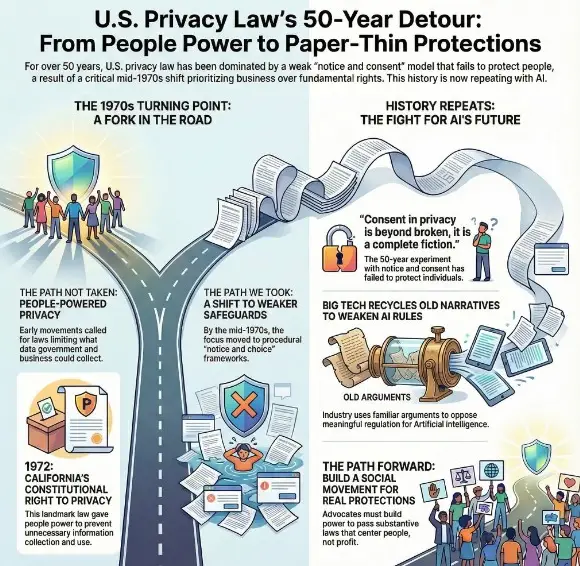
CCO's Holiday Compliance Crisis 2025: Managing 72-Hour Breach Notifications, 61% Third-Party Risk, and 8 State Privacy Laws Mid-Season

It's November 15, 2025. Thanksgiving is next week. Black Friday is 12 days away. And if you're a Chief Compliance Officer or Data Protection Officer, you're already behind.
The holiday shopping season doesn't wait for compliance readiness. While your security team battles a 692% surge in phishing attacks and your seasonal workforce processes millions of transactions without proper training, you're sitting on a regulatory powder keg that could detonate at any moment.
Here's the uncomfortable reality: 61% of companies experienced third-party vendor data breaches over the past year—a 49% increase from 2023. When (not if) a breach occurs during peak shopping season, you have 72 hours under GDPR to notify authorities, face potential fines of €20 million or 4% of global annual revenue, and navigate eight different state privacy laws now in force across the United States—each with its own notification requirements, cure periods, and penalty structures.
And that's assuming you even discover the breach within 72 hours. During the 2024 holiday season, the average time to detect a breach was 207 days. By then, your notification windows have long since closed, your regulatory violations have compounded, and your penalties have multiplied.

This isn't a drill. This is your operational reality. The question isn't whether your organization will face compliance challenges this holiday season—it's whether you'll be ready when they arrive.
The Compliance Landscape: What Changed While You Were Planning
Eight State Privacy Laws Now in Force
As of November 2025, eight comprehensive state privacy laws are actively enforced across the United States:
| State | Law | Effective Date | Enforcement Authority | Penalty per Violation | Cure Period |
|---|---|---|---|---|---|
| California | CCPA/CPRA | Jan 1, 2020 / Jan 1, 2023 | CPPA + AG | $7,500 (intentional) / $2,500 (unintentional) | 30 days (sunsets 2025) |
| Virginia | VCDPA | Jan 1, 2023 | AG | $7,500 | 30 days |
| Colorado | CPA | Jul 1, 2023 | AG | $20,000 | 60 days (expires 2025) |
| Connecticut | CTDPA | Jul 1, 2023 | AG | $5,000 | 60 days (expires 2025) |
| Utah | UCPA | Dec 31, 2023 | AG | $7,500 | 30 days (expires 2026) |
| Texas | TDPSA | Jul 1, 2024 | AG | $7,500 | 30 days (perpetual) |
| Oregon | OCPA | Jul 1, 2024 | AG | $7,500 | 30 days |
| Montana | MCDPA | Oct 1, 2024 | AG | No cap specified | 60 days (expires Apr 1, 2026) |
Critical insight: Montana's law doesn't specify penalty caps, giving the Montana Attorney General discretion to impose higher fines than any other state.
The Texas Enforcement Machine
On June 4, 2024, just ahead of the Texas Data Privacy and Security Act (TDPSA) effective date, the Texas Attorney General's office announced it will establish a dedicated enforcement team for privacy issues within its Consumer Protection Division.
Their enforcement priorities include:
- Texas Data Privacy and Security Act
- Texas data broker regulations
- Biometric privacy laws
- Data breach notification laws
- Unfair and deceptive trade practice laws
- Federal privacy laws (HIPAA, COPPA)
Unlike other state privacy laws, Texas's 30-day cure period will not sunset but rather continue in perpetuity. This means every violation gives you 30 days to cure before facing $7,500 per violation fines—but those fines can accumulate quickly across millions of customer records.
The Montana Wild Card
The Montana Consumer Data Privacy Act (MCDPA) presents the most significant financial risk for non-compliance. While other states cap penalties at $7,500 to $20,000 per violation, Montana imposes no cap on monetary penalties.
This gives the Montana Attorney General unprecedented discretion to impose fines that could exceed any other state's enforcement actions. For a retail breach affecting thousands of Montana residents during the holiday season, the potential liability is virtually unlimited.
California's CPPA Enforcement Ramp-Up
The California Privacy Protection Agency (CPPA) released its first-ever enforcement advisory in April 2024, focusing on CCPA data minimization obligations tied to consumer requests.
Privacy-related enforcement and compliance activities picked up in 2025 across states, especially in California and Texas. Regulators are still feeling out how best to enforce their states' laws, but they are learning quickly—and with more and more state privacy laws coming into effect, enforcement is not going to slow down anytime soon.
The 72-Hour Nightmare: Breach Notification Requirements
GDPR: The 72-Hour Countdown
Under GDPR Article 33, organizations must notify their relevant supervisory authority within 72 hours of discovering a breach likely to result in risk to individuals.
Key requirements:
- 72-hour deadline from discovery (not occurrence) of the breach
- Notification must include:
- Nature of the personal data breach
- Categories and approximate number of data subjects affected
- Categories and approximate number of personal data records affected
- Name and contact details of the Data Protection Officer
- Description of likely consequences of the breach
- Measures taken or proposed to address the breach
Penalties for late or failed notification:
- €10 million or 2% of annual global revenue for notification failures
- €20 million or 4% of annual global revenue for the underlying breach (whichever is higher)
The holiday challenge: Discovering a breach within 72 hours requires 24/7 monitoring and alert capabilities. During Thanksgiving weekend, when 9 in 10 ransomware attacks occur during off-hours, your detection window may close before anyone is even in the office.

CCPA/CPRA: California's Dual Notification System
California requires two separate notifications for data breaches:
1. Consumer Notification:
- "Without unreasonable delay" after discovery
- Required when breach involves unencrypted or unredacted personal data
- Must be written in plain language
- Must be titled "Notice of Data Breach"
- Must include name and contact information of reporting organization
2. Attorney General Notification:
- Required if breach affects more than 500 California residents
- Must be submitted electronically
- Deadline: Generally at the same time as consumer notification but subject to law enforcement delay requests
Penalties:
- $2,500 per unintentional violation
- $7,500 per intentional violation
- Private right of action: $100-$750 per consumer per incident for data breaches
Real-world impact: For a breach affecting 10,000 California residents discovered during Black Friday weekend, you're looking at potential penalties of $25 million (10,000 × $2,500) for unintentional violations, plus private lawsuits seeking up to $7.5 million (10,000 × $750).
State Breach Notification Laws: The Patchwork Compliance Problem
All 50 states, the District of Columbia, Puerto Rico, and the Virgin Islands have enacted data breach notification laws. However, requirements vary significantly:
Timeline variations:
- Most states: "Without unreasonable delay" or "most expedient time possible"
- Florida: Within 30 days (with 15-day extension if requested)
- Colorado: Without unreasonable delay but no later than 30 days
- Maryland: Without unreasonable delay (typically interpreted as 10-14 days)
Attorney General notification requirements:
- New York: Must notify AG if more than 500 residents affected
- California: 500+ residents (as noted above)
- Vermont: Must notify AG if breach affects Vermont residents
- Many states: AG notification required alongside consumer notification
Penalties for late notification:
| State | Maximum Penalty |
|---|---|
| California | $7,500 per intentional violation |
| New York | $150,000 for failure to notify within 72 hours (DFS entities) |
| Oklahoma | Up to $10,000/day after 90 days of non-compliance |
| Michigan | Up to $750,000 for multiple violations |
| Texas | $7,500 per violation |
The compliance nightmare: A breach affecting customers in all 50 states requires simultaneous compliance with 50+ different notification laws, each with different deadlines, content requirements, and delivery methods.
The Delayed Notification Penalty Multiplier
2024 enforcement actions demonstrate that regulators are increasingly penalizing late notifications separately from the underlying breach:
- New York Department of Financial Services: $2 million fine in August 2024 for failure to notify within 72 hours of a cybersecurity event, among other compliance issues
- California Attorney General: $6.75 million fine for "misleading the public of the full impact of the data breach"
- GDPR violations: Fines as high as €10 million for notification deadline failures
The multiplication effect: You can face penalties for both the breach itself AND the notification failure, effectively doubling your regulatory exposure.
The Third-Party Vendor Time Bomb
The 61% Reality
61% of companies experienced third-party vendor data breaches over the past year—a 49% increase from 2023 and three times higher than in 2021.
At least 35.5% of all data breaches in 2024 originated from third-party compromises, up 6.5% from 2023. The 2024 Verizon Data Breach Investigations Report (DBIR) found that "supply chain breaches made up 15% of breaches this year, a 68% jump compared with last year."
Holiday-specific risk: Third-party vendors experience the same resource constraints your organization does—reduced staffing, increased transaction volumes, stretched security teams. This makes them more vulnerable during the holiday season, precisely when your dependence on them is highest.
You're Liable for Their Failures
Under GDPR, CCPA, and most state privacy laws, organizations are legally responsible for protecting personal data even when handled by third parties.
Critical compliance principle: When your payroll vendor, payment processor, or e-commerce platform experiences a breach, YOU are still responsible for notification and compliance—regardless of whether the breach occurred in your systems.
Real-world example: When a payroll vendor experienced a breach in early 2024, multiple clients were held jointly liable for failing to ensure vendor data controls were adequate. The resulting settlements and fines totaled over $60 million.
Major Third-Party Breaches in 2024
Toyota: A cybercriminal group hacked into an undisclosed third-party supplier, leaking 240GB of sensitive data. Toyota faced regulatory scrutiny in multiple jurisdictions despite the breach occurring at a vendor.
National Public Data: Hackers targeted NPD through a third-party contractor who failed to update security patches, reportedly affecting 2.9 billion people. The scale of this breach triggered notification requirements across every privacy jurisdiction globally.
Bank of America: Customer data was compromised through an Infosys McCamish cybersecurity incident affecting approximately 6.5 million individuals. Bank of America was required to handle notifications and face regulatory consequences despite not being the breached entity.
Your Vendor Contract May Not Protect You
Most organizations have broad indemnification language in third-party vendor agreements, holding the vendor responsible for costs and liability arising from vendor data breaches.
However:
- Indemnification doesn't prevent regulatory penalties against your organization
- Many vendors have liability caps that cover only a fraction of actual breach costs
- Indemnification requires litigation to enforce, which takes months or years
- You still face the regulatory notification deadlines while legal proceedings drag on
The compliance gap: Your vendor contract says they're responsible. Regulators say you're responsible. Guess who the regulators will fine first?
The Holiday Vendor Risk Assessment
Questions every CCO/DPO must answer before Thanksgiving:
- Do you have a complete inventory of all third-party vendors with access to personal data?
- Have you conducted security assessments of critical vendors within the past 12 months?
- Do your vendor contracts include specific incident notification timelines (e.g., vendor must notify you within 24 hours of discovering a breach)?
- Can you meet regulatory deadlines if you don't learn about a vendor breach until days after it occurs?
- Do you have redundancy for critical vendors if one experiences an outage or breach?
If you answered "no" to any of these questions, you have a compliance gap that could explode during the holiday season.
PCI DSS 4.0.1: The Payment Compliance Mandate
The March 31, 2024 Deadline Has Passed
PCI DSS 4.0.1 became mandatory on March 31, 2024, replacing the older 3.2.1 standard. Organizations that are not yet compliant are already in violation and subject to escalating monthly penalties.
Additional future-dated requirements will become fully enforced by March 31, 2025—just four months away.
The Holiday Transaction Volume Problem
During the holiday season, payment transaction volumes can increase 300-500% compared to normal periods. This creates compliance challenges:
Increased attack surface: More transactions = more opportunities for payment data compromise
Scalability testing: Are your PCI-compliant systems tested for Black Friday/Cyber Monday transaction volumes?
Temporary systems: Any emergency capacity additions must also be PCI DSS compliant
Third-party processors: Increased use of payment processing vendors (see third-party risk above)
PCI DSS Non-Compliance Penalty Structure
Monthly penalties for non-compliance:
| Time Period | Monthly Fee |
|---|---|
| Months 1-3 | $5,000 - $10,000 |
| Months 4-6 | $25,000 - $50,000 |
| Month 7+ | $50,000 - $100,000 |
For organizations not compliant as of March 31, 2024, you're already in the $25,000-$50,000/month penalty range.
In the event of a data breach, serious breaches typically incur $50-$90 per affected customer. For a holiday season breach affecting 100,000 customers, that's $5-9 million in PCI penalties alone—before regulatory fines from privacy laws.
The Target Precedent
In 2013, hackers stole data from up to 40 million credit and debit cards of shoppers who visited Target stores during the holiday season.
Total costs of PCI non-compliance: $292 million reported in their 2016 annual financial report.
This included:
- Payment card company fines
- Customer compensation
- Credit monitoring services
- Regulatory penalties
- Legal settlements
- Reputation damage and lost revenue
The Target breach occurred during the holidays for a reason—attackers knew security would be stretched and detection would be delayed.
Key PCI DSS 4.0.1 Changes for Retail
Targeted Risk Analysis: Organizations must now conduct targeted risk analyses for certain requirements, documenting how they implement controls based on their specific environment.
Customized Implementation: More flexibility in how controls are implemented, but requires documentation of why specific approaches were chosen.
Multi-Factor Authentication (MFA): Expanded MFA requirements for all access to the cardholder data environment.
Future-dated requirements (by March 31, 2025):
- Enhanced authentication mechanisms
- Additional encryption requirements
- Improved logging and monitoring
Compliance action: If you're not yet compliant with PCI DSS 4.0.1, you're accumulating penalties every month—and the holiday season dramatically increases your breach risk while non-compliant.
FTC Enforcement: The $137 Million in Penalties
2024 Enforcement Priorities
The FTC has remained focused on financial services, web services and telecommunications, health care, and retail industries, with approximately 90% of its consumer protection actions in these areas.