5 Alarming Truths About the War on Your Digital Privacy in 2026
Introduction: Caught in the Digital Crossfire
There's a growing, unspoken anxiety that defines our digital lives. We rely on technology for everything from our most intimate conversations to our most critical infrastructure, yet we feel increasingly powerless to protect it. We are caught in a digital crossfire. On one side, governments propose ever-more-intrusive surveillance measures in the name of safety. On the other, sophisticated cybercriminals weaponize the very systems we depend on. The paradox is that as both states and criminals fix their sights on the digital world, the ordinary citizen is left more exposed than ever.
The alarming truth is that the tactics of state surveillance and cybercrime are no longer just separate threats; they are evolving in surprisingly parallel ways. Their methods are converging on a single point of pressure: the individual's expectation of privacy. Whether through a legislative mandate or a malware-free attack, the result is the same—our private digital spaces are being rendered transparent and controllable. Understanding these convergent trends is the first step toward reclaiming our digital future.
--------------------------------------------------------------------------------
1. Encryption Is Now the Central Battlefield for Everyone
The central, counter-intuitive struggle of our time is this: European lawmakers and sophisticated ransomware gangs are both locked in a battle to control or bypass encryption. They see it as the ultimate strategic asset, the one lock that must be broken or co-opted for them to achieve their goals.
The Legislative Attack on Encryption
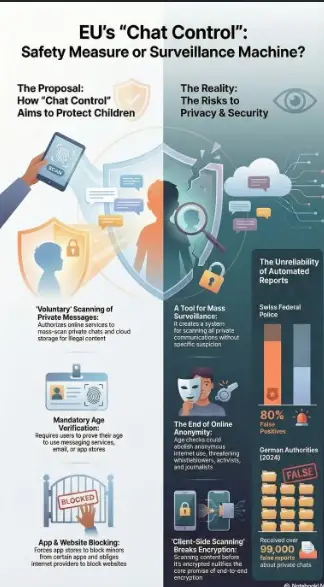
The EU's "Chat Control" regulation, officially aimed at preventing child sexual abuse, poses a fundamental threat to end-to-end encryption (E2EE). While recent proposals have removed language mandating the breaking of E2EE, they have introduced a far more subtle threat: "client-side scanning" (CSS).
This technique involves scanning the content of a message—text, images, or videos—on a user's device before it is encrypted and sent. Proponents argue this doesn't "break" encryption, but security experts and digital rights advocates are clear: this technicality completely nullifies the purpose of E2EE. It violates the core promise of confidential communication. As the Internet Society explains in a powerful analogy:

Breaking encryption is like tampering with an envelope while it transits through a post office. Client-side scanning is like reading the letter as it is being written. In client-side scanning, the envelope is not tampered with, but the result is the same–the confidentiality agreement is violated.
This approach is profoundly dangerous because it creates a "single point of failure." A system designed for mass scanning can be reconfigured to search for anything, creating a vulnerability that undermines the security relied upon by everyone from activists and journalists to politicians and military forces.
The Systemic Weaponization of Encryption
While governments work to legislate around encryption, criminals are evolving to weaponize it. The threat actor known as "Codefinger" exemplifies this shift. Instead of deploying traditional malware, Codefinger attacks abuse a victim's own legitimate cloud encryption tools to lock them out of their data.
Their method targets AWS cloud infrastructure. They compromise a company's credentials and then use AWS's own Server-Side Encryption features to encrypt all of the victim's data. They then rewrite access policies to block the rightful owners from their own files. This new method is insidious because it generates no malware alerts and appears as legitimate administrative activity. It proves that criminals are moving from trying to break encryption to weaponizing the very systems that provide it.
2. The "Official Story" Hides the Real Goal
The stated justifications for both government surveillance and ransomware attacks are becoming increasingly misleading, masking deeper and more alarming motives.
The ‘Child Safety’ Pretext for Mass Surveillance
The official purpose of the Chat Control regulation is to prevent and combat child sexual abuse material (CSAM). While this is a noble goal, there is widespread criticism that it is being used as a pretext for establishing an infrastructure of mass surveillance, with online commentators noting that the "Think of the children" slogan is a familiar tactic to "push a shitty law."
The hypocrisy of the proposal reveals its true target. Leaked details show that government and military communications would be exempt from this privacy invasion. This suggests that the real objective is not universal safety, but the monitoring of the general citizenry. The legal services of the EU itself and the German government’s own lawyers have raised serious doubts about the proposal's legality, confirming in internal memos that they believe it violates fundamental rights and is unlikely to survive a court challenge.
The ‘Ransom’ Pretext for Business Destruction
The ransomware economy is no longer primarily about getting paid to decrypt files. Data shows that 76% of all ransomware attacks now involve exfiltrating—or stealing—data before any files are encrypted.
This marks a shift into what researchers call "Third-Wave Extortion," where the primary goal is intentional and catastrophic business disruption. The encryption of files is just one tool in a much larger arsenal. Attackers now routinely wipe backups, launch Distributed Denial-of-Service (DDoS) attacks, publicly harass customers and partners, and report their victims to regulators to trigger compliance penalties. This strategy aims to make non-payment so costly that a ransom seems like the lesser evil. As one ransomware operator bluntly stated to researchers:
"Backups are worthless if we destroy your reputation and regulatory standing first."
3. The Threat Is Shifting from Direct Mandates to Subtle Manipulation
Both governments and criminals are moving away from brute-force methods. The new playbook favors more subtle, systemic forms of control and attack that are harder to detect, harder to fight, and ultimately more dangerous.
Coercion Through ‘Voluntary’ Compliance
After massive public outcry, mandatory scanning of encrypted messages was removed from the Chat Control proposal. However, it was replaced by two concerning systems: "voluntary" detection and "risk mitigation."
This framework is not truly voluntary. If a service provider refuses to "volunteer" to scan user content, regulators can designate them as "high risk," which then triggers mandatory risk mitigation requirements. As digital rights experts have pointed out, an activity is "no longer voluntary if it forms part of a formal risk management obligation." This creates a powerful backdoor for surveillance by pressuring companies to monitor their users to avoid being targeted with punitive regulation.
This shift from overt force to systemic pressure has a direct parallel in the criminal world, where attackers have also abandoned noisy, brute-force methods in favor of attacks that manipulate the system from within.
Infiltration Through Trusted Systems
The Codefinger ransomware technique is the prime example of this criminal shift toward systemic attacks. Instead of deploying malicious code, the attack manipulates the fundamental administrative fabric of the cloud. The process is chillingly simple:
- Compromise a company's AWS credentials.
- Use the victim's own tools to encrypt their S3 data objects.
- Replace the victim's Identity and Access Management (IAM) policies to revoke their access.
- Set short data deletion policies to create extreme urgency and pressure for payment.
This is a game-changer because it completely subverts traditional security defenses that are designed to look for malicious software. The attack doesn't come from a virus; it comes from the misuse of the system's own trusted functions.
4. The Collateral Damage Is Hitting Everyday Citizens
As these digital threats evolve, the consequences are being felt most acutely by innocent people and public safety systems. This collateral damage manifests in two distinct but related ways: the direct, personal harm caused by flawed surveillance and the systemic, societal harm caused by attacks on the infrastructure we all depend on. Both chip away at the public's sense of safety and trust in the digital world.
The High Price of False Positives
The AI technology proposed for scanning messages is notoriously unreliable and prone to massive error rates. The statistics are stark: Swiss federal police report that 80% of machine-generated reports about suspicious content turn out to be false positives, and in 2024 alone, German authorities received over 99,000 false reports about private chats and photos.
The human cost of these errors is immense. Innocent people face traumatic criminal investigations for sharing perfectly legal content, such as "family beach photos," that an error-prone algorithm incorrectly flagged as suspicious.
When Critical Infrastructure Becomes the Target
Ransomware groups have systematically shifted their focus toward critical sectors like healthcare, manufacturing, and emergency services—targets with the lowest tolerance for downtime. The group "INC Ransom" has become infamous for intentionally targeting sectors that other criminal syndicates previously considered "off-limits."
Their attack on Jackson County's emergency warning systems is a sobering example of the real-world danger. The attack left communities unable to send critical notifications—such as weather alerts or public safety warnings—for two weeks. It represents one of the most serious attacks on public safety infrastructure in U.S. history.
5. The Battlefield Is Fragmenting into More Dangerous Pieces
Paradoxically, as major players in both government and crime are disrupted, the overall threat landscape is becoming more chaotic, complex, and dangerous—not safer.
The Divided EU Response
The push for Chat Control is far from unified, revealing deep divisions within the EU. The Council's negotiating mandate was adopted without the support of key countries, including Italy, Poland, the Netherlands, the Czech Republic, and Estonia.
In a surprising twist, the new EU Home Affairs Commissioner, Magnus Brunner, has sided with the more rights-protecting European Parliament position over the more surveillance-heavy position of the EU governments (the Council). This split shows that the top-down push for mass surveillance is fragile and contested, leading to an unpredictable and chaotic legislative process.
The Ransomware Power Vacuum
Law enforcement actions against massive ransomware syndicates like LockBit did not end the problem. Instead, they shattered the ecosystem, creating a power vacuum filled by smaller, more aggressive, and more numerous groups.
The data is clear: 96 unique ransomware groups operated in the first half of 2025, a 41.18% increase over 2024. The disruption of old giants led to the rapid rise of new dominant players like Qilin, which carried out 81 attacks in June 2025 alone, and a surge from others like DragonForce. The criminal landscape is now more competitive, dynamic, and unpredictable than ever before.
--------------------------------------------------------------------------------
Conclusion: Reclaiming Our Digital Future
The war on our digital privacy is being fought on parallel fronts. State actors, driven by a desire for control, are pushing surveillance measures that weaken the very security that protects us. At the same time, cybercriminals are evolving from simple extortionists into systemic saboteurs who weaponize the infrastructure of our digital world. Encryption, anonymity, and trust are the casualties caught in the middle. The lines are blurring, the justifications are facades, and the collateral damage is mounting for ordinary citizens.
When the state's tools for control and the criminal's tools for chaos begin to look the same, how do citizens build a future that is safe from both?






