Compliance Report: Procedures for NIST SP 800-171 and CMMC Assessment Submission in the Supplier Performance Risk System (SPRS)
1.0 Introduction: The DoD Cybersecurity Compliance Mandate
The Department of Defense (DoD) has formalized cybersecurity accountability for its supply chain through the Defense Federal Acquisition Regulation Supplement (DFARS) and the Cybersecurity Maturity Model Certification (CMMC) program. This regulatory framework establishes that robust cybersecurity is no longer a best practice but a mandatory condition for contract awards. Defense contractors who process, store, or transmit sensitive government information are now required to demonstrate compliance through a structured, verifiable assessment process.
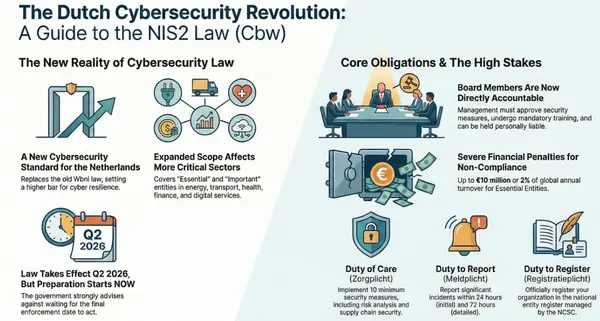
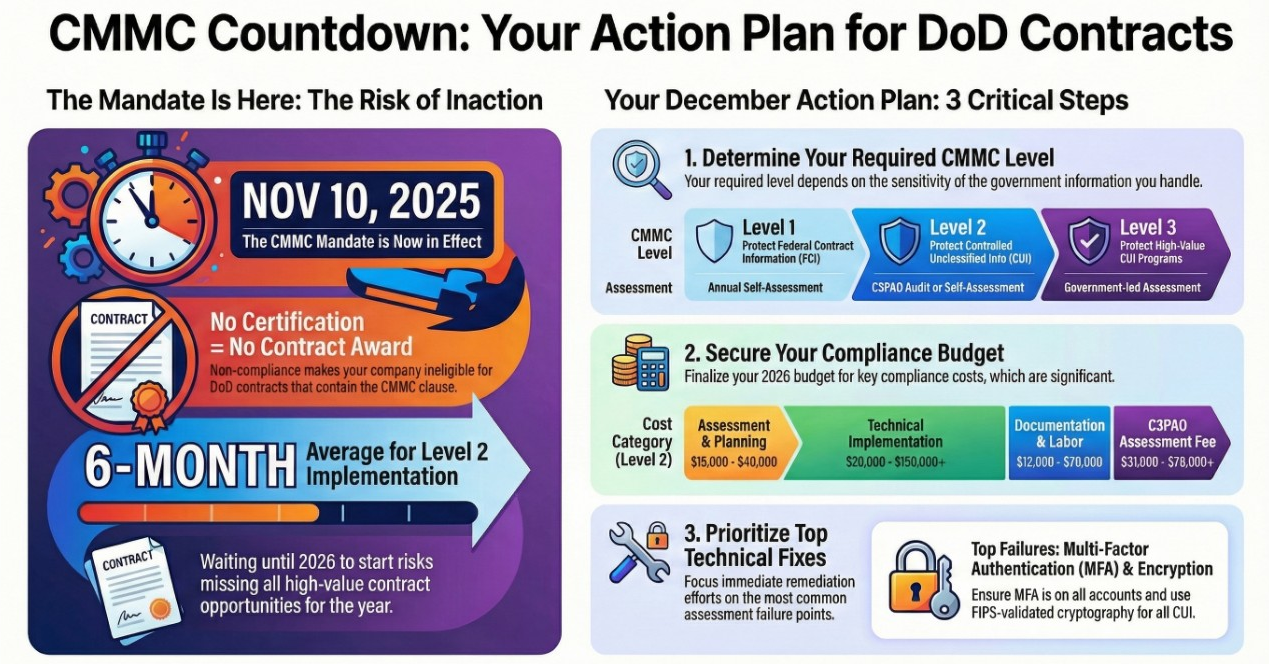
The CMMC Final Rule takes effect on November 10, 2025. This date represents a critical threshold, marking the point when the CMMC clause at DFARS 252.204-7021 will begin to appear in new DoD solicitations. This shift makes adherence to specified cybersecurity standards a direct and immediate factor in contract eligibility, rendering non-compliant organizations unable to secure new defense contracts issued after this date.
The purpose of this document is to serve as a formal guide for internal review and strategic planning. It details the procedural requirements for submitting and maintaining cybersecurity assessments in the Supplier Performance Risk System (SPRS), which the DoD has designated as its single, authorized application for this compliance data. To effectively navigate these procedures, it is essential to first understand the structure of the CMMC framework itself.
2.0 The CMMC 2.0 Framework and Required Tiers of Compliance
The CMMC 2.0 framework is a tiered model designed to assess a contractor's cybersecurity maturity based on the sensitivity of the information they handle: Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). The program does not create new security standards for protecting CUI; rather, it provides a formal assessment and verification mechanism for the existing 110 security controls detailed in NIST SP 800-171 Rev. 2. A contractor's required CMMC level is specified in the solicitation and dictates the scope of requirements and the type of assessment needed to prove compliance.
CMMC 2.0 Compliance Levels
Level | Information Protected & NIST Alignment | Assessment & Affirmation Requirements |
Level 1 | Federal Contract Information (FCI)<br>Aligns with the 15 basic safeguarding requirements from FAR 52.204-21. | Annual Self-Assessment and affirmation of compliance in SPRS. No Plan of Actions and Milestones (POA&Ms) are permitted; full compliance is required. |
Level 2 | Controlled Unclassified Information (CUI)<br>Aligns with all 110 security requirements from NIST SP 800-171 Rev. 2. | Triennial Assessment (every 3 years). The assessment type is contract-specific and will be either a Self-Assessment or a formal C3PAO Assessment. POA&Ms are allowed for certain controls but must be closed within 180 days. |
Level 3 | CUI for High-Value Programs<br>Aligns with all 110 requirements of NIST SP 800-171 plus 24 enhanced requirements from NIST SP 800-172. | Triennial Government-Led Certification Assessment conducted by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). |
The DoD is implementing CMMC requirements through a phased, multi-year timeline, giving contracting officers discretion in applying the clauses to new solicitations. Phase 1 begins on November 10, 2025, and Phase 4, which marks full implementation, begins on November 10, 2028. This phased approach allows the industry time to prepare but underscores the urgency for organizations to understand the distinct pathways for achieving and reporting their compliance status.

3.0 Assessment Pathways and Foundational Requirements
Before any submission to SPRS can occur, an organization must undergo a specific type of assessment as dictated by its contractual obligations. While the DoD previously required contractors handling CUI to conduct a NIST SP 800-171 self-assessment, the CMMC program formalizes this process with distinct verification pathways tied to the sensitivity of the information involved.
The following assessment types are available to contractors:
- NIST SP 800-171 Basic Assessment: This is the foundational self-assessment required under DFARS 252.204-7019/7020. Contractors must conduct a self-evaluation against the NIST SP 800-171 controls, calculate a score based on the DoD Assessment Methodology, and post that score to SPRS.
- CMMC Level 1 Self-Assessment: This is an annual requirement for organizations that handle only FCI. The organization must conduct a self-assessment and affirm that all 15 basic safeguarding requirements from FAR 52.204-21 are met.
- CMMC Level 2 Self-Assessment: For certain contracts involving non-critical CUI, contractors may be permitted to conduct a triennial self-assessment. This requires a comprehensive self-evaluation against all 110 controls in NIST SP 800-171.
- CMMC Level 2 Certification Assessment: Required for contracts involving more sensitive CUI, this is a formal audit conducted by an accredited CMMC Third-Party Assessment Organization (C3PAO). The C3PAO verifies the contractor's implementation of the 110 NIST SP 800-171 controls.
- CMMC Level 3 Certification Assessment: This is the highest level of assessment, reserved for contractors supporting the most sensitive DoD programs. It is a government-led assessment conducted by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
Regardless of the assessment type performed, the results must be formally entered, affirmed, and maintained within the Supplier Performance Risk System to ensure contract eligibility.
4.0 Procedural Guide for SPRS Submissions and Affirmations
The Supplier Performance Risk System (SPRS) is the DoD's central repository for all contractor cybersecurity compliance data. Proper registration and the accurate, timely entry of assessment results are critical prerequisites for contract eligibility. This section provides the step-by-step procedures for fulfilling these requirements, based directly on the official SPRS Software User's Guide.