Configuring an Information Security Program in Compliance with Global Privacy Laws
In today's interconnected digital world, businesses operate across borders, often serving customers in multiple countries. With the rise of stringent privacy regulations worldwide, it’s imperative for organizations to configure an information security program that not only meets their business needs but also complies with the various data protection laws in the regions they operate in or where their customers are located. This article explores the key considerations and steps for configuring an information security program that aligns with global privacy regulations.
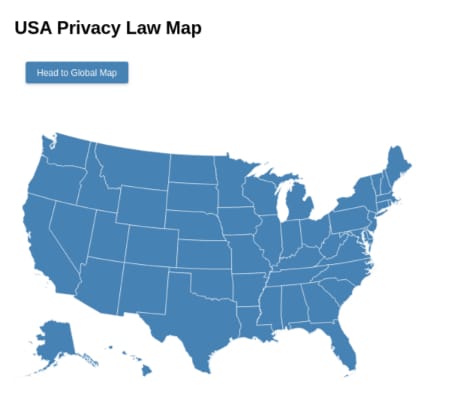
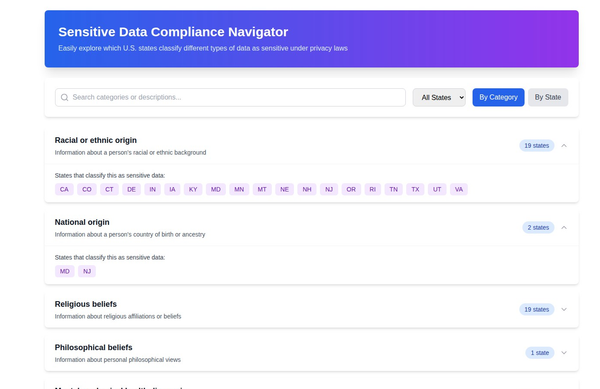
USA Compliance Map:

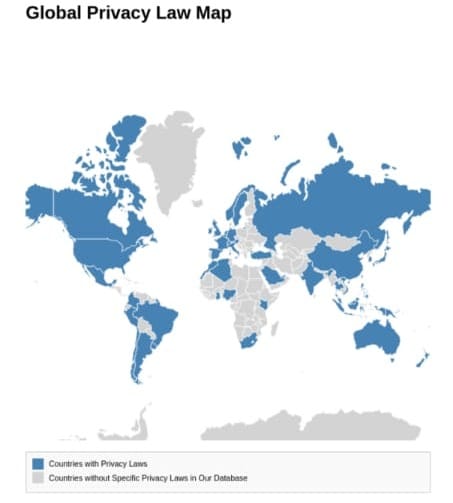
Global Compliance Map:

Understanding the Regulatory Landscape
Before configuring an information security program, businesses must first understand the global regulatory landscape. Privacy laws like the General Data Protection Regulation (GDPR) in the European Union, the California Consumer Privacy Act (CCPA) in the United States, and the Personal Information Protection Law (PIPL) in China, among others, set strict requirements on how personal data should be handled. These laws can vary significantly in terms of scope, rights granted to individuals, and obligations imposed on organizations.
Key Regulations to Consider:
- European Union: GDPR applies to any organization processing the personal data of EU residents, regardless of where the organization is located.
- United States: CCPA, along with various state-specific regulations such as Virginia's Consumer Data Protection Act (VCDPA) and New York's SHIELD Act, governs how businesses handle personal data.
- China: The PIPL imposes strict requirements on data handling, with particular emphasis on data localization and cross-border data transfers.
- Brazil: The General Data Protection Law (LGPD) closely mirrors the GDPR and applies to businesses processing the data of Brazilian residents.
- Australia: The Privacy Act 1988 outlines data protection obligations for organizations operating in Australia.
- Other Countries: Regulations such as the Personal Data Protection Act (PDPA) in Singapore, the Data Protection Act in the United Kingdom, and various other laws across Asia, Africa, and the Middle East, each bring unique compliance challenges.
Step-by-Step Approach to Configuring an Information Security Program
- Assess Regulatory Requirements:
- Begin by conducting a thorough assessment of the privacy laws that apply to your organization. This includes understanding the specific requirements of each regulation based on where your business operates and where your customers are located.
- Identify the key legal obligations such as data subject rights, data breach notification requirements, data localization mandates, and cross-border data transfer restrictions.
- Map Data Flows:
- Create a comprehensive data flow map that details how personal data is collected, processed, stored, and transferred within your organization.
- This map should include both internal processes and external data transfers to third-party service providers or international locations.
- Understanding your data flows is critical for identifying compliance risks and implementing appropriate safeguards.
- Implement Data Protection Principles:
- Adopt the core principles of data protection, such as data minimization, purpose limitation, and data accuracy, across your information security program.
- Ensure that personal data is only collected and processed for legitimate purposes and that it is kept accurate and up-to-date.
- Implement data retention policies that align with the regulatory requirements of each jurisdiction, ensuring data is deleted when no longer needed.
- Develop and Implement Security Controls:
- Based on your regulatory assessment and data flow mapping, implement technical and organizational security measures to protect personal data.
- Security controls should include encryption, access controls, data masking, and regular security audits to mitigate risks of unauthorized access or data breaches.
- Consider adopting industry-standard frameworks like ISO/IEC 27001 for Information Security Management Systems (ISMS) to ensure a structured approach to managing sensitive data.
- Cross-Border Data Transfers:
- For businesses that transfer personal data across borders, ensure compliance with the data transfer requirements of each applicable regulation.
- For instance, the GDPR imposes strict conditions on transferring personal data outside the European Economic Area (EEA), which may require implementing Standard Contractual Clauses (SCCs) or obtaining explicit consent from data subjects.
- Similar requirements exist under laws like the PIPL in China, which may require data localization or security assessments before cross-border transfers.
- Establish a Data Breach Response Plan:
- Develop a comprehensive data breach response plan that complies with the notification requirements of each applicable regulation.
- The plan should outline the steps to be taken in the event of a data breach, including immediate containment, investigation, and notification to affected individuals and relevant authorities.
- Conduct regular breach response drills to ensure your team is prepared to act swiftly in the event of a breach.
- Employee Training and Awareness:
- Regularly train your employees on data protection principles and the specific regulatory requirements relevant to their roles.
- Ensure that employees understand the importance of data privacy and security and are aware of their responsibilities in protecting personal data.
- Create a culture of privacy within your organization by integrating data protection practices into everyday business processes.
- Engage with Third-Party Vendors:
- When engaging with third-party vendors who process personal data on your behalf, ensure they comply with relevant privacy regulations.
- Include data protection clauses in contracts with vendors and conduct regular audits to assess their compliance.
- Consider using Data Processing Agreements (DPAs) to outline the responsibilities of each party in protecting personal data.
- Monitor and Review Compliance:
- Continuously monitor your information security program to ensure ongoing compliance with evolving privacy laws.
- Implement regular compliance audits and assessments to identify any gaps or areas for improvement.
- Stay informed about updates to global privacy laws and adjust your security measures and policies accordingly.
- Leverage Technology for Compliance:
- Utilize technology solutions such as Data Loss Prevention (DLP) tools, Security Information and Event Management (SIEM) systems, and Privacy Information Management Systems (PIMS) to automate compliance processes.
- Consider using AI-driven tools to monitor data usage, detect anomalies, and ensure compliance with data protection requirements in real time.
Adapting to a Global Privacy Landscape
As privacy regulations continue to evolve, businesses must remain agile and adaptive in their approach to information security. By understanding the regulatory landscape, mapping data flows, and implementing robust security controls, organizations can configure an information security program that not only complies with global privacy laws but also builds trust with customers and stakeholders.
Moreover, by fostering a culture of privacy and leveraging technology, businesses can stay ahead of regulatory changes and ensure the protection of personal data, regardless of where they or their customers are located. In a world where data is a critical asset, a well-configured information security program is not just a regulatory requirement—it's a business imperative.