GDPR: General Data Protection Regulation compliance
- Zero Trust: Security concept emphasizing verification of all access requests
Assessment Benefits
Risk Identification
- Identifies critical security gaps across multiple frameworks
- Provides risk-based prioritization of security improvements
- Maps vulnerabilities to industry-standard control frameworks
Strategic Planning
- Enables data-driven security investment decisions
- Supports compliance planning and audit preparation
- Facilitates communication with stakeholders and executives
Continuous Improvement
- Establishes baseline measurements for progress tracking
- Supports regular reassessment and maturity advancement
- Enables benchmarking against industry standards
Implementation Recommendations
Preparation Phase
- Stakeholder Engagement: Involve key security, IT, and business stakeholders
- Documentation Review: Gather existing security policies, procedures, and documentation
- Resource Allocation: Ensure adequate time and personnel for thorough assessment
Assessment Execution
- Systematic Approach: Complete all assessment sections for comprehensive coverage
- Evidence-Based Responses: Base answers on documented evidence rather than aspirational goals
- Cross-Functional Input: Incorporate perspectives from multiple departments and roles
Post-Assessment Actions
- Priority Setting: Focus on high-impact, high-risk recommendations first
- Implementation Planning: Develop realistic timelines and resource requirements
- Regular Reassessment: Schedule periodic evaluations to track progress
Industry Applications
Healthcare Organizations
Healthcare entities benefit from assessment focus on:
- HIPAA compliance alignment
- Patient data protection measures
- Medical device security considerations
- Incident response for healthcare environments
Financial Services
Financial organizations should emphasize:
- Regulatory compliance (SOX, PCI DSS, etc.)
- Customer data protection
- Fraud prevention measures
- Business continuity planning
Manufacturing
Manufacturing companies should prioritize:
- Operational technology (OT) security
- Supply chain risk management
- Intellectual property protection
- Industrial control system security

Best Practices for Assessment Success
Accuracy and Honesty
- Provide realistic assessments of current capabilities
- Avoid overestimating security maturity
- Document assumptions and limitations
Comprehensive Coverage
- Address all assessment domains thoroughly
- Consider both technical and procedural controls
- Include third-party and vendor risk considerations
Action-Oriented Outcomes
- Focus on implementable recommendations
- Align improvements with business objectives
- Establish clear success metrics and timelines
Conclusion
A structured cybersecurity baseline assessment provides organizations with a clear understanding of their security posture and a roadmap for improvement. By leveraging industry-standard frameworks and following a systematic approach, organizations can enhance their cybersecurity maturity while ensuring alignment with regulatory requirements and business objectives.
Regular assessment and continuous improvement efforts help organizations stay ahead of evolving threats while building resilient security programs that protect critical assets and enable business success.







